While analyzing our website firewall logs we discovered an old vulnerability being retargeted in RevSlider, a popular WordPress plugin. In 2014 / 2015, this led to massive website compromises. Now it’s being leveraged again in a new attempt to infect websites. The patched version (4.2) was released February 2014. Many websites remain outdated and are being targeted under a new wave of attacks.
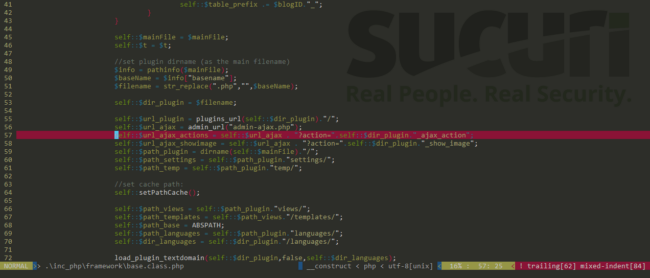
The original hack required sending an AJAX request containing the action revslider_ajax_action to the vulnerable site along with the malicious payload. Due to the severity, many hosts deployed ModSecurity to virtually patch and block this attack. In the new variation, the attack sequence is modifying the action to revolution_slider-ajax-action.
This variation was detected by our analyst Keir Desaily. It turns out that certain themes using revolution slider leverage a different folder name to store its data, replacing “revslider” by “revolution-slider”. As the code uses the plugin directory as the name for its AJAX actions, this permits the attacker to change their exploit, successfully compromising websites. Most ModSecurity and prevention techniques deployed since the vulnerability was released are filtering the original attack and are considered static and stale.
All CloudProxy customers are not affected by this new variation.
Malware Analysis – IRC Botnet
During the analysis of this new exploit variation we spent time looking at the backdoor it was trying to communicate with. It turns out the attackers were pushing a zombie script to connect to an IRC botnet where it would receive the orders from the Command and Control (C&C).
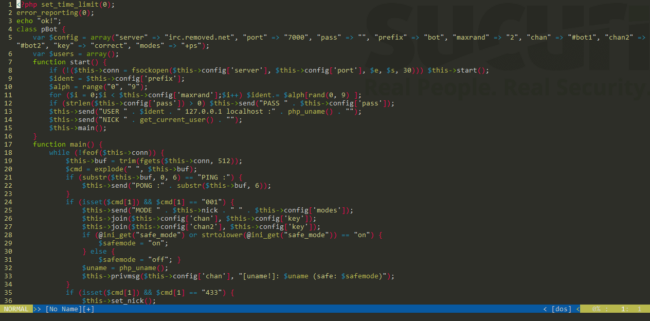
Botnets are common, they can spread the infection through a website’s resource while simultaneously building a mesh network to cover their traces. Using IRC as a command center is popular among botnet as they are easy to operate from a distance and provide a stable connection to the bots.
This particular script has been used in website hacking since 2012 and yet the functions of this variation are very limited. While it can execute arbitrary commands, it cannot automatically perform tasks which require a complete script to be sent with every command.
We simulated being one of these bots to monitor the activity of the server. This led us to a small IRC network with dozens of zombies leaking hundreds of unique WordPress databases credentials. Monitoring this channel gave us insights into how it operates the bot to expand the infection rate.
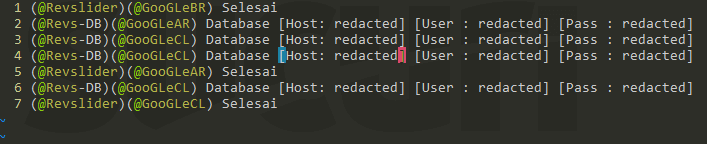
We know that Google asks for CAPTCHAS after a certain number of searches have been reached. These bots had devised a way to perform Google searches, evading their CAPTCHA feature, enabling them to find and target more vulnerable sites. This attack sequence can be described as an evolution of the previous attack Denis shared. Each bot searches for specific terms and extensions, leveraging different Google Top Level Domains (TLD). Google has over 200 domains. This allows the attacker to multiply their search range by 200. The technique seems to be efficient, rendering over 800 database credentials from different sites in less than two days.
While pretending to be a bot, we received various commands to execute:
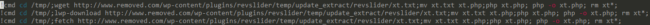
This script tries to download a text file from another infected server part of their network, execute it, then delete all traces of itself. The content of the file remains a mystery as it had already been removed from the server when we attempted to download it. From previous experience, it would likely force our site in brute force or DDoS attacks.
Exploit Target – Revslider
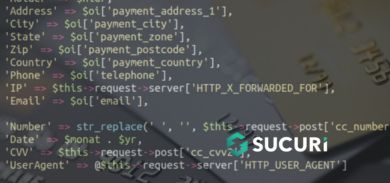
From the dorks used, we were able to find out that they were searching for WordPress installations containing a vulnerable version of RevSlider. Once a vulnerable target is found, gaining administrator access is straightforward.
Once a target is compromised, scripts are added to the compromised server and the attackers network.
Password Statistics
From the 800 sets of credentials pulled from the network, 40 of these had the year the website had been built in, in the password (i.e, such as WP_SiteName2016). While it may be an easy way to memorize the password, using a date lowers the entropy of the password which makes it predictable!
For more information on passwords, read through the Dynamics of Passwords article in which we share some best practices.
Patch As Soon As Possible
If you’re using a vulnerable version of RevSlider, update or patch as soon as possible! In the event you’re unable, we strongly recommend leveraging our Website Firewall or equivalent technology to get it patched virtually.









4 comments
How to patch? Which version is secure?
This is an old vulnerability dating from Feb. 2014, everything over version 4.2 is patched
Are you sure about that? I still see compromised wordpress sites out there with version 5.1.6 installed. Serving up exploit kit nonetheless. Not to mention this article is only less than two months old, if it were me, I would get rid of this plugin given the past..
Does that compromise the web server or the server itself?
I used to run my webserver on my server at home. The webserver is turned off now, but the Server is of course still active. I get these Google capcha requests once in a while when I google, telling me there’s suspicious activity from my Network. Also I discovered that the my symantec AV scanner quarantined a few files from revslider directories.
So my suspicion is, the Server is infected. maybe from running the Webserver in 2014 with a Website using revslider. But how do I find that out for sure and how can I remove the bot/trojan? Can you point me to a site with help?
j.
Comments are closed.