12.17.2014: See more information on the SoakSoak massive malware outbreak resulting from this vulnerability: RevSlider Vulnerability Leads To Massive WordPress SoakSoak Compromise by Daniel Cid
If you need help cleaning a hacked WordPress website, we released a new guide in 2016 that may help:
Guide to Clean Hacked WordPress
Mika Epstein, Ipstenu, of Dreamhost, notified us today of a serious vulnerability in the WordPress Slider Revolution Premium plugin which was patched silently.
It turns out that the vulnerability was disclosed via some underground forums. ThemePunch confirms that their plugin was patched in version 4.2 for those that purchase the plugin directly from them, and they include an auto-updater which would address the problem. The real issue lies in the way the plugin is wrapped into theme packages. ThemePunch’s approach to disclosing the issue was based on guidance they received.
This a very popular plugin, and appears to be one of the most downloaded slider plugins from Envato’s Marketplace – Code Canyon. It also appears to be bundled in theme packages so be sure to check your theme / plugins.
This is an example of where things go terribly wrong.
In this situation, a very popular plugin developer decided it was best not to disclose to anyone, in return patching silently. Mind you, this vulnerability was already disclosed as a zero day via underground forums, which you would have thought would incentivize a developer to work quickly and disclose even faster. No, instead a different course of action was taken.
Now, the vulnerability is being actively exploited in the wild. Yes, the vulnerability is severe enough that the attackers are able to compromise websites through it.
WordPress Slider Revolution Vulnerability
About 2 months ago someone publicly disclosed a serious vulnerability in the Slider Revolution Premium WordPress Plugin that allows a remote attacker to download any file from the server.
The proof of concept shared via underground sites shows how someone can easily download the wp-config.php:
http://victim.com/wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php
This is used to steal the database credentials, which then allows you to compromise the website via the database.
This type of vulnerability is known as a Local File Inclusion (LFI) attack. The attacker is able to access, review, download a local file on the server. This, in case you’re wondering is a very serious vulnerability that should have been addressed immediately.
Local File Inclusion (also known as LFI) is the process of including files on a server through the web browser.
UPDATE IMMEDIATELY!!!
Attacks In The Wild
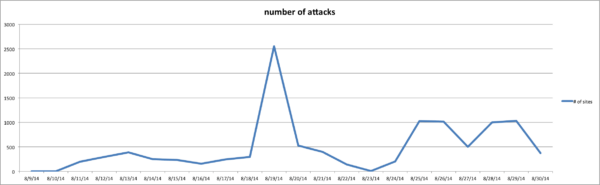
We thought it’d be in our interest to see how active attacks against this vulnerability were. We turned to our WAF logs and found that this vulnerability is being actively attacked in the wild. Today alone, there were 64 different IP addresses trying to trigger this vulnerability on more than 1,000 different websites within our environment.
Here is a snippet of what to look for in your access logs:
194.29.185.106 - - [02/Sep/2014...] "GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.1" 403 1082 85.103.12.6 - - [02/Sep/2014...] "GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.1" 403 226 91.229.229.201 - - [02/Sep/2014...] "GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.1" 403 226 85.103.12.6 - - [02/Sep/2014...] "GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.1" 403 1 85.103.12.6 - - [02/Sep/2014...] "GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.1" 403 11 94.242.246.23 - - [02/Sep/2014...] "GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.1" 403 11 74.120.13.132 - - [02/Sep/2014...] "GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.1" 403 11 77.247.181.165 - - [02/Sep/2014...] "GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.1" 403 1 37.148.163.38 - - [02/Sep/2014:...] "GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.1" 403 7269 37.130.227.133 - - [02/Sep/2014...] "GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.1" 403 11
It appears that via our environment, the attack appears to begin on August 09th, growing significantly on Aug 19:
Yes, if you are a client of our Website Firewall you are already being protected via our virtual hardening and patching mechanisms. No, if you leverage the latest WordPress Security utility plugin you are likely not being protected.
Update Now!
If you use the WordPress Slider Revolution Premium plugin, you have to update it immediately! We also wish the developers were more open and had publicized the issue and alerted their customers of the problem beforehand. This type of action is an example of what not to do, especially if you find out about the issue via a Zero Day disclosure.
***Update – 20140903 – Which Versions Affected****
This is a Premium plugin, this means we don’t have insights into the way they structure or release their plugins. We are however reaching out to the development team to confirm the exact date of the patch. There is mention of a patch in February, but because we have no insights into the older version of the plugin it is hard to confirm if it’s related to this or something else.
To illustrate the problem, here is a comment from one of the users of the plugin:
I have this plugin installed on a number of sites but none of the plugins are prompting me to update. In fact they’re all showing different version numbers: 2.03, 2.1.7, 2.3.91, 3.0.5, and 4.1.4 while the latest version on CodeCanyon is 4.5. Any idea why there is no option to update from within the WordPress dashboard? Thanks for bringing this to our attention!
If we hear back from the developers we will update accordingly.
The biggest challenge with this vulnerability is that it appears to be bundled in many theme packages. This means theme shops have paid for a developer license and are releasing the plugin with or making it optional to users. Users may or may not know they have the plugin installed because of this. We are also noticing that while most theme packages have updaters, they don’t update the plugins, only the themes which causes more confusion to the process.
***Update – 20140903 – Affected Themes****
A more comprehensive list of themes packages possibly affected include:
# WordPress IncredibleWP Theme Arbitrary File Download # Vendor Homepage: http://freelancewp.com/wordpress-theme/incredible-wp/ # Google Dork: "Index of" +/wp-content/themes/IncredibleWP/ # WordPress Ultimatum Theme Arbitrary File Download # Vendor Homepage: http://ultimatumtheme.com/ultimatum-themes/s # Google Dork: "Index of" +/wp-content/themes/ultimatum # WordPress Medicate Theme Arbitrary File Download # Vendor Homepage: http://themeforest.net/item/medicate-responsive-medical-and-health-theme/3707916 # Google Dork: "Index of" +/wp-content/themes/medicate/ # WordPress Centum Theme Arbitrary File Download # Vendor Homepage: http://themeforest.net/item/centum-responsive-wordpress-theme/3216603 # Google Dork: "Index of" +/wp-content/themes/Centum/ # WordPress Avada Theme Arbitrary File Download # Vendor Homepage: http://themeforest.net/item/avada-responsive-multipurpose-theme/2833226 # Google Dork: "Index of" +/wp-content/themes/Avada/ # WordPress Striking Theme & E-Commerce Arbitrary File Download # Vendor Homepage: http://themeforest.net/item/striking-multiflex-ecommerce-responsive-wp-theme/128763 # Google Dork: "Index of" +/wp-content/themes/striking_r/ # WordPress Beach Apollo Arbitrary File Download # Vendor Homepage: https://www.authenticthemes.com/theme/apollo/ # Google Dork: "Index of" +/wp-content/themes/beach_apollo/
Released on Exploit-DB September 1st, 2014. The emphasis on possibly is because if you are running the latest version of the theme, you might be ok, you might also not be ok.
It all depends on how the theme packager bundles the plugins and handles the upgrades. That, we can’t and won’t speak to.
If you know of more theme package feel free to let us know and we’ll be happy to update the list to ensure everyone is made aware equally and without prejudice. The emphasis here is to update your plugin, we do not intend to focus on any theme shops, their practice for handling dev licenses or any variation of that.
***Update – 20140903 – ThemePunch Response****
Here is the response from the developers of the plugin, found in the comment thread below:
Hi,
The problem was fixed 29 updates back in 4.2 in February. We were told not to make the exploit public by several security companies so that the instructions of how to hack the slider will not appear on the web.
You should always keep the slider up to date like any other WordPress component but urgently need to do this when using Version 4.1.4 or below in order to fix the security issue. Please use the included autoupdate feature (we solve issues within hours and update nearly every two weeks if nothing special needs a faster frequency).
We are sorry for you guys out there whose slider came bundled with a theme and the theme author did not update the slider. Since you cannot use the included autoupdate function please contact your theme author and inform him about his failure!
Best regards, ThemePunch
Here is the changelog from February:

The real issue here appears to be with how theme packages incorporate and subsequently update plugins their themes depend on.
***Update – 20140904 – More themes that might be affected****
These themes include the plugin and might be affected as well:
X Theme (2nd highest selling theme) – http://themeforest.net/item/x-the-theme/5871901
Bridge Theme – http://themeforest.net/item/brooklyn-creative-one-page-multipurpose-theme/6221179
The7 – http://themeforest.net/item/the7-responsive-multipurpose-wordpress-theme/5556590
Total – http://themeforest.net/item/total-responsive-multipurpose-wordpress-theme/6339019
BeTheme – http://themeforest.net/item/betheme-responsive-multipurpose-wordpress-theme/7758048
Inovado – http://themeforest.net/item/inovado-retina-responsive-multipurpose-theme/3810895
Porto – http://themeforest.net/item/metronic-responsive-admin-dashboard-template/4021469
Metronix – http://themeforest.net/item/metronic-responsive-admin-dashboard-template/4021469
Jupiter – http://themeforest.net/item/jupiter-multipurpose-responsive-theme/5177775
Newspaper – http://themeforest.net/item/newspaper/5489609
uDesign – http://themeforest.net/item/udesign-responsive-wordpress-theme/253220
***Update – 20140905 – Envato Release ****
Envato has releases the comprehensive list of the themes affected by this vulnerability.
If you have a hacked WordPress site, we recommend following the steps in our comprehensive guide to dealing ith a hack:








223 comments
Sucuri to the rescue yet again, thanks!
This appears to have been patched in version 4.2: http://codecanyon.net/item/slider-revolution-responsive-wordpress-plugin/2751380#item-description__version-4-2-skywood-25th-february-2014-including-security-fix
We thankfully only found one site of the ~250 we maintain that was affected and were able to apply a manual patch to the UniteImageViewRev::outputImage() function in revslider/inc_php/framework/image_view.class.php
I’m not a security expert, but adding a simple check of the file extension there seems to be working for us.
If this plugin is packaged with a theme and unable to update immediately, will disabling the plugin prevent this until an update for the theme is released?
@rickbannerman:disqus yes, disabling the plugin will prevent the attack – but no telling how doing so will affect the output of your site, depending on how the theme integrates.
Thanks!
Correct..
move your wp-config.php ‘UP’ a folder level.
This would still be vulnerable with a slight modification to the attack URL.
Ok, so… according to your logic, I should definitely not publicly post this url then, correct?
https://areawaste.com/wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php
Thanks for letting us know guys!
Remove the how to on the hack?
Yes seriously. Sucuri is getting out of hand writing an article showing how to do the exploit but not including information about what is the safe version number of the plugin or how to update it.
Hi @virginiasolomon:disqus
The exploit is already being actively shared, the faster we release it, the faster others can write rules to protect against it. This is not uncommon practice.
Thanks
I found it all over Google
The how to is pretty simple to pick out once you know where the vulnerability is… I would think exposing it like this will help show how big of a vuln it really is.
Correct.
absolutely I agree I think it is viable are doing.
agreed
In this scenario it makes sense to release, it’s already been in the wild, and actively being targeted, for over 30 days. At this point it’s time to share.
Thanks
I did not know that. it was out for that long I retract what I said it shows just how bad the Slider Revolution had been Vulnerable for so long as somebody hosted on FireHost and very naively believed
I was secure Because of the very expensive FireHost firewall which proves the cost of the firewall does not always correlate with the ability for to secure a site.
Until I ran the I used the hack (that is out on the web everywhere else already anyway.)
I agree with Tony it is something that drove me to take action and hopefully will get others to wise up and use a top-of-the-line WAF like CloudProxy
My hats off to for finding and patching before anyone else.
Plus without this confirmation person are less likely to take a vulnerability is seriously
If someone simply reads there has been a compromise on your plug-in will they take action?
My thoughts are some well most will not.
If you show them how to prove this is something that you need to take action on will they take action?
Most will if they are smart.
Adding another WAF thanks Tony much appreciated and I retract my comment above.
All the best,
Thomas
No worries @blueprintmarketing:disqus.. 🙂 Thanks for stopping by as always.
Thank’s Tony! @perezbox:disqus
This is worse than the article is making it out to be. This plugin costs money and there are TONS of themes on Themeforest that use this plugin giving buyers no way of updating the plugin without paying again. Themeforest does nothing about the quality of developers offering themes (their diligence about updating their themes) so many are stuck with this issue or will have to completely remove the slider from their sites. I’m having to remove the slider from 5 sites because of themes from Themeforest who’s developers don’t update their themes while using 3rd party plugins that are paid. Also, what is the version number of the plugin that isn’t vulnerable? What should people update the plugin to? This is kind of critical information that shouldn’t have been left out of this article.
That’s the same boat I’m in. Either remove it and leave large holes where the slider would be, pay to upgrade or wait for the theme developer. Unfortunately it will be easier for a lot of people to upgrade then remove, so ironically, they will probably see an increase in sales due to this vulnerability.
True but it shouldn’t be. I’m removing all of the sliders from all of my websites. Research shows they aren’t good for websites anyway, especially shops. I’ve been using them in static mode but now with all the easy frontend builder tools, I think I can do a bit better with adding a static image where the slider will be. This was just the final straw.
Makes sense.
well if that’s what it takes to rid the world of sliders (on homepages) then this vulnerability might have been a good thing 😉
Try leveraging a Website Firewall if you don’t want to upgrade or leave a gapping whole. Food for thought.
Hi @virginiasolomon:disqus
It’s actually a very bad situation, we agree.
We can’t talk to the practice of updating within the ThemeForest ecosystem, not much we can do in that regard. I do feel for your situation though.
Because this is a private plugin, we are limited in researching the history on it. What we have been able to see is that it has been patched in 4.5. This is why we don’t disclose versions, because unlike plugins in the WP repo, we can’t go backwards without engaging them (which we have not done).
I would say upgrade to 4.5 to patch the issue.
If the real issue is with handling the vulnerabilities, consider using a Website Firewall. Doesn’t have to be ours, there are others in the market, but they are designed to address this very issue.
All the best
Tony
@perezbox:disqus We have a site with version 4.2.2 installed that does not seem to be affected by this vulnerability. I can provide you a copy of 4.2.2. to you privately if needed. The change log on the plugin site includes a vague “Fixed Security Issue” in version 4.2.
Can you send it to labs@sucuri.net please?
Sent.
Could you send it to mlamberti101@gmail.com, please?
I’m afraid I no longer have access to that version, sorry!
While I cannot speak for other themes, we can certainly speak for Avada. We update it frequently, and any of our users can get a plugin update the day it comes out. This issue was fixed in the plugin back in February, and was updated in our theme shortly after. We would never do that to our user base. Please remember, the theme author does not make the plugin, they simply buy a license to include the plugin with the package, and most likely that is a part of the reason you have bought the theme in the first place. If what you say is true about other authors who themes you have bought, you should be contacting them immediately and also Envato support.
How can we tell if our plugin is the most up-to-date? Do you have a version number? I always update plugins when notified… but would like to know for sure I’m covered.
You can view the version number of any plugin in your plugin section of your admin. Look for the rev slider there. As long as you are on 4.2 or higher of the revolution slider, you are good. If using Avada theme, it was updated back in February so as long as you have updated your theme since then you are fine. If using Avada 3.5 or higher, then setup the auto updater so you will get notified of theme updates, which always include plugin updates also.
View our Avada theme docs for how to update before the auto updater, and then how to setup the auto updater: http://theme-fusion.com/avada-doc/install-update/how-to-update-theme/
You can check the plugin version number by navigating to “Plugins” in the WordPress admin dashboard; see the green highlighted area in this screenshot: http://snag.gy/lrTeo.jpg
The article says that the issue was fixed in version 4.2. The version number appears on the main Revolution Slider in the WP backend. Just scroll down a little bit.
We have Version 4.2.3 and it’s still vulnerable.
Thanks very much for the assurance lukeabeck. It’s a good thing i switched to Avada recently cos it felt secure, and now i’m even more assured its the right move. =)
You’re welcome 🙂 We take it seriously and treat our userbase as we want to be treated. Thanks again!
Thank you so much, Lukeabeck! I also am an avid Avada user with 9 different sites actively running your theme. I am thrilled to know we are safe. Awesome theme. Awesome support. Thank YOU.
You are most welcome Kate, and thank you for being a loyal Avada user!
1
Yes, but when I updated the slider, it didn’t work anymore. The server was failling to load js files. Now I’m stuck with either no slider or an infected slider. Perhaps their are special instructions for making this update work?
Hmm no there are no special instructions. A regular update will do. We can help you out on our support forum and do it for you, signup there http://theme-fusion.com/avada-doc/getting-started/free-forum-support/
That should not happen. We can take a look for you on our support forum where we provide support for users. I cannot post the link here or Sucuri will not approve my comment it seems. But all the info you need for our support is in the included docs or online at our support site.
Not only Themeforest does nothing about quality, also Codecanyon. I bought a lot of plugins that did not work properly, even on a brand new WordPress installation. And that was the reason to ask myself: how secure are those plugins from Codecanyon? And those items from Themeforest? The bad truth about Envato is: they look for quantity, not for quality. My hope is that someone builds an alternative where items are previewed for code quality and functionality. That would be a lot of work so items would be more expensive. And maybe you couldn’t find as much items there as on Envato’s marketplace. But I’m shure that people would pay more when they know that not every second item they buy is pure bullshit.
hi, Stefan from ThemeFuzz here,
We have a system in place for clients to easily update the bundled plugins. Even if you do not purchase the specific plugin, by using our themes you are notified and have the ability to update the plugins to their latest version.
This ensures that none of our clients are affected by this vulnerability.
Best regards,
Stefan
How about now? http://gizmodo.com/mysterious-russian-malware-is-infecting-over-100-000-wo-1671419522.
Wow… a quick inurl query on google also reveals a bunch of websites with the plug in’s parameters in their robots.txt files… Why would you even let admin-ajax.php be indexed by google?
This is very serious… Thanks for spreading the word.
This is correct.. we saw that too and decided against sharing that nugget of information.
Does this have vulnerabilities for non wordpress use of this plugin?
The attack exploits the revslider_show_image function by calling files it shouldn’t be calling. I’d imagine the vulnerability would persist outside WP.
This is incorrect, the issue is specific to WP (and a very old version of the plugin) — the revslider_show_image function you are referring to is a PHP function.
I looked on CodeCanyon and they haven’t updated the plugin since 8/26. Is that the update with the patch or should I be waiting on a new one to be released?
This is hard to say, it seems 4.5 is patched but because this is a private plugin we can’t confirm.
Yeah their change log doesn’t refer to any serious fixes (unless you consider a broken Ken Burns effect serious), but I’ll be updating all of my sites to it anyway. Thanks for the info!
There’s a vague “Fixed Security Issue” note in 4.2’s changes and I was unable to use this exploit on an installation using version 4.2.2.
Alex,
all of our customers website are running on 4.6 (which is the 26th Aug 2014 release) and I have retested all sites and none exhibit the vulnerability. So looking good for the newest version.
If we’re using managed wp hosting with Flywheel and running an older version of the plugin, is the site ok (since Flywheel doesn’t give write access to wp-config)? I reached out to them for an answer but figured I’d go ahead and ask here.
Also, does disabling the slider plugin remove the vulnerability or do I need to completely delete it?
@caseyfulgenzi:disqus blocking write access to wp-config.php will not provide any protection from this attack, but disabling the plugin does.
Correct. Deactivating will do the trick as well.
getflywheel is an awesome managed WordPress site but I can tell you every one of the big five are vulnerable right now I have tried it on all of them.
It is best to disable the plug-in or what I would suggest is changing it out with a better slider
Soliloquy is much faster and works better with managed WordPress hosting
Just tried disabling the plugin. WP refreshes and gives the notification at the top that it’s disabled but then it’s actually not. Is that just because it was included with the theme?
It’s possible the theme is automatically activating the plugin. If so, you may have to remove the plugin.
Slick is also an awesome slider: http://kenwheeler.github.io/slick/
Add cloudproxy WAF with get flywheel that is what I run for many clients garrisonbespoke.com is a perfect example of a flywheel site that is protected with cloudproxy try running the script on their and try running it on your site as it is
I need to do a server wide search for sites that may be utilizing this plugin. Can anyone advise to a folder structure or specific file name that would be unique to this plugin? Thanks!
Mmm, I don’t know the specifics of the plug in… However you could try something like this (assuming a
*nix environment)
find . -exec grep -l “revslider_show_image” {} ;
which would throw back a list of files containing the function the plugin calls for in admin-ajax.php.
Thanks Ryoku! I was able to find one installation by doing
find /var/www/vhosts/ -name “revslider” -print
However I’m not sure this method will work across the board because that plugin has been packaged with so many themes, I figure directory name could have been changed over time.
You can try
grep -sHor themepunch *
This will also find it within most zip files, backups, cache, etc
The problem I found is that “revslider_show_image” is present in both the vulnerable and updated (fixed) versions. My solution was to do something like this:
locate revslider.php
Then for each result I did:
head /path/to/revslider/revslider.php
Revslider versions <=4.1.4 are vulnerable (per http://packetstormsecurity.com/files/127645/WordPress-Slider-Revolution-Responsive-4.1.4-File-Download.html)
For each plugin that's vulnerable, first make a backup:
tar -zcvf /backup/sitename_date.tar.gz /path/to/revslider/
If you have any custom CSS for titles / text layers, it's a good idea to make a separate backup of that. I've found it stored in revslider/rs-plugin/css/captions.css and revslider/rs-plugin/css/dynamic-captions.css
Then update the plugin to any version greater than 4.1.4
Once you update the plugin, you'll have to re-add your custom CSS by editing any slide and then modifying global styles.
I am working on determining the specific code that fixed this vulnerability. Right now I've found a few lines in revslider/inc_php/framework/functions_wordpress.class.php that appear to be relevant:
—–
Extra lines in New before 187 in Old (File functions_wordpress.class.php; Line 189:192; File functions_wordpress.class.php; Line 187)
—–
$ul_dir = wp_upload_dir();
I have this plugin installed on a number of sites but none of the plugins are prompting me to update. In fact they’re all showing different version numbers: 2.03, 2.1.7, 2.3.91, 3.0.5, and 4.1.4 while the latest version on CodeCanyon is 4.5. Any idea why there is no option to update from within the WordPress dashboard? Thanks for bringing this to our attention!
@Yaron Guez:disqus This plugin does not receive updates via the normal WordPress mechanism. The latest version must be downloaded and upgraded manually.
Yes, this is another issue we noticed as well.. very unfortunate.
I had some sites running 4.1.1 and the hack worked. Updating to 4.5.9 fixed it.
Another site running 4.3.3 did not have the vulnerability.
Hi Daniel,
Thank you for letting us know about the explot. However, please remove Avada from the article as there is no reason to put us in the spotlight. We regularly update our theme and bundled plugins http://theme-fusion.com/avada-documentation/changelog.txt
However, this is terrible from revolution slider to not let their users know about the major patch. I have not even received an update email.
Thanks
According to the changelog (and a comment here), this issue was fixed in Revolution Slider 4.2 which was released in February on CodeCanyon.
We have not been able to confirm this. We are reaching out to the development team. We have no idea what was patched in 4.2 and what was not, we have no access to the plugin. Until we see the code it’ll be hard to confirm.
You can see the changelog from their item page, 4.2 is 7 months old and they did list our the security issue: http://d.pr/i/MyHU However, we do not know the details of that change either, only that it was listed out as the “security issue”. I’m sure Themepunch can shed some light on that.
We fully agree that a security issue is serious and should be taken care of (as Themepunch already did), however you should be careful with how you word the article when you are not sure of what happened or when it was fixed. You mention that they didnt even notify their buyers when that can easily be proved to be false as the changelog shows above. Why post that without knowing the truth?
Once you have all the facts then you can post an article bashing them saying they did not notify anyone, however you do not know that and simply assumed that was the case. As you stated, you do not even have the plugin. I would think for a serious matter such as this, Sucuri would of spent the $18 to buy a copy of it and investigate. Just my .02 on the matter.
Nevertheless, I’m sure Themepunch will be in touch if you guys reached out.
Thanks
Hi @lukeabeck:disqus
Thank you for your thoughtful response.
Updating the change log is not notifying your buyers, it’s updating your change log. As you can also see from that log entry, there is no way to know if that fix is relevant to this issue or something else (unless you know something I don’t, but based on your response above you don’t).
Regardless, if the only issue here is “notification” we can live with that. Because of the magnitude of the issue, and the fact that it was brought to our attention from a third-party whom had been having issues engaging with the developer, we stand by our approach.
Thanks for your .02 though. Look forward to engaging with them.
All the best
Tony
You’re most welcome.
And don’t get me wrong, we fully agree with you on the importance of the security issue. That is not what I was trying to get across. And I understand about the changelog also. the point I was making is the article made accusations about the issue, when in reality it sounds like it cannot be backed up. Research upfront would of been better. How do you know that buyers were not notified if you have never bought the plugin? That is the point I was making.
Either way, best of luck.
Thanks
Also, your “list” of themes is extremely unthrougough. Literally 80% of top selling themes on Themeforest ahve the plugin.
To name a few …
X Theme – http://themeforest.net/item/x-the-theme/5871901
Bridge Theme – http://themeforest.net/item/brooklyn-creative-one-page-multipurpose-theme/6221179
The7 – http://themeforest.net/item/the7-responsive-multipurpose-wordpress-theme/5556590
Total – http://themeforest.net/item/total-responsive-multipurpose-wordpress-theme/6339019
BeTheme – http://themeforest.net/item/betheme-responsive-multipurpose-wordpress-theme/7758048
Inovado – http://themeforest.net/item/inovado-retina-responsive-multipurpose-theme/3810895
Porto – http://themeforest.net/item/metronic-responsive-admin-dashboard-template/4021469
Metronix – http://themeforest.net/item/metronic-responsive-admin-dashboard-template/4021469
Jupiter – http://themeforest.net/item/jupiter-multipurpose-responsive-theme/5177775
Newspaper – http://themeforest.net/item/newspaper/5489609
uDesign – http://themeforest.net/item/udesign-responsive-wordpress-theme/253220
So how should plugin developers notify the buyers, in your opinion?
Envato does not allow plugin developers to directly contact buyers, unless the buyer first posts a comment. The buyer needs to initiate contact first, authors cannot simply send out a mass e-mail saying “Hey everyone, there is a bug, please patch it up immediately.” Authors do not have access to buyers’ e-mail accounts, or any personal information for that matter.
With that said, updating the changelog is all any plugin developer really can do. There is no line for direct communication with every single person who has ever purchased the plugin, this simply does not exist within Envato’s infrastructure.
Doesn’t this only really show what a big cock-up Envato is and their practices are? Why would a developer even want to be on that platform? Why does Envato allow theme-authors to bundle plugins?
I purchased the plugin so that I would receive updates and support about it. How hard would it have been to add some explanation/info/urgency to the messages that are currently sent to owners (through Envato)?
This would not have helped those users who are bundled, but at least it would get the word out. And I could have patched the error right away when notified. Shame on you, ThemePunch for hiding a problem and not doing everything you can spread the word about the severity to at least your paying customers.
First off, we are not the developers of the revolution slider, we make the Avada theme. And the plugin is not “integrated” into the theme, is is simply a stand alone plugin that you can choose to install if you wish. Pointing out our theme name in this article is completely unfair for several reasons, all of them obvious. Also, the version you are talking about was fixed back in February, 7 months ago.
And from what I see, the slider developers did post it in their changelog, which is contrary to your above report. It lists out a security fix in the changelog. However, they certainly should of been more proactive in letting their user base know about this, we fully agree with you on that. Either way, its unfair to list out one theme when dozens of them use that plugin, please remove our theme name from your article.
Hi @lukeabeck:disqus
We removed reference to the Avada theme. We’ll be looking to see if we can’t compile a more thorough list of theme packages that make it available to their clients in an effort to make it a more comprehensive list and in an effort not to single out any one shop.
The reference to your package was just one we tested, it wasn’t saying you were responsible for it, it was saying that end-users might have it installed whether they intentionally did it or not, in short, look through your stuff and get it patched.
Thanks for removing it. Yes we know what is was saying, however it casts a bad light no matter how you say it.
And it was fixed back in February, 7 months ago and updated in our theme during that time as our included plugins always are. We’re very cautious about any bugs or issues we find in anything dealing with our theme.
Thanks again.
We’ve updated the list of possibly affected themes to more accurately reflect the impact and added some qualifiers to help differentiate intent.
You might also be curious to know that when you run an old version of your theme and update, the old version of the plugin stays in place and no mention is made of it being out of date. This has been tested in our environment (version 3.2). If we delete the old version, then your upload package notifies us to upload the latest version.
Thanks
Yes that is because v3.2 is older and does not include the update messages. As long as you are on v3.5 or higher, you will be notified when you update the theme to update the plugin.
Why has your list not been updated with other themes? Seems my comment was deleted also that listed them out. Your “comprehensive” list is not “comprehensive”. Since your whole vendetta is to warn people and get the word out, why have you not updated your list and only show a very small fraction of themes?
Hi @lukeabeck:disqus
We’ve updated the post with the latest update from Envato. There list is by far more comprehensive.
Thanks
Absolutely agree, very glad they took the time to gather the information for this.
Yep, their list is perfect, contains them all so the users are aware of the issue. Thanks Envato!
You’re great Lukeabeck. Really, Avada theme is the best! I don’t say this not only as a buyer but also as a developer myself… You guys rock!
Luke, I’m a user of Avada theme and I’m a happy user. However, the following is not true:
“First off, we are not the developers of the revolution slider, we make the Avada theme. And the plugin is not “integrated” into the theme, it is simply a stand alone plugin that you can choose to install if you wish.”
Revolution Slider ‘was’ integrated to Avada when I bought it. There was no way to delete or update it indipendently as it was not listed on the WP Plugins page. Only after a few versions later you have seperated the plugin from the theme.
I’m glad to see that you have stopped integrating plugins that you license. It was a bad practice. You should have thought that in future updating code would have become a mess, which it did with very bad consquences to many of your users who were hacked.
I want to put the record straight.
I’m afraid there is a misunderstanding here, the record is not “un-straight” 🙂
First off, the rev slider ‘was’ integrated long ago, yes. But no, we are not the creators of it nor do we have control over it. In addition, the exact day the plugin update was issued for the security issue, it was also live in Avada for any who updated and kept up with that.
And I’m not sure what you mean by “future updating code would have become a mess”, that is definitely not what we have seen or experienced in our support. The change from integrated plugins to non-integrated was seamless.
“First off, the rev slider ‘was’ integrated long ago, yes. But no, we are not the creators of it nor do we have control over it”
This is like saying the vulnerabilty in TimThumb was nothing to do with theme authors. If you ‘include’ a code in your intalltion routine, what happens with that code IS your responsibility. Do realise that I’m not saying you reacted irresponsibly. You acted correctly. However, your (unnecessary) defense is not correct.
“that is definitely not what we have seen or experienced in our support.”
I have recently updated a very early version of Avada and the process was far from “smooth”. Far too many things have changed in the theme. Even the shortcodes which were integrated are now supplied via a plugin. The vulnerable Revolution Slider has also changed, which required copying CSS values over.
Furthermore, there was no theme update notification (or an option to do so). As I was not following your releveant forum I was only notified by Envato that there is a new version due to the said vulnerability.
Do you think that my experience can be classified as “smooth”?
Hey Sarumbear … let me say thank you for being a long time Avada user! I can recall your username long ago, maybe even back to v1. That’s pretty awesome 🙂
I think we will only disagree further on the first point. It is not a defense as much as it is an understanding. I heartily disagree with you on that point that we control the rev slider code and should be the ones who make changes. It is the highest selling WP slider plugin, hugely popular. We include a license for it in our theme, we will not make edits to the plugin nor manage the codebase. I’m pretty sure you will find that same response from other theme authors.
For updating, this will depend on many factors, none of which deal with plugin integration which is what your first comment presented and why I replied as I did.
Yes, shortcodes are now supplied in a plugin, and that is a good thing. It is best practice and how it should be done. When you update the theme, you simply install the plugin to get the shortcodes. You are notified in your WP admin that the plugin needs installed … that is all standard. In addition, we always list out these changes in our documentation and update notes. Always check out the supplied changelog when you update, or visiting our support center.
Copying over CSS from rev slider is also something that you should always be doing. If you are using custom CSS in anything, you should be backing it up. We do not control changes made in the rev slider, and backing up CSS is something you should always be doing no matter the situation.
For theme updates, there is not an automatic theme updater supplied for themes from Themeforest. Originally Avada never had one, but we added it back in v3.5. When you set it up, you get auto theme updates and will be notified in your admin. In addition, you can be notified via Themeforest any time the theme is update, all it takes is checking a box on the downloads page. I wish that was done automatically from their side but it is not.
About the rev slider security issue, once we found out we did everything we could to notify our user base. I checked your user account and you are not subscribed to our newsletter so you only received an email from Envato once they found out, which was exactly the same time we found out. Outside of that, I’m not sure how else we could of notified you, especially since TF notified anyone who bought the plugin or a theme that supplied it.
I wish that all plugins came with auto updates no matter what, just like ones from the WP repo. But plugins sold on code canyon are not like that and have specific licensing rules to them. Again, that is not something we control, but we have done what we can by adding auto theme update notifications and are recommending every chance we get to make sure any plugin included as a bundle on TF comes with the same auto updates that come with a plugin bought individual. I think it is coming this year, i can feel it 🙂
You mentioned that new updates had “far too many things that change”. Yes, and that is a good thing. Any product, especially software does that over the course of time. It is called improvement and we go through great lengths to make these improvements and ensure they have extremely little impact on previous customer sites. These new items we add and changes made are at the request of our 120K user base and are all done in the spirit of improvement. If you are happy with the site, then do not update. If you do update, take a little bit of time and look up our notes, they are always available. If a security issue comes up, like the one we are discussing, then yes you should update no matter what and take time to look up update notes.
When you update any software, always keep things like that in mind. New software comes with new features, new settings, new processes. To learn about them, always check with the developer. We always put out update notes with each release.
For any other update issues and your process not going” smooth”, we would gladly reply to any questions or concerns you have via our support system.
Thanks
Just to let you know:
“You are notified in your WP admin that the plugin needs installed … that is all standard.” hasn’t happen, neither for the shortcode plugin nor for Revolution Slider. I knew of the latter hence I have installed it but not the former, which I knew of its existance after my first support email.
Besides that where we disagree is not specific about you as a publisher. I am debating the fallacy of a general practice. The v1 Avada had bundled the Revolution Slider in a such a way that it was not controllable by the user. It was installed within the theme directory by you and the user had no knowledge of it being a seperate entity. This is afact. In situations like this the existence of such a code is your responsibilty. That is my stance and that is the stance that is accepted in the software world, maybe not in the WP world. However following the recent developments I can see that WP world is maturing and following the established software practices: if a code is not under your control tell the user from the start, make sure they read that code’s license and T&Cs seperately, etc., etc.
I wish you all the best as an otherwise happy user. Yes, I am a user since Avada 1.0. Since then I am responsible for at least a dosen more licenses purchased by clients to whom I consult to.
If you are on Avada 3.5 or higher and have setup the auto theme updater, then you will be notified. If you have not set it up, then you will not be.
My point though is that there is still not a method for themes that includes premium plugins to auto update those premium plugins, the license does not allow that. We have to follow those rules, we cannot break license. However …
Avada is auto updated once you set it up, simply fill in your credentials in theme options and auto updater will work. When we issue an update, you will be notified in your WP admin just like any other default WP theme. Then when you update the theme, you also get notifications to update the plugins. See my link above. Again, this is all we the theme author can do until license rules change and we are allowed to have our customers auto update premium plugins we include.
Regardless of that fact, you are safe if you use our auto updater because we will always issue a theme update the same day any security issue is known. As long as you have theme auto updates setup, you will be notified that same day in your admin.
Trust me when I say that we want each premium plugin to have auto updates with it on their own. It would make everyone’s life easier if plugins that are included with a theme, came with their own single license to auto update. Right now, following the license rules, we cannot do that and can only do it through the theme, which we do religiously.
Envato does inform users of these things on their site, but you have to go digging. Keep in mind that we sell exclusively on Envato’s marketplace, they make and control the rules and licenses. We abide by them.
Thanks for the continued purchases and support! We’re just a ticket away from any questions or concerns you have.
Thanks
@perezbox:disqus , If folks have moved wp-config.php up a level ***LIKE THEY SHOULD HAVE*** have you seen any instances of the wp-config.php file being accessed then?
Incorrect, still susceptible. Whether ./wp-config or ../../wp-config doesn’t matter… same applies. That file was also just an example.. it could have been any other file as well.
So…@perezbox:disqus, you’re saying that ‘Moving wp-config.php’ is NOT a solution to fixing this problem? (and subsequently would have been great for Daniel to mention in the body of his post)
Again, let me publicly post this url here to make sure I’m using the correct path and everything:
https://areawaste.com/wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php
Careful if you have multiple domains on the same hosting account and/or additional domains are mapped to subfolders. If you do this for one of those additional domains, the move of wp-config.php to level up will result on site on root folder become unusable/corrupted
I have in the past encountered many website owners who engaged developers to create their site and ended up with plugins like Revolution Slider and simply don’t have access to the upgraded version. They will be stuck and will have to spend money to purchase a license under the name.
Hi,
The problem was fixed 29 updates back in 4.2 in February. We were told not to make the exploit public by several security companies so that the instructions of how to hack the slider will not appear on the web.
You should always keep the slider up to date like any other WordPress component but urgently need to do this when using Version 4.1.4 or below in order to fix the security issue. Please use the included autoupdate feature (we solve issues within hours and update nearly every two weeks if nothing special needs a faster frequency).
We are sorry for you guys out there whose slider came bundled with a theme and the theme author did not update the slider. Since you cannot use the included autoupdate function please contact your theme author and inform him about his failure!
Best regards, ThemePunch
Thanks for the update, post has been updated to reflect your response.
Take care.
Tony
I had Revolution Slider installed, but the auto-update feature did not work. The auto-update area inside the plugin interface will not accept any entries: envato username, envato api key, plugin purchase code. Rev Slider has lots of great functionality, but it has historically been very slow. Due to the sluggishness I don’t use the plugin anymore, so I simply deleted it. That should fix the security problem.
Hi TommyLinsley,
the auto updates works fine, however you will need to have a regular license purchased of the Plugin. It will not work with your “Theme purchase code”.
Since this Fix we had 29 !!! updates. And not just the Security Issue has been fixed since that, but around 250 new features has been added, and also the engine has been rewritten.
The “historicaly slow” slider what you talk about from Ferbruary got 29 updates, and has better speed and load messures as the most known slider today.
We have a full customer service, available almost 7×24. You have always the possibility to contact us if you have issues with performance and or updates. We will help for sure !
Cheers,
ThemePunch
@themepunch:disqus don’t you agree that it is a bit silly to first sell your dev license to countless of theme developers, so they can bundle your plugin with their themes and now make the end user responsible for purchasing the plugin?
You could have seen that coming from a mile away!
I really think it is also your responsibility to actively approach the theme developers that bought your plugin AND all the possible end users.
Also silently updating a plugin that has such a major vulnerability is just so bad practice. You mentioned before that several security firms advised you against disclosing that information. Names Please!
Hi,
DevLicense – Theme Authors are informed about updates from Envato like every other customer. The hint “Security Fix” should ring some bells in their heads too.
What does “Security Fix” means other than Security fix? Why did they not update the plugin since February? Our direct customers do and can update their plugin regularly.
Sliders that came bundled with a theme are by the terms of CodeCanyon responsibility of the theme author. If they cannot provide such support they should not include the slider! We cannot check every theme in the internet (if you provide this service please contact us). If the theme authors would have done their job end customers would not have to shell out $18 to get a future proof plugin. If you find your theme has not updated plugins inside please contact the support of the theme author or the market place about this. It is a farce to be blamed for someone else’s failures too.
Silent Update – We gave everybody the time to update their plugin BEFORE the details of the hack becomes public. You had 29 Updates and 7 months. Why did you or the theme author not update when you were informed of a “Security Fix”? “Silent” means we did not give out detailed information in order to protect your installation. Do you wanted us to expose all installations with details of “HowTo Hack” without giving anyone the chance to update?
Security firms – You want to keep on the finger pointing? Keep pointing to us then. We made the decision to trust our partners, so do they.
Cheers, ThemePunch
You sold buggy code to theme developers but do not allow direct update to clean it. That is at best mean, at worst irresponsible. Take your pick.
Meanwhile, you also allowed theme developers integrate the plugin in such a non-standard way that even if I am willing to re-purchase your plugin to access the clean code, I’m stuck with the old code. At best irresponsible, at worst…you name it!
My Installed Version is 4.5.95 – the update isn’t available on the dashboard. I also have this plugin packaged with a theme but I am unable to disable it because I’m using it with a live site.
4.5.95 isn’t vulnerable to this exploit
It does look like there are some themes that use this plugin and come pre-packaged with it, lets hope the theme authors will realize the problem and update their themes.
Hey guys, I made a quick video showing that moving your wp-config.php doesn’t stop this vulnerability from being exploited. You’ll need to update or protect with a firewall to prevent it from happening. Take a look here: https://www.youtube.com/watch?v=etkFLR_RoO0
Great video but than how they could connect to my database?
If your database server is configured to only allow local connections it would probably be quite difficult for them to connect to the database (but probably not impossible?).
WooCommerce Supermarket Theme – GoMarket
http://themeforest.net/item/woocommerce-supermarket-theme-gomarket/7049228
This is another theme using Revolution slider…
Wow. This is quite parallel to what’s been going on with GM’s faulty cars. They sell them through dealerships and the dealers can decide whatever they want to do with the cars (price, financing, rebates). But when there is an issue with the cars, GM releases a statement to EVERYONE (gov’t, general public, dealerships), and any consumers using that car brings the vehicle back to the dealership which then decides how it will go about remedying the issue.
Initially, I thought the plugin developer was being unjustly maligned “We have no control over theme developers who bundle our slider with their files.” but they should have contacted everyone they licensed the plugin to and said “Hey, please only include this version of the slider, or please stop including the slider, or please let your customers know about the issue and contact us.”
Not sure who decided that silence was golden here, but this should be a lesson to developers. Tons of companies issue product recalls (and it doesn’t damage their reputation). Web companies should not think that they are somehow above the practices of brick-and-mortar companies.
Am I correct in the assumption that keeping ‘wp-config.php’ outside of the ‘htdocs’ folder will prevent this vulnerability?
you are not correct assuming this. proof: http://youtu.be/etkFLR_RoO0
No. See @joeherbrandson:disqus’s earlier comment; he’s created a video demonstrating that moving the wp-config.php file up one folder does not protect it from this vulnerability.
Also, this vulnerability is not limited to the wp-config.php file – it was just used as an example to demonstrate the vulnerability.
You can also protect a site using Apache mod_rewrite with three lines added to your .htaccess or your site config:
RewriteEngine On
RewriteCond %{QUERY_STRING} .*/wp-config.php
RewriteRule / [NC,R=301,L]
Please note that this vulnerability is not limited to the wp-config.php file – it was just used as an example to demonstrate the vulnerability.
The Frisco theme by CreativeSmitten ships with Revolution Slider 3.0.95. The theme is/was sold by Mojo Themes, its no longer listed.
I can confirm that having the latest Wordfence + preFebruary RevSlider together IS NOT SECURE.
If anyone is using Wordfence maybe received this by email: IT¨S WRONG.
Email received:
SUBJECT:
[WordPress Security] File Download Vulnerability in the Slider Revolution Premium WordPress Plugin
BODY:
Dear WordPress Publisher,
If you would like to stop receiving WordPress security alerts and product updates from Wordfence, you can click here. You subscribed to this list via the Wordfence security plugin for WordPress. If you find this alert helpful, please give us a 5 star rating on WordPress.org.
A commercial plugin called Slider Revolution had a vulnerability which was fixed in February. Many themes rely on this plugin and are using old versions of Slider Revolution which has left sites vulnerable to the exploit. Attacks on the old version of Slider Revolution are now being seen in the wild.
The vulnerability lets a hacker download any file from your system including your wp-config.php file which contains database passwords and other sensitive data.
What to do: If you are using the free or paid version of Wordfence, we have just released Wordfence 5.2.2 which blocks this attack on Slider Revolution, even if you have a vulnerable version installed. So you’re already protected if you upgraded to Wordfence 5.2.2 released today.
If you have Wordfence auto-update enabled then you will automatically be upgraded to Wordfence 5.2.2 within the next 24 hours and will be protected from this attack. If you want to enable Wordfence auto-update, go to your Wordfence options page and check the box titled “Update Wordfence automatically when a new version is released” and hit “Save”.
If you are running Slider Revolution, please make sure that you are running at least version 4.2 which contains the fix released in February. You can find Slider Revolution on the ThemePunch website at: http://themepunch.com/revolution/ if you need to grab the latest version or contact them. You may also need to contact your theme developer if they bundled this plugin with your theme.
If you found this alert helpful, please give us a 5 star rating on WordPress.org on the right of the page.
Regards,
Mark Maunder
Wordfence Founder & CEO
PS: If you aren’t already a member you can subscribe to our WordPress Security and Product Updates mailing list here. You’re welcome to republish this email in part or in full provided you mention that the source iswww.wordfence.com. If you would like to get Wordfence for your WordPress website, simply go to your “Plugin” menu, click “add new” and search for “wordfence”.
Hi, I confirm that the ThemeForrest themes that I bought with Slider Revolution in bundle are vulnerable and could not be updated. At this stage just deleted the plugin, better this then giving away my wp-config.php file 🙂
I confirm that my website from Theme Forest is also vulnerable through Rev Slider and I can’t do nothing about it either.
You can contact the theme vendor and ask them to provide you an updated version of the plugin. If they are unwilling or unavailable, you can purchase the latest version of the plugin for $18.
You can als patch this yourself by editing the niteImageViewRev::outputImage() function in revslider/inc_php/framework/image_view.class.php. Personally, I added two lines to check if the file extension is an image. This will protect wp-config.php and other non-image files, but I believe the latest version of the plugin is more comprehensive in this, checking the file name against the WordPress media library.
also applies to:
# WordPress X Theme Arbitrary File Download
# Vendor Homepage: http://themeforest.net/item/x-the-theme/5871901
# Google Dork: “Index of” +/wp-content/themes/x/framework/plugins/
# WordPress Shift Theme Arbitrary File Download
# Vendor Homepage: http://themeforest.net/item/shift-a-tumblog-style-wordpress-blogging-theme/4301599
# Google Dork: “Index of” +/wp-content/themes/shift/
# WordPress Soulmedic Theme Arbitrary File Download
# Vendor Homepage: http://themeforest.net/item/soulmedic-flat-responsive-medical-health-theme/6282832
# Google Dork: “Index of” +/wp-content/themes/soulmedic/
I can confirm that the Brandon theme, version 1.5, is vulnerable. Theme URL: http://themes.muffingroup.com/brandon/
Actually the demo site itself has the vulnerability too
Another premium theme using this slider…
WooCommerce Supermarket Theme
http://themeforest.net/item/woocommerce-supermarket-theme-gomarket/7049228
As has been demonstrated elsewhere in the comments, moving wp-config.php up a folder is still susceptible to this vulnerability by modifying the attack URL. In your particular case, the version of the plugin installed is not vulnerable to this exploit, so feel free to publicly post that URL to your heart’s content.
I didn’t – on purpose – go in and install a version of RevSlider that was WELL below the version listed? Awww @lucaskarpiuk:disqus, bless your heart. If you want, I’ll put the old one back up there again, with an even FURTHER backwards version.
There’s no need for hostility.
I’m terribly sorry you thought I was being hostile. I was actually smirking and getting some popcorn.
Plase can you share how to apply a manual patch to fix this security issue, I have a theme that is no longer available on Themeforest so I can’t ask for an update. Thank you.
This patch isn’t as comprehensive as what the plugin author provided in version 4.2 but it will at least limit the plugin’s access to images. In the file ‘inc_php/framework/image_view.class.php’ look for private function ‘outputImage’ at about line 142 and make the changes outlined here: https://gist.github.com/karpstrucking/8e86502c27eaa2182021/revisions
You can just block the call to your wp-admin folder by a simpke htaccess command. That would have prevented any of these calls either way regardless the leak.
How can I do that? I’m a total noob on WP, can you share that solution please?
hi,
This is not an options, as the wp-admin is used for ajax calls. This would make your site unusable.
Best regards,
Stefan
As has been explained by many others, this has been patched for months both in the plugin and many leading themes. With regards to the X theme, we have included the patched version of Slider Revolution since version 1.8.1 released in April, 2014 (11 releases ago). Put simply, the past 11 versions of X have included this patched version of Slider Revolution which our customers can always download directly from their ThemeForest download page. More information for our customers can be found in our member center here: http://theme.co/x/member/forums/topic/regarding-old-verisons-of-revolution-slider/
As has been explained by many others, this has been patched for months both in the plugin and many leading themes. With regards to the X theme, we have included the patched version of Slider Revolution since version 1.8.1 released in April, 2014 (11 releases ago). Put simply, the past 11 versions of X have included this patched version which our customers can download directly from their ThemeForest download page and have been able to for months. More information for our customers can be found in our member center here: http://theme.co/x/member/forums/topic/regarding-old-verisons-of-revolution-slider/
hi, Stefan from ThemeFuzz here.
Just wanted to assure our clients that we always provide the latest version of the plugins we provide. Also, we have our own update system in place and every client is notified to update the plugins provided in our themes. This means that you won’t be affected by this issue.
Best regards,
Stefan
Hi,
I’m Mark Maunder – the email author. Please email a zipped package with the revslider you’re using and your theme to genbiz@wordfence.com and mark it for my attention. Our testing shows that we have in fact provided an effective block for this attack vector so I want to investigate why this isn’t working for you.
Thanks,
Mark.
I had to check, because I was only webmastering the site:
The problem came from the template itself: neighborhood by envato and the way they bundled it:
http://themeforest.net/item/neighborhood-responsive-multipurpose-shop-theme/5086341
So that RevSlider was not updateable from wp-admin, so the admins never knew about the updates. Of course the Admins weren´t aware that the server was compromised.
We were hacked on 31.08 (and before), during quarantine we found this article and we were able to a exploit ourselves easily.
Hi All,
I just wanted to link to a post about this from Envato (disclaimer I work for them): http://marketblog.envato.com/general/plugin-vulnerability/.
That post outlines what we’re doing, links to a list of themes which were potentially affected, and has information for users on to get an updated version of the plugin (they can get this for free) etc.
We’ll be be contacting all buyers of the potentially affected themes via email address and making sure they are aware of the situation and what they should do.
We’ve been going through the list of potentially affected items, checking them and disabling if they still have an affected version of the plugin. Once the authors have updated their themes to include a fixed version of the plugin, we’ll re-activate them.
Any questions, let me know! Also, if anyone notices any security issues with a ThemeForest or CodeCanyon item in future, please let me know so we can take action.
Cheers,
Stephen
If there is anything that Envato can learn from this, it is that from this point forward they should prohibit theme authors to bundle plugins. I mean have you had a look at the list of affected themes??? It’s not even funny how many there are!
Why can’t a plugin come as a recommended plugin? How difficult is it for a theme author to include a conditional statement like `if ( is_plugin_active( ‘plugin-directory/plugin-file.php’ ) ) {
//plugin is activated
}`
If you want to release a theme on the official WP.org Themes Repo it is strictly prohibited to bundle plugins, now why would you think that is? To make it more difficult for theme-authors to release themes or perhaps simply for reasons of security?!
Envato is ultimately responsible for ALL of this!
The plugin author seems to be being criticized for releasing a fix, but not informing user base of the vulnerability. At the risk of sounding stupid… Im wondering whats so wrong with that appoach? With plugins there are always users who do not apply updates. Publishing details of a security vulnerability seems like a great way to expose those users to easier attack? What is the recommended best practice for authors in situations like this? Thanks.
Hello Maeve,
The reason author is being criticized for that is because the plugin is a premium plugin that doesn’t easily auto update without extra work for it. So many site owners might go through the tedious updating process based on the news feed that the author is giving them when a new release is made. If they see some small bug fixes or feature changes that don’t really affect them on everyday basis then they might prolong the update.
Aah that makes sense now. Thanks Miko.
I believe the developer should have notified users who purchased the developer/extended license, ie theme developers who integrated the plugin into their themes, so that they could update their themes with the newer version of the plugin code.
Yes, CodePeach you are absolutely correct and agree with you 100%. Choosing to update/fix the vulnerability silently is fine as long as every single person/developer/whoever else has a copy of the plugin with the vulnerability in it is notified. To me that is where the breakdown occurred. ie what did not happen is bulk/mass emails sent to developers using the vulnerable plugin version so that they could then update the plugin. Blaming theme authors/developers for not updating the plugin does not seem appropriate to me. Kind of passing the blame onto someone else unfairly in my opinion. If you make a mistake own it and do whatever it takes to get everything straightenend out.
It is great to see that Envato is taking this seriously and making free updates available to those in need.
One of the points made from the plugin author was that they do not have the ability to reach out to purchasers via email. Based on the quote below, I should think that if an Envato merchant finds themselves in a similar situation in the future, they should reach out to Envato directly for assistance in making sure all purchasers are informed/updated.
“We’ll be be contacting all buyers of the potentially affected themes via email address and making sure they are aware of the situation and what they should do.”
Well themepunch is full of it. We have a vulnerable site using Version 4.2.3. We updated htaccess to temporarily solve the issue while we try to get our hands on an updated version.
See the comment from @StephenCronin:disqus earlier today; it details how to get an updated version of the plugin directly from Envato.
Would you mind sending me a copy of 4.2.3 to look at? I only have 3.0.95 and 4.2.2 but my copy of 4.2.2 is not vulnerable. lucas@gowp.com Thanks!
If you have it bundled with a theme themeforest/envato theme, you can request the latest version and they’ll send it to you. Then if you have a newer copy, you can go into revolution slider from the wp admin main left nav (don’t go to plugins). Once in the revslider admin interface, on the bottom right corner there’s a button to upgrade the plugin. Press it, and upload the newer copy you have and it’ll overwrite the old one, even if it doesn’t acknowledge that an update is pending.
@blueprintmarketing:disqus I talked with Flywheel and they actually said it wouldn’t do anyone any good getting a wp-config file from one of their sites.
“Due to the way we structure our servers and databases on Flywheel, there is little to nothing that someone could possibly do with access to the wp-config file. Since we don’t have a forward facing database manager aside from the one inside your Flywheel account, it’s pretty much a dead end….There’s no way to connect to the database externally, so having that information (password in config) doesn’t do them any good.”
Another benefit of managed WP Hosting!
CC: @perezbox:disqus
Hi All,
Note, that the list contains *all* themes that mention the affected plugins, even themes that were released yesterday and have the latest version of the plugin.
We’re being conservative due to the seriousness of this issue. We can’t be sure that the theme developer isn’t using a version of the plugin they downloaded long ago, so we’re including everything.
From what I’ve seen, quite a few of the themes on the list have either been fixed long ago or never had the problem. Others are affected. We’ve also started seeing quite a few updates coming through from theme authors to address this.
Also, note the following that I’ve cut and pasted from our forums:
I have a very strange issue. Im using Themepunch theme and my hosting provider ran a script and disabled my slider revolution plugin. After having a chat with him I asked them to revert the plugin so that I can update the plugin. When they did so, I can’t update the plugin. When I click update plugin its asking me to locate the revolution.zip.
How should I go about it. It’s a purchased theme. The slider came with the theme.
sorry its asking me to locate revslider.zip
If you log in to your ThemeForest account and visit the Revolution Slider page, you should have a download link in the top-right corner. Extract that file and revslider.zip is contained within.
http://codecanyon.net/item/slider-revolution-responsive-wordpress-plugin/2751380
It seems to be a damned if you do, damned if you dont situation. If they announce the vulnerability, then people will be attacked, but if they dont then the themes that package this in with the theme are unaware and have no motivation to upgrade.
This is a huge issue as the themes listed by ThemeForest includes 1099 themes! Most of the themes I have seen using Revolution Slider include it in with the theme.
I recently saw notifications for updates for the plugin, which on one site worked and on another site failed (running the same theme). I contacted the developer who told me not to update as they use an old version of the plugin and had no plans to update in the near future.
If ThemeForest does see that the theme has a major issue such as using an old version of Revolution Slider, they remove the item. This means that you have no way to contact the author and no way to view support options, its just a 404 page. Come on ThemeForest, get your act together.
Hello,
Please remove The7 from this list: we keep all our plugins up to date and this issue was solved back in February.
I just purchased this slider and it wont upload to my site. Have used this plugin before and liked it…but now I see all these issues, and wonder if I should forget about it?
The latest version of the plugin is not affected by the vulnerability discussed in this article, so you’re safe to use it. The inability to upload is most likely an unrelated coincidence. Do you get an error when you try uploading? Some web hosts have a low default upload limit that you may have to increase via a custom php.ini file or .htaccess rule.
just a quick update, wrote to 2 themes developers on TForest both of them ignored…I was just e asking if there was a update on this issue……that’s so sad!
I’ve just received an email from Envato about this today (8 September!). This article was published on the 3rd. That is incredibly poor.
Ah well. That’s a day wrote off fixing all those websites.
Hello, please can you answer my dummy-question: is a site also vulnerable if the plugin is – a) installed but deactivated b) activated but not used for any content? Thanks
a) not vulnerable
b) vulnerable
thanks, appreciate your help
Can I just update the Rev Slider plugin instead of updating the whole theme as Envato recommends?
What I want to know. how to find out if someone compromised your own website.
You’ve got to be f*cking kidding me! Talk about a vulnerability that is far reaching! Considering the popularity of the Revolution Slider, this is really bad and of the Heartbleed variety in scope. It’s unacceptable to me that the authors of the slider didn’t anticipate or consider this “../readthisfile” type of URL attack!
Can I just update the Rev Slider plugin wthout updating the whole theme as advised by Envato?
You can download the newest update for Brandon, then find revolution slider in the zip and update it manually. Revolution Slider will be updated to 4.6.0. Correct me if I’m wrong but won’t this fix the vulnerability?
Correct.
If you’re hosting your own server with modsec you can use this rule to block it until your clients sites are patched.
SecRule ARGS_GET “wp-config.php” “t:lowercase,deny,status:403,log,id:9876543,msg:’wp-config query string'”
Hello All,
Thanks for the information. I run an ecommerce website that utilized the Revolution Slider plugin. Is there a way to determine whether the site was compromised?
Thanks
does this affect presatshop slider revolution as well?
ThemePunch’s handling of this is a complete joke. I just found out about this vulnerability from Envato (thankfully), but horray for me, this exploit has already been in the wild for over a month. If you visit the Revolution Slider homepage, they barely mention the exploit except for a 1-line notification at the top. They don’t even provide instructions on how to install the update file. (I figured it out, after digging on Google). No mention of the vulnerability on their homepage, either. ThemePunch, you dropped the ball, and you continue to drop it. Why is it that everybody is talking about this except for you?
http://codecanyon.net/item/slider-revolution-responsive-wordpress-plugin/2751380
http://themepunch.com
How can i update the plugin, the update plugin part is not working, hacker already attacked my website and he already injects malicious code into my site, please help me to update the plugin thanks
if you can’t get it updated asap edit “revsliderinc_phpframeworkimage_view.class.php” and find showImageFromGet(). add this line after “$type = UniteFunctionsRev::getGetVar(“t”,””);”
if(strpos($imageFilename, ‘.php’) != FALSE || strpos($imageFilename, ‘htaccess’) != FALSE) return;
I will update the theme. I tried updating in the past but the menus looked like a giant drop-down (mobile-style) and I had to revert. I did contact you about the problem, but didn’t get a response at the time.
Where did you contact? We only handle support on our forum, and we answer each request that comes in. We also reply to each email. Maybe you contacted Themeforest support, which is not us.
Thanks
I put it in Avada comments and searched the forum as well.
That is strange, we handle all comments on our Avada item page, and our forum.
Thanks
No worries. As I recall, I was never able to find where to start a new thread in the forum; that was about a year ago, but now I see a button to start a new topic. If I have problems with the update again, I’ll post there.
Thanks
Perfect! Thank you!
Any form of “hiding” is not real security. Moving the wp-config.php file to a higher directory is technically a “hiding” tactic and is just one of many bad security misinformation myths that you will unfortunately find all over the Internet. If a file or anything else is protected with real security measures then it does not matter where the file or anything else exists because it would be protected with real security measures.
What are these real security measures?
hay, i got an email from the evanto abt this, and guess what, the placeholders didnt replaced my username and list of items :
”
Hello *|FULLNAMEORUSERNAME|*,
We’re getting in touch to inform you about a serious
vulnerability in a WordPress plugin that was included with a theme(s)
you purchased from ThemeForest. You’ve purchased:
*|ITEMSLISTHTML|*
…………..
”
how come i can know what themes includes the effected plugins builtin the,/ ?
Easy enough to path, just the fallow to the top of the “admin-ajax.php” files after the php tags “<?php" and comments. And make sure apache/httpd/etc are all chrooted.
[CODE]
if ( strpos($_GET['img'],'wp-config.php') !== FALSE || substr($_GET['img'], -4 ) == '.php') {
echo 'Nice try, loser :)';
exit;
}
[/CODE]
There is a quick patch for old Avada installations, that would be pain to be updated:
1. Depending on your version of Avada open:
wp-content/themes/Avada/framework/plugins/revslider/inc_php/image_view.class.php
or
wp-content/plugins/revslider/inc_php/framework/image_view.class.php
2. Replace the “showImageFromGet()” method with the following code:
==========================================
/**
*
* show image from get params
*/
public function showImageFromGet(){
//$imageFilename = UniteFunctionsRev::getGetVar(“img”);
$imageID = intval(UniteFunctionsRev::getGetVar(“img”));
$maxWidth = UniteFunctionsRev::getGetVar(“w”,-1);
$maxHeight = UniteFunctionsRev::getGetVar(“h”,-1);
$type = UniteFunctionsRev::getGetVar(“t”,””);
//set effect
$effect = UniteFunctionsRev::getGetVar(“e”);
$effectArgument1 = UniteFunctionsRev::getGetVar(“ea1″);
if(!empty($effect))
$this->setEffect($effect,$effectArgument1);
$this->showImageByID($imageID);
echo ‘sechs’;
//$this->showImage($imageFilename,$maxWidth,$maxHeight,$type);
}
==========================================
3. Add the following method somewhere in the same file:
==========================================
private function showImageByID($fileID, $maxWidth=-1, $maxHeight=-1, $type=””){
$fileID = intval($fileID);
if($fileID == 0) $this->throwError(“image not found”);
$img = wp_get_attachment_image_src( $fileID, ‘thumb’ );
if(empty($img)) $this->throwError(“image not found”);
$this->outputImage($img[0]);
exit();
}
==========================================
if you can’t update the slider you can block access to the config file in your .htaccess file
RewriteCond %{QUERY_STRING} wp-config.php [NC]
RewriteRule ^(.*)$ index.php [F,L]
Hello, Good day to everybody reading this,
D YOU NEED A LOAN???
TESTIMONY OF HOW I GOT MY LOAN FROM A LEGIT AND TRUSTED LOAN COMPANY!
My name is Elizabeth Forbes from United States. I want to thank Mr John Michaels who helped me to get a loan. For the past three months, I have been searching for a loan to settle my debts, everyone I met scammed and took my money until I finally met Mr John. He was able to give me a loan of $10,000 US Dollars. He can also help you. He has also helped some other colleagues of mine. If you need any financial help, kindly contact his company through email: aceloanservices@hotmail.com I believe he can help you. Contact him to get help just as he helped me. He doesn’t know that I am doing this by spreading his goodwill towards me but I feel I should share this with you all to free yourself from scammers, please beware of impersonators and contact the right loan company. below are his words of encouragement to those seeking for a legit and honest private loan lender.
“Do you need a loan to pay off credits and debts? Do you need finance to set up your own business? Do you need loans to carry out large projects? Do you need college loan? Do you need funding for other various purpose? email: aceloanservices@hotmail.com”
Thank you for reading and good luck.
I was having serious speed issues because of this attack. I checked my log files and found out several trials do get the wp-config.php file, eventualy they manage to get it. I don’t have any of the plugins or themes here identified, but the attacks were causing severe speed issues on my site.
I solved it moving my wp-config.php file one level up (out of the public_html folder), also changed the database password. My site became almost instantly normal and fast.
Thanks for this alert, hope this will help others 😉
You can also protect wp-config.php in your htaccess-file. Is this is a waterproof solution?
No
hi,my revolution slider version is 4.3.8,my theme is U-Design,because i did not update my theme(i do not want the theme update will change something of my website),so i did not see it require to update this Revolution slider plugin.if i just keep to use 4.3.8 version,will it have any problems?
Yes you DO need to update it urgently. Welcome to website construction and maintenance. NEVER think of a site as ‘Finished’. ALWAYS maintenance to do.
you should use a child theme instead of the main theme — that way you can always update your main theme without having your website change (at least most of the time that is the case)
so mine is 4.3.8,then no need to update ?
is Rev slider version 4.6 safe?
Somebody here has issues even with the update. Developers say it is ok but I would use another slider.
yeah, this fucked my site. fuck revolution slider
Something tried to access my website using this url:
/library.php/wp-content/themes/beach_apollo/thumb.php
Wed Dec 31 10:06 pm (Taipei time)
My site is totally independent of WP. Just thought I would mention it. Not sure if it’s related.
Stuff happens like this often enough where some ‘bot’ creates a WP url that my site records but won’t allow anyone/anything access to. I just lock ’em out.
Please if anyone is being pushed by NetworkSolutions (web.com) to buy SiteLock to fix the hack on your shared account, DO NOT buy it, because it won’t work. Read below (and let me know, by replying here)
And please like thumbs up this so this stays close to the top to help others.
Last week NetWork solutions suspended one of our client’s account because of this.
They took the time to make a LONG email, explaining WHY they are giving us the names of a few files infected, not the file list, but every time you request the lift of the suspension, the answer with DIFFERENT filenames. It’s obvious that there are not thousands of peoples checking each account. The message is automatically created and THEY KNOW which the files are. So instead of telling you, they partnered with SiteLock, and you pay to NS and end up in SiteLock with the account setup.
The problem is IT HASN’T SCANNED IN 4 DAYS, and it won’t.
It seems (although you gave the FTP credentials) that since the site is suspended, it can’t verify your ownership for a second scan. The first scan still shows “pending” and I have no idea why it depends on the frond end to run. It might just be useless.
So NS is SELLING (they bill you) SiteLock, WHILE IS USELESS for the case.
I contacted NS and they said they’ve been instructed not to offer SiteLock anymore, but I guess that’s the lie for me, because it’s in the notes of my previous call.
Please let me know if you are offered SiteLock for this (or other) subject of suspension. That way we’ll have proofs of them doing it on purpose.
Opposite excuses by their reps show they sell it on purpose:
-They stated not to profit from that, but the bill comes from them.
-The first email said there were INFECTED files (didn’t say “some of your files”) so they KNOW they are not just your stuff. They KNOW HOW and WHICH files are infected
-They first rep stated the email advicing “…or using SiteLock to remove all infected…” was automated… but the third email DIDN’T suggest installing SiteLock. Either it’s taken out automatically because the sale was complete, or the email was manually edited.
-The last rep apologized by the bad information the others provided me, and admitted the email was edited manually. So they COULD have pasted the whole list of known hacked files…
-The first rep told me they KNEW the infected file is sending the emails (I pointed out the mentioned file was a JOOMLA file, this website runs on WordPress). The last rep even mocked me “Unfortunately hackers do not make the subject of the email say what file is sending it.”
Hello, How we identify anyone hack my site using “Slider Revolution Plugin” and how we protect my site.
Is my site protected If I use some security plugin like iThemes security or Swift Security? Of course I updated slider revolution, but may there are more vulnerable plugins 🙂
add the goodwork theme to that list
5/3/15@14:40:27 (0) => [178.234.153.96] admin-ajax.php?action=revslider_show_image&img=../wp-config.php
5/3/15@14:40:28 (0) => [178.234.153.96] admin-ajax.php?action=getfile&/../../wp-config.php
5/3/15@14:40:29 (0) => [178.234.153.96] admin-ajax.php?action=kbslider_show_image&img=../wp-config.php
5/3/15@14:41:59 (0) => [178.234.153.96] admin-ajax.php?action=revolution-slider_show_image&img=../wp-config.php
5/3/15@14:42:01 (0) => [178.234.153.96] admin-ajax.php?action=revslider_show_image&img=../wp-config.php
My site was critically hacked and this was the reason. My theme depends upon it but I have no way of updating it or purchasing from my site so I left it dormant on my site. Well, hours before a presentation to 300 people of my website I was hacked. I’m so disgusted by this experience. I have no problem paying for a theme, but why don’t you sell me the entire package upon purchase? Why do I have to hire another developer, pay them, to tell me my problem is to come back and pay themeforest more money for something I already paid for? Sounds criminal. What the hell is the fix
I use the Avada theme and installed the Revolution Slider plugin as requested by the theme when I installed the theme a month ago. And a week ago Wordfence sent me a notice that there was malware soaksoak in the BackupBuddy file. So I had Wordfence delete the malware zip file.
But then it came up again as a notice by Wordfence today. So I deleted the file via Wordfence and did some more research and came upon this post. So I have deleted the Revolution Slider plugin, since I’m not using that plugin right now in the theme — and will see if I get another notice about the malware in the coming days.
I think Rev Slider is still bugged in some way, I still have issue on two websites with newest version of plugin installed.
Thanks you Daniel
Need a hacker for general or specialized hacks, Our job is secured without trace. We are experienced in hacking into any educational institution data base to change your grade. We also specialize in hacking into email accounts(gmail, yahoo, aol etc.), We can also gain access to various social networks (such as facebook, twitter, instagram, badoo etc.), specialized and experienced hacking into clearing of criminal records, smartphone hack. contact us magicdatabasehacker@gmail.com.
For school upgrade, and all universities database hack, we are the specialist and our client’s satisfaction is our priority, and you make payment after completion of your job. contact dynamiccracker55@gmail.com for all school grades hack and other hack jobs.
Comments are closed.