We’ve been scanning and removing malware from websites for years and in this time frame we have seen the website security domain grow by leaps and bounds. Over the same period, the ubiquity of the internet has reached to all corners of the globe, and the number of websites worldwide has skyrocketed (estimated at 955 million and growing). Where do all of those sites live? We decided it would be interesting (and instructive) to look inward at the demographic of hosts within our own construct.
Hosting Companies Sucuri Works With
The good news is that it doesn’t matter what host you choose to work with. It’s likely that we already work with whomever you’re likely to choose, though from time to time we do work with hosts that we didn’t even know about. It’s important to note that some hosts, like managed hosts, don’t actually have their own infrastructure. They resell or sit on top of existing hosts. As such, this investigation doesn’t include those without their own infrastructure.
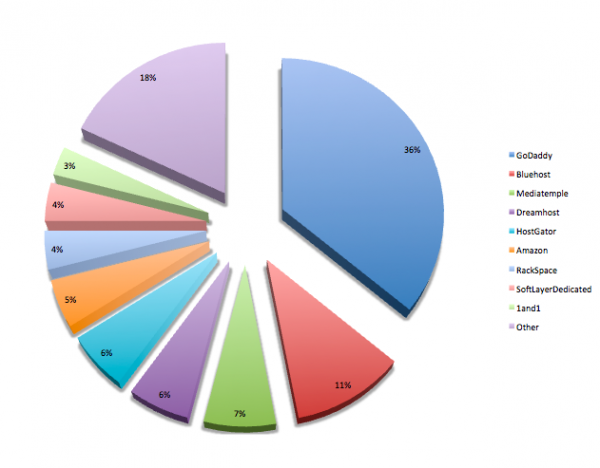
This investigation illustrates that sites on every hosting service get attacked – in pretty pie-graphical form. Regardless of your hosting company, you should always be thinking about how to protect the investment you’ve made in your website. Here is the host distribution within our environment*:
*The distribution of our clients among the hosts does not mean that any one host gets infected more or less than any other, and is reflective of many different factors.
Our goal is to make the internet a safer place for everyone. To that end, even if you are not our client, we have lots of free tools for you to leverage, based on your technical skill level, to insure your website’s integrity. At the, “for everyone” end of the spectrum is SiteCheck, our globally recognized tool for malware scanning, which can be used to remotely scan any website for malware, spam, defacements or blacklisting. Be sure to read up on how SiteCheck works before using to ensure you understand what it detects, and its limitations.
If you want to automate SiteCheck scans and be alerted if your site is attacked, you can always Does Sucuri Work With My Host? Yes, Yes We Do.subscribe to our service and enjoy daily scans and unlimited malware removal. Alternatively, if you use a platform like WordPress you can embed SiteCheck within your dashboard. In this way, if you have the technical acumen, you can use our free tools to detect malware and fix your own website.
For everyday website owners wanting to make sure they’re browsing the web safely, be sure to leverage our SiteCheck extensions for Chrome and Firefox. Like we said, our mission is to make the internet a safe place, and one way to do that is by ensuring that everyone browses clean websites.
Moving up the technical ladder, you can use DDecode, which is our PHP decoder. This is specifically meant for developers, designers and system administrators. If you’ve found a strange payload on your box, we want to see it. If we can’t reverse engineer it automatically through our PHP decoder, then engage our research team via Twitter or Email. We’re always up for a new challenge.
For website owners looking to make attacks stop, regardless of host, look into Website Firewall solution, which is also included with our AntiVirus plans. If you run your own stack, we recommend using a product like ModSecurity. We also strongly recommend that you architect an environment in which you separate the WAF from the web server and leverage technologies like NGINX at the edge.
Or, you could use our Sucuri Website Firewall and save yourself the headache. Did we mention that?
Questions to Ask Yourself Before Engaging a Host
We’ve learned a lot about hosting providers over the last couple of years. One very important distinction to make between them is that each host has their own preferred method of handling website security issues. Some like to throw the kitchen sink at the problem and others place the burden squarely on website owners. Neither of these methods is wrong, but it is important for you to understand what you need to protect your website. Our advice is to do your homework and find the best host for your website.
To that end, we’ve put together a primer of questions below that are based on our clients’ experience with hosting providers. We would ask these questions to any host taking care of our own website:
- What is the host’s response to a website being hacked?
- Will the host stop or prevent website attacks?
- Does the host use it’s own technology, or do they leverage a third party?
- If they leverage a third-party, does that party use it’s own technology or is that leveraged from a fourth party?
- What is the host’s response to a hack? Will they shut you down? Will they tell you that you are hacked or will you find out from your clients when they can’t reach your website anymore?
- If they shut you down, what is their protocol for getting you back up?
- Do they offer you a backup service? If so, how far back does it go?
- Will they help you fix the problem?
- How do they stay current with the latest threats and trends?
- What happens if you get reinfected?
- What is their response time when and if your site gets hacked?
- What assurance can they provide around the management of their stack?
- What happens in the event your website is blacklisted? Do you know what a blacklist is?
- How will the host handle your website in the event of a Denial of Service or Brute Force attack?
My Host Partners With Another Web Security Firm
That’s great. We won’t hold it against you for long.
In all seriousness, there are a lot of website security providers providing a lot of different options for website owners. In fact, most of the hosts in the graph that lead off this post are partnered with another security vendor, yet those websites still found their way to us. In some cases, we work in conjunction with a service provided by the partnered security firm. For instance, another firm may specialize in website backups. While we have a backup product for clients, our focus is on malware detection, removal and prevention.
In other cases, our client websites have come to us because they love that we bundle our malware monitoring and removal plans into one easy-to-understand price. They’ve found that the low introductory offer to website security that their host negotiated only covers malware monitoring. When their website gets hacked, they find that the company they thought would clean their site is actually going to charge an exorbitant amount to do so and they look for other options.
As we’ve said before, there are a lot of options for website security and we’d recommend that you choose the one that’s right for your website. We’re confident in saying that because we truly believe that when you do your homework, you’ll choose Sucuri.










10 comments
Hi Austin,
How can I contact you by email?
Hi there! Feel free to email us at info@sucuri.net, we would be happy to connect.
Thanks,
Dre
This engaging article is a needed corrective, a whirlwind tour of the latest developments in Website owners, Website security, Host, and other fields…Austin make a compelling case for optimism over dread as we face the exhilarating unknown.
Skype
Very happy to partner with Sucuri. Our customers feel safe to know that we monitor for malware using Sucuri. It malware is detected then Sucuri is very quick to remove it. Excellent service! Thank you guys.
Hey Guys
Thanks for the kind note! It’s a pleasure working with you guys as well.
Tony
If it’s true that Flywheel uses Sucuri as they state here (https://getflywheel.com/why-flywheel/wordpress-security/), I can tell your product doesn’t work very well.
We’ve had 3 sites show malicious code that we have caught in manual inspections, and the same hack appearing twice in one week.
Hi @disqus_Xs5KyhqLsR:disqus
That’s not a fare statement at all. Those that partner with us, like Flywheel have unique relationships that may or may not leverage all our toolsets.
I’d encourage you to leverage something like our Website Firewall, you should check with your host to see if it’s part of their relationship with us.
As for reinfections, remember that not all reinfections are the fault of the host, and many often come down to the website owners. Things like keeping their environment up to date, but more importantly keeping the environment clean. One of the biggest issues we see with reinfections is cross-site contamination.
As you don’t have an account with us directly, have Flywheel provide you a bit more information as to why this is happening.
If you have any further issues, here is my email: tony@sucuri.net
Thanks
Tony
No, I don’t know to what extent Flywheel uses your products, I figured you’d know more about that than me, they are your customer after all.
But I can tell you that Flywheel is a one-site-per-server host. So I doubt cross site contamination.
As for the hacks, Flywheel don’t seem to know much about why it is happening, they just
tell me Sucuri says it’s clean, then a few days later the same hack
appears.
As I understand it, your product is supposed to monitor, learn and then clean up, so repeat hacks of the same type, that get caught by manual inspection, and removed manually seem to indicate something isn’t working – hence, I say your product doesn’t work. Of course we notify Flywheel each time, provide the infected files etc.
Fact is, we have had multiple, repeat hacks on a host that credits you guys heavily for their security.
HI @disqus_Xs5KyhqLsR:disqus
We don’t publicly discuss anything regarding our customers. What I can say is that the full security suite is offered directly to our customers, not through partnerships.
As for your specific situation, I assure you that engaging directly with us will likely render you a much more favorable outcome. I can’t speak specifically to your challenges without directly accessing the environment. What I can tell you is we deal with reinfection cases like yours a lot, and once in our environment we’re able to make them stop.
It sounds like there is a point of entry that is not being patched, likely a vulnerability in the code being exploited.
Hard to say without more details.. but I don’t think blaming our team or tech is adequate, being you’ve never engaged us directly.
Thanks
Comments are closed.