For the last few weeks we’ve been tracking a very large blackhat SEO spam campaign initiated by basicpills.com, generic-ed-pharmacy.com, getrxpills.com and a few other domains (all located at 212.117.161.190).
They basically infected thousands of WordPress sites and inject spam links directly in their databases (the wp-post table). These are some of the links you will see in an infected site:
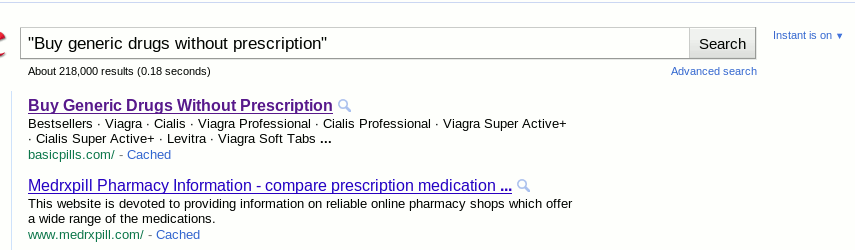
<a href="http://basicpills . com/">online prescription drugs without a prescription..
<a href="http://generic-ed-pharmacy . com/">Buy Generic Viagra Onlin.
<a href="http://getrxpills . com/buy/levi tra.html”>lev itra 10 mg..
What is very annoying for the infected site owners is that those links appear in the middle of the text (sometimes in the middle of other tags). This typically occurs in ALL of their posts making it hard to identify where the dirty links are, and even more of a challenge to remove them. In some of these sites, we’ve seen the attackers create new admin users allowing access back to the site at any time.
Another worrying point is that these spam domains seem to rank pretty well on Google. Their antics seem to be working, just Google for “Buy generic drugs without prescription” for an example:
Whois information for those domains (same people):
Registrant:
Pavel freeh0st@mail.ru +3.80444515342
getrxpills.com
ul.Kalyaeva, 53
Dnepropetrovsk,Dnepropetrovsk,UA 49489Registrant:
Pavel dext@coreimpacts.com +3.80444515342
basicpills.com
ul.Kalyaeva, 53
Dnepropetrovsk,Dnepropetrovsk,UA 49489
Here are some of the infected sites (according to Google all of these domains seem to be shared hosts):
freshdaily.ca
aka.me
www.hugeog.com
www.intrepidusa.com
innovationinteaching.org
spinorbinmusic.com
www.caerlas.org.uk
www.slcan.org
chicagopublictransit.org
acme-web-design.info
idevicepro.com
www.unifemcar.org
aiisf.org
www.jimhudson.org
www.f2a.org
www.aafcs-ca.org
www.jazzbassment.com
ffw.com.br (popular Brazilian portal)
www.b2b-i.com
www.winnipegfolkfestival.ca
www.awrta.org
legoengineering.com
wemc.org
www.ssta.org
www.zentra.com
recitpresco.qc.ca
guildhall.smu.edu
dcms.beloit.edu
timecapsule.asu.edu
moodle.westwind.ab.ca
www.searchengineacademy.com
For the site owners out there, you can check if your site has been infected by scanning it with Sucuri Sitecheck. Sitecheck is our free malware and spam scanner. It will show you if these links have been added, and if you have other security issues. If your site has been hacked, we recommend changing your DB passwords immediately and checking the permissions of your wp-config.php file. If you need help cleaning up the mess, send us an email support@sucuri.net or over at Sucuri.
If you have any questions or comments, please let us know.







6 comments
How do they inject spam via the wp-post table? And how do they created new admin users?
These are essential questions to be able to stop it on our side (WP users)
I have been hit with this on every hosted WP site I run Multi domain names all latest WP code Strong passwords I dont use wp_ for SQL prefix. I am about to lose my mind trying to stop this.
This is getting extremely frustrating, we have removed these things several times and rescanned to see that we were okay and in only a matter of hours we saw that we had malware again. We have also looked at several posts out there outlining how to remove this hack but none of them seem to work. Any suggestions?
Comments are closed.