Update 9/9/16:
We released a new guide to cleaning a hacked WordPress site with our plugin.
If your site has been recently hacked and you are trying to clean it up yourself, we recommend that you use SiteCheck Malware Scanner, our Free WordPress plugin to help you during that task.
The plugin has a collection of useful tools that can guide you along the way. The steps provided here are not final, and there are some variations that require more work, but by just following these steps you will get very far. We will also not rely on any specific signature or malware strings since those can easily be evaded by the clever bad guys.
As always, if you need professional help, the Sucuri team is here for you.
Step 1 – Scan your site remotely (Remote Scanner)
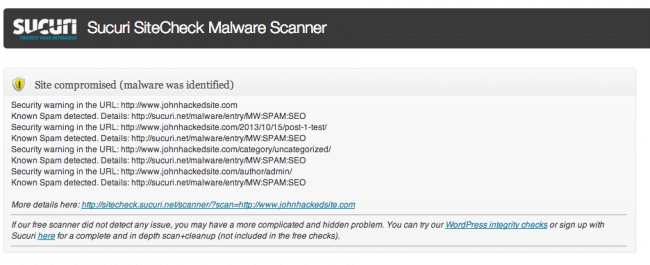
After a site is compromised, it is likely to be used by the bad guys to distribute malware or spam. This can be easily detected by our free remote scanner, SiteCheck.
With our plugin installed, you can click on “Sucuri-Free / Sucuri Scanner” and run the remote scan right from your WordPress dashboard. If the site is infected, you will likely get a warning similar to this one:
Even if the remote scanner doesn’t find anything, you can keep moving to the other tests.
If it does find an injection, you will receive the malicious string detected and a reference link with more details. Keep that saved since it can be useful when cleaning files manually or searching in the database.
Step 2 – Check the integrity of your WordPress core files
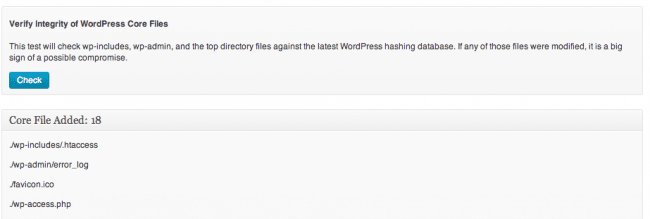
The WordPress core files should never be modified and inside “Sucuri-Free / WordPress Integrity”, you will find a place to verify that they are indeed clean.
If you click on the first test called “Verify Integrity of WordPress Core Files”, you will get a full list of files that are not supposed to be there.
Something like this:
If any file(s) are modified, we recommend reinstalling WordPress by hand. You can do this by removing all top files (along with the wp-includes and wp-admin directories) and re-uploading from a clean source. By replacing and reinstalling, you know the files are fresh and clean and shouldn’t pose a threat.
Step 3 – Check the latest modified files
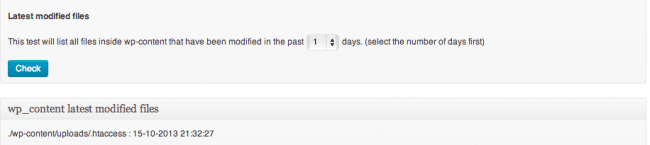
If the WordPress core files are intact, or if you just reinstalled WordPress, there is still one place left where the bad guys can hide their code: wp-content/themes and wp-content/plugins.
If you go back to “Sucuri-Free / WordPress Integrity” in WordPress admin and click on the second test called “Latest modified files”, you can see all the latest modified files. If you noticed that your site was just hacked or blacklisted, any files modified in the last 7 days are likely to be suspicious. You can even go back the last 30 days just to be sure:
If there are too many files modified, you are out of luck. In those cases, we recommend deleting all plugins and themes and reinstalling them manually after. With the plugins, it is not a big deal since typically they aren’t customized. However, we hope you have backups of your theme, especially if you have customized it.
Often times you will notice that just two or three files inside your active theme were modified to serve spam or malware. You can manually fix them by removing the bad code. You can use the results from the first step (remote scanner) as a reference to what to remove.
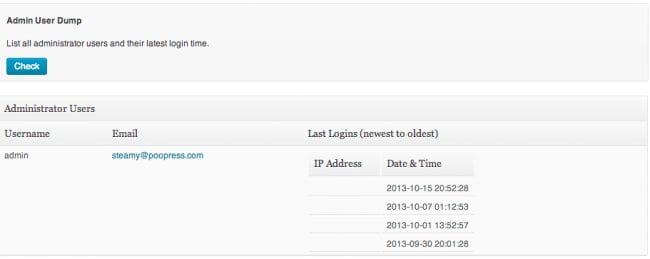
Step 4- List all admin users and their login times
A lot of compromises happen due to stolen passwords, so we recommend you head back to “Sucuri-Free / WordPress Integrity” and click on “Admin List dump”. That will show all admin users that logged in, their IP address and login time.
You can see if someone was able to compromise your admin passwords and get in via wp-admin. Notice that it will only list logins from the time you had the plugin installed. So it might not work 100% if you just installed it after you got hacked.
If your site is currently clean and you are reading this just to learn, I recommend installing the plugin even if just for the “last Login” feature. That will help tremendously if later you find any security issues on your site.
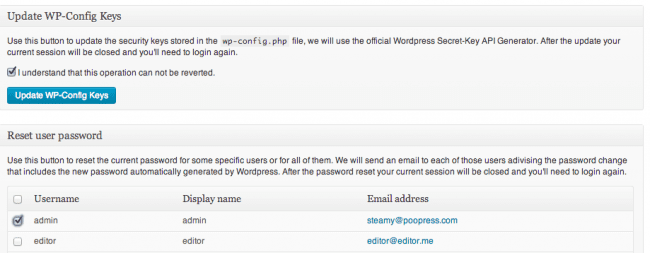
Step 5- Reset all passwords and secret keys
Our plugin has another very nice feature called “Post Hack”. It allows you to reset all passwords and secret keys for all users. We highly recommend that you run this if you have been hacked:
By running this tool you know that any stolen password can’t be used to reinfect your site and that any active session is killed throughout your site. You should also look at the email addresses for each registered user to see if any of them were modified. We often see addresses modified to an email controlled by the bad guys so they can later reset the passwords and get back in.
Step 6- Apply our hardening suggestions
The plugin has a series of hardening suggestions that we also recommend you run. These options can be found under “Sucuri Free / 1-click Hardening”. The main ones would be the Uploads and Wp-content PHP execution hardening.
These hardening options prevent any uploaded or malicious PHP files within the wp-content directory from directly executing.
Additional Files & Protection Steps
These, of course, are just some suggestions for your cleaning up process. You should also look at your .htaccess files and wp-config file to double check them for signs of compromises. If it is spam, you can look at your posts/pages/widgets to see if any of them were modified. If you have root access to your servers, we highly recommend verifying the integrity of Apache/Nginx and their modules, to rule out any server-level compromise.
Lastly, we also suggest that you protect your site with a web application firewall (WAF). A strong WAF will help thwart many of the popular attacks from penetrating your website. Of course, we are biased and highly recommend you check out Sucuri’s Website Firewall 🙂
What else did we miss here? I would love to hear some opinions on additional checks we can take.











10 comments
Wow!! Very cool!!
Thanks so much for this plugin. It is really amazing. I have one question. I am going through the hardening list of items and one of them could not be completed. Specifically that one is related to hardening the wp-content directory. I’m using a Better WP Security plugin through which I changed the name of the wp-content directory to something else as leaving it as default could cause a security issue. Obviously, since the hardening script looks for the wp-content directory it cannot find it as it was renamed. At this point, would you suggest me just updating the hardening.php script under lib directory to use the new name for the wp-content directory? Is there anything else I should be aware of that also needs to change (for both hardening and for the security scan)?
Since I have seen in quite a few places that changing the name for the wp-content directory is recommended (mainly for the new sites), maybe it would be good to have an additional feature to ask the user for their wp-content directory name. That way, the above mentioned issues will be prevented. Looking forward to some guidance.
Thanks so much for an amazing plugin.
Nina
Changing wp-content directory name in sucuri.php and hardening.php files worked for me. I hope it’s not going to break anything else.
So, from your expert standpoint, do you think that changing the wp-content directory is a good idea? I’m just afraid that each plugin will need to be modified as I’m pretty sure that the majority of them look for the wp-content directory as that is a default one.
Thanks a lot,
Nina
It’s really that useful. I tried to install and it helps me very much to prevent malicious. Thank you for sharing.
Very impressive and useful plugin ………. here one more plugin with j query and filters for WordPress http://wordpress.org/plugins/evm-portfolio/
Thanks
Ruby
Hi, I’d like to know how can I remove the alert on top showing last logins. Thanks
It can scan for security WP Theme in case of I download free WP theme version, or any one have a method for scan security for free theme.
Thank
Do you any command line tools, free or paid-for to help sysadmins? Having to install a plugin is fine, but there are obviously many advantages to being able to point a perl/python/ruby script at a WP installation and let it do it’s thing 🙂
lk;kl;l;
Blog is nice. But it only described only one free plugin their are other option available that could also have been added in. If one does not want to use free plugin person can also make its wordpress website free from malware. I read it on some blog called template toaster. They described it in better way.
Comments are closed.