Phishing scams are always bad news, and in light of the Google Drive scam that made the rounds again last week, we thought we’d tell the story of some spam that was delivered into my own inbox because even security researchers, with well though-out email block rules, still get SPAM in our inboxes from time to time.
Here’s where the story begins:
Today, among all the spam that I get in my inbox, one phishing email somehow made its way through all of my block rules.
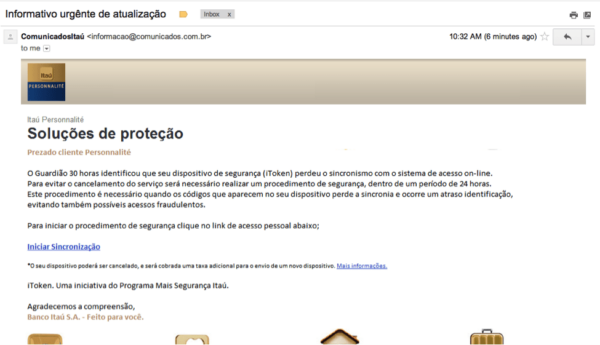
I decided to look into it a little further. Of course, I wanted to know whether or not we were already blocking the phishing page, but I also wanted to investigate further and see if I could figure out where it came from. Was it from a compromised site or a trojanized computer?
The investigation started with the mail headers (identifying addresses have been changed, mostly to protect my email ☺):
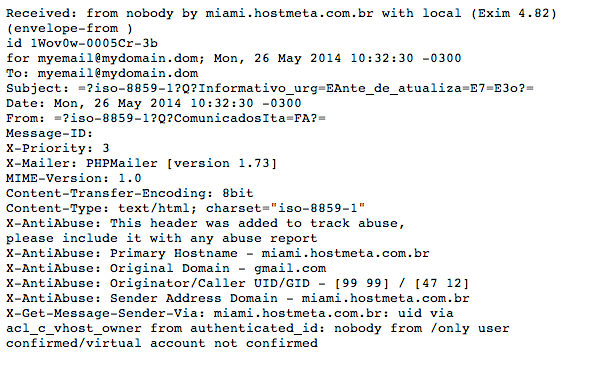
The headers tell us that miami.hostmeta.com.br is being used to send the spam. It’s also an alert that some of the sites in this shared server are likely vulnerable to the form: X-Mailer: PHPMailer [version 1.73]. I decided to look into the server and found that it contained quite a few problems. This server hosts about twenty sites, some of which are outdated–WordPress 2.9.2 is the oldest–while others are disclosing outdated web server versions (Outdated Web Server Apache Found: Apache/2.2.22) and still others are blacklisted (http://www.siteadvisor.com/sites/presten.com.br). This makes it pretty difficult to tell where the spam came from, right?
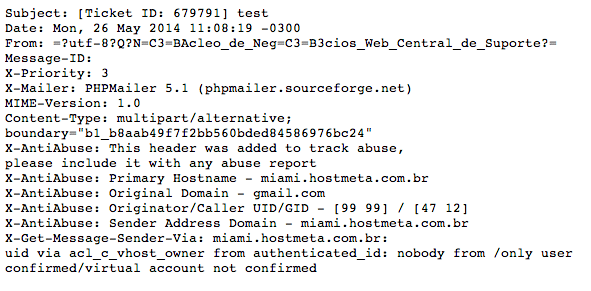
Luckily, there’s another header to help us, Message-ID:. nucleodenegociosweb.com.br is hosted on miami.hostmeta.com.br and it has an open contact form. I used it to send a test message and although the headers are similar, the PHPMailer differs:
What Do We Know Now?
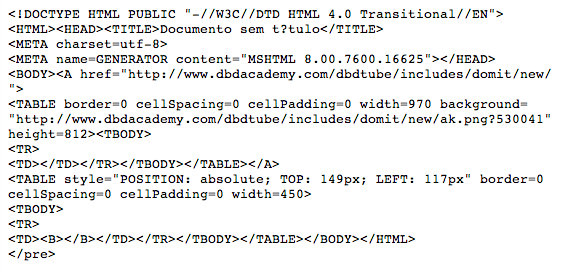
We know who is sending the phishing messages, but what host are they coming from? There are some clues in the message body:
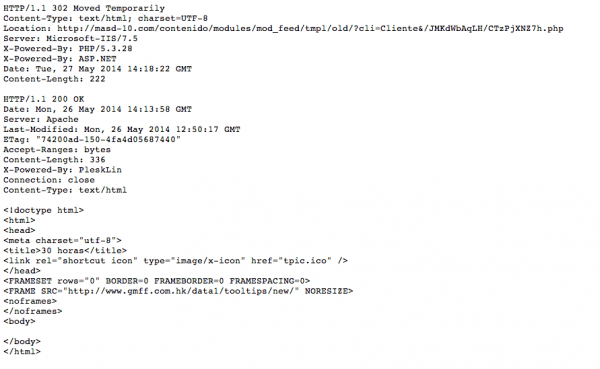
From that image, we can see that http://www.dbdacademy.com/dbdtube/includes/domit/new/ is hosting the image and the link to the phishing scam, but it doesn’t end there. As you can see from the content below, we’ll be served a redirect to http://masd-10.com/contenido/modules/mod_feed/tmpl/old/?cli=Cliente&/JMKdWbAqLH/CTzPjXNZ7h.php, which loads an iframe hosted on http://www.gmff.com.hk/data1/tooltips/new/.
Problem Solved – Or is It?
In this case, there are three compromised sites being used to deliver the phishing campaign and it’s becoming very common to see this strategy being adopted. The problem from the bad guy’s point of view, is that if they store all of their campaign components on one site, then they lose all of their work when we come in and clean the website. If they split the components up and place them on multiple sites, with different site owners, then it’s unlikely that all of the sites will be cleaned at one time, which means their scam can continue.
As always with malware, it’s not enough for your site to be clean. You also need to rely on everyone else to keep their own site clean. When others don’t, your computer or website can be put at risk.
If you’re interested in technical notes regarding the type of research we do be sure to follow us on Twitter and be sure to check in with our Lab Notes. If you something interesting you’d like us analyze please don’t hesitate to ping us, we’re always looking for a new challenge.








6 comments
We regularly phish our users. One of the most interesting data points is that over 50% of those who fall victim will click on the link within the first five minutes. More than 40% of those who fall victim will click on the link within the first fifteen minutes. So, the vast majority of responses will be minutes after the campaign starts. This is good for the bad guys, because it means that the effects of their campaign can be realized very quickly, and if the web site if cleaned up even a short time after the campaign starts, it doesn’t do them much harm.
Wow, that’s really interesting data.. would you have raw stats you can share on these tests?
Tony, I’ll PM you on G+. This is all I really can share publically.
Nice article. I think you mean “thought-out”.
These seem to be going the same way as command and control systems with one main infected website followed by many child sites redirecting or iframing and then further child sites doing the same. As you pointed out, this way one site cleaned does not destroy their network, unless it is the main site. Could the code possibly include more than one source so if the parent site is removed, it changes to point to other parent sites?
Hey David,
Interesting point. I’ve already saw some reverse backdoors written in perl with this feature, grabbing a list of servers from a file and updating it periodically, and it is easy to implement for any other kind of malware. I’ll check our samples database for something like that. By the way, it can turn into a good blogpost if we have any of it 🙂
Thanks for your feedback
Thank you. I remember reading about how the C&C servers regularly changed their sources. As the FBI shut down one C&C server, another would be used.
Comments are closed.