We often write about very clear cut cases of malware activity. The attacker is leveraging your traffic, redirecting it to other locations, or injecting things like iFrames in an attempt to perform some type of drive-by-download. These are obviously very clear cut cases of malware and nefarious activities. But what about others?
By others I mean abusing system resources. This can be done through bot networks, spam emails and even using your box as a proxy. None of these are things you’ll ever pick up via any remote scanner as they never present themselves remotely. It’s also why we have to start evolving our ideals and remediation to move beyond the application tier and focus on the web server.
A perfect example is what we came across today.
In this example the attacker has injected a file called gate.php, when you navigate to via your URI you come see this:
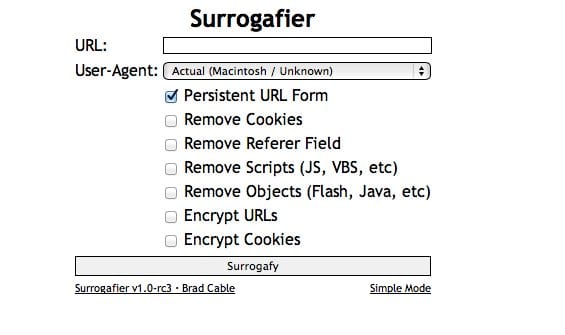
If you look closely you see it gives you a number of options:
- Switch your user-agent
- Persist through forms
- Remove your cookie
- Encrypt URL
- Encrypte Cookies
- and so on..
The kicker of this is that this proxy is publicly available via Surrogafier. I can’t help believe that this Church group had no intention of this file being on it’s site, let alone embedded within the core files of it’s plugin – Akismet. Yes, awkward moment I’m sure.
If you’re sitting there scratching your head wondering of the impact of a proxy like this on your box, here are a few reasons:
- Bandwidth usage
- Nefarious acts performed via your IP could be blacklisted
- Could lead to legal action against you if it’s determined you are the proxy agent
Cheers.







