Recently, we wrote about a malware redirect causing compromised sites to redirect their visitors to pornographic content (specifically, the BaDoink app). You can read more about what we found by going to our previous blog post.
As described in the original post, some particular files were infected (examples were the index.php, wp-config.php and others). We thought that was enough malware for one app. However, while we were working on an infected site today, we found a new malware injection causing this redirect.
Since all of the website files were clean and we didn’t find any suspicious Apache modules or binaries, it took a while for us to figure out the problem. However, it became much more clear once we investigated the PHP binary and found some suspicious entries.
First, after running the php -i command (which displays full PHP info), I got the location of the main php.ini configuration file. When I took a look at it, I saw the following suspicious entry:
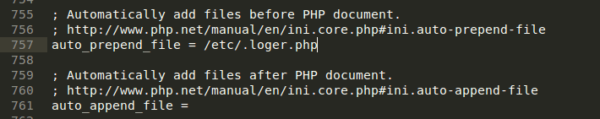
I was actually searching for the auto_append_file entry (because it is a very commonly used malware entry), but this time, auto-append was empty. Right above it, however, there was an auto_prepend_file entry that had some files assigned and it was this /etc/.loger.php, that looked very suspicious.
Here’s what we found when we opened the file:
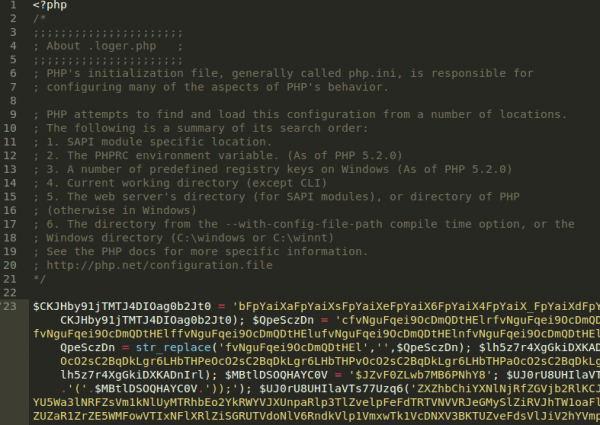
After deobfuscating it we could confirm that it was malicious and that it contained a redirect to the infamous porn app because it used the exact same code responsible for inserting the malicious JavaScript redirects to the documents (based on the User Agent). The solution was to remove the php.ini entry, remove the file itself, and then restart the apache server.
Be careful because simply removing the file will cause a crash of your site and will lead to a 500 internal server error, which is why Apache needs to be restarted. However, if you want to schedule the restart for a more appropriate time, removing all of the content from this malicious file (.loger.php in this case) would do the trick, and then you can remove it after restarting Apache.
What Did We Learn
We already knew this, but there is a lot of money to be made by redirecting website links to porn and some malicious agents will do this by hacking legitimate links and websites. In this case, there is still a lot of traffic being driven specifically to Badoink’s App. It’s important to remember that if you hear reports of visitors being redirected and can’t get redirected yourself, your site is still at risk as much of the malware we’ve seen is conditional. Finally, remember that we can prevent, detect and fix sites built on any platform (examples: WordPress, Joomla, Drupal) so if you’re having a hard time getting rid of the malware or any symptoms of malware, sign up for a plan and our team will clean your site today.
Stay safe and keep your eyes open!








5 comments
Hmmm…. how does a process get to write to /etc? Shouldn’t php.ini be owned by root and secured 644?
Agreed, /etc/php.ini should only be writable by root???
Some servers are just not configured properly. On that server hackers compromised one site first, then figured out a way to take over the whole server.
And actually, it doesn’t have to be in /etc. They could put this file to any writable directory (even /tmp).
But anyway, the initial problem was poor server security.
Wow Nice one. I’ve not come across that before and hadn’t even thought to look for it. But I will now. Thank you! And because this is PHP_INI_ALL this wouldn’t even need to be in the main INI file. It could be in a php.ini file or httpd.conf even. And the file could be anywhere in the include path. Well that’s just nifty.
Thanks for sharing!
Hi,
My name is Matthew and I work for BaDoink.
Thanks to Peter for writing this article and letting users identify and fix this issue.
Please note that BaDoink is not responsible at all for this infection. Whoever is doing this is redirecting the script to our website and we have no control over that.
We believed it was an affiliate and as a result they have been banned from our program.
We run a popular affiliate program; our brand has a large, global presence and notable market share. The overwhelming majority of affiliates promoting us are clean, honest and law-abiding; however not everyone in the world of online marketing is bound to a moral compass; some are predatory. When we identify such an affiliate, one who engages in illegal activities, seeks profit through deceptive or criminal marketing practices, that affiliate is terminated immediately.
If anyone wants to reach out to me about this issue or report something else then please send me an email to the following address.
matthew(at)badoink(.)com.
Thanks, Matthew
Comments are closed.