Having your website hacked can be a devastating experience for any website owner. Unfortunately, many website owners rarely know they are infected until days, if not weeks, after the compromise has occurred. Their notification comes in the form of a blacklist or some other alert, including notifications from their users. Neither is ideal. So how are website owners supposed to know when their site is hacked?
Fortunately, there a number of tools designed to help, but all depend on one critical element – you – the website owner to be actively engaged in the administration of your site. We couple this active administration with a basic understanding of the attacker’s actions on objectives (i.e. their goals after successful penetration) and we find ourselves better situated to quickly identify, mitigate, and if necessary, remediate a hack.
These are some common actions on objectives you can expect if a hack is successful:
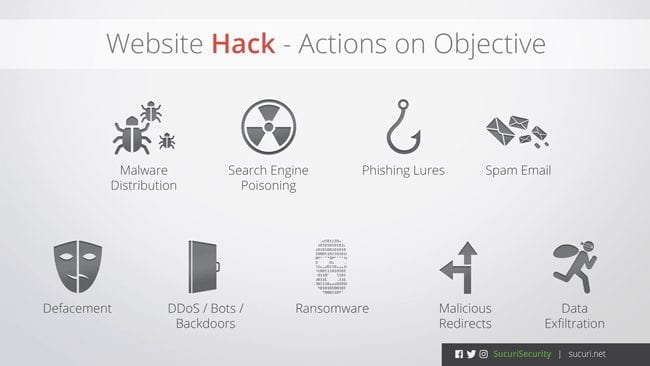
These examples illustrate that not all actions on objectives are the same when it comes to what the attacker hopes to achieve. As such, how we go about identifying specific hacks and the tools we leverage will vary.
4 Tips To Identifying a Website Hack
Because of the various ways a website can get hacked, and the number of things cybercriminals can do if successful (i.e., actions on objective), we have to complement the symptoms with potential Indicators of Compromise (IoC). With this, we can configure and effectively deploy tools to assist us in the process.
1 – Change Detection
As a non-technical website owner, the greatest asset you have at your disposal is integrity monitoring. You can think of integrity monitoring as a way to identify when something changes from the baseline. This type of monitoring should include a log of modifications, from pages, databases, and server files, to the addition of files or server-level changes (including permissions).
Change detection will not indicate whether the change is right or wrong though. Making that call falls on the website owner. The tool will only tell you when something has been modified and worth taking the time to investigate further.
For my personal change detection, I use a number of tools.
- For server-level integrity monitoring I leverage OSSEC HIDS on my web servers.
- For my WordPress installations, I use the free Sucuri WordPress plugin.
Configuring your tools to report on integrity issues can be timely, but please don’t skip this step. Tune your tools. Every system, and associated applications, functions differently. If you don’t take the time to tune, you’ll find yourself regretting it; the notifications will consume you.
There are different schools of thought on this, but for us, the key to successful monitoring are the things that mean the most. For instance, if I know that the uploads directory requires files to be uploaded, I don’t want to be notified when files get added. I do want to know though if someone makes a change to the .htaccess file that disabled PHP execution in the uploads directory.
To make things easier, you want to integrate alerts into existing workflows. So if you depend on email for operational actions, then focus on email alerts. If you depend on tools like Slack, or SMS, find ways to integrate them into existing monitoring systems. Reason being, things that require us to change our habits are rarely adopted, while things that fall right into the existing systems seem to be more readily adopted.
We’ve shared techniques in the past showing you how integrating the Sucuri plugin with OSSEC feeds into an alerting system (like Slack or PagerDuty) to provide an easy way to get the visibility you require.
2 – System & Access Monitoring
Along the same lines of change detection, we have to keep a close eye on who is accessing the website and its associated web server. This includes monitoring what accounts are being created and when people log on to the system. In short, add visibility within roles.
- Was someone’s account changed from author to administrator? Why?
- Was a new user added? Why?
There should be a procedure in place that logs the account creation process, as well as an inventory of users and their associated roles and rights. A number of tools (depending on your platform) have been designed to notify when these type of events occur.
This type of monitoring is critical when you consider how attackers operate. In many instances, most attackers will create malicious users within your site with the hopes of using them in the future. Additionally, these accounts often go unnoticed. Any new, unauthorized accounts in your system is a very strong IoC.
3 – Free Online Scanners
One of the best resources will be scanners designed to see things that you can’t. This includes hacks that target specific devices or Search Engine Result Pages (SERP). Online scanners can help show you what only certain visitors or Googlebot are seeing.
A couple of tools to consider include:
The first three scanners are what you would refer to as remote scanners. These scanners see how your website responds to requests from different browsers, devices, and user-agents, in the hopes that it can identify a specific issue. We’ve shared information in the past providing some clarity on how these remote scanners work. Yes, remote scanners look for and identify very different issues than scanners you might deploy locally (within the application or web server). These scanners depend on scraping and spoofing to display content remotely, which identifies a very large number of infections, but not actions on objectives such as adding your server to a botnet, abusing your server resources (i.e., DDoS / mailer scripts) or using your site as part of spear phishing campaigns.
VirusTotal doesn’t perform its own scan, but it aggregates a number of different blacklist engines, allowing it to check the state of your site across many different providers at the same time.
4 – Free Online Monitors
The most underutilized resource is likely the free online monitors. A number of technology providers like Google, Bing, Norton and many others offer website owners the ability to monitor their websites for free via their webmaster tools (i.e., Google Search Console, Bing Webmaster Tools). The tools are built by other search engines like Yandex Webmaster and a number of other organizations like Norton Webmaster.
No tool will be 100% accurate but it never hurts to leverage a couple, especially since they are free.
It’s unlikely that the resources at your disposal, whether a large organization or a small business, are able to match the monitoring capability of all these entities combined. Configuring is easy, and when something is identified as a potential issue, you are notified via email. They look specifically for malware (i.e., drive-by-downloads), phishing and SEO spam. However, I forewarn you, that all solutions have the potential for false positives. Getting flagged by one doesn’t mean the others will flag your site. If more than one does, that’s usually a strong indicator of a problem. Also, each of them have their own process for clearing warnings; some can take a couple of days, while others weeks.
Website Security is a Continuous Process
As website owners, we have subscribed to be today’s webmasters. The term might not resonate with you, but it’s the reality. Yes, many simply want to hand off their problems to someone else or defer to the commoditization of website creation, deployment, and maintenance. This mindset will continue to be the Achilles heel to the larger website security ecosystem. We have to do our best to be responsible website owners and remember that security is a continuous process.
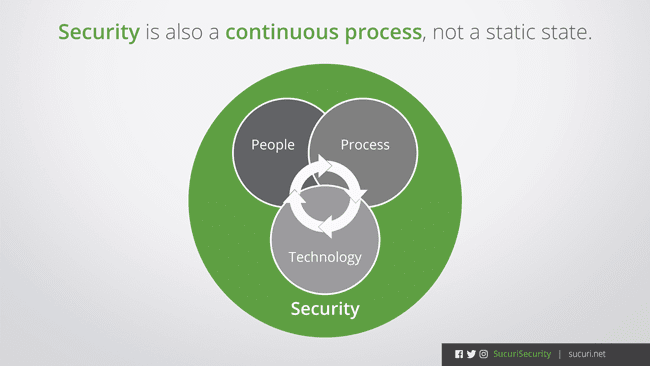
In many of the incident response and forensic cases we work on, there are usually a number of signs that could, and should have, triggered an IoC worth investigating. These triggers could have mitigated an attack. One of the few instances where this doesn’t apply is with malvertising (i.e., an attacker abuses your site without compromising it, but abusing the trust with a third-party integrator – the ad network). There is almost a footprint created somewhere in the process though. Through active monitoring and website administration, we should be able to have everything in place to quickly identify, mitigate, and remediate hacks.
If you prefer to complement your security controls with a professional website security organization, Sucuri can help.









5 comments
Really appreciate this article and some of the tips in it!
You’re very welcome @kassandra 🙂
We are technology expert ,We provide Microsoft Support,Windows Support,MS Office Support for further information dial our microsoft Support TOLL FREE NUMBER,
Support for microsoft windows toll free,
Support for microsoft MS Office toll free
Windows Technical Support number,
Windows Online,
Windows 10 Support Contact Number
Intuit Support Number,
microsoft Tech Support,
MS office Toll Free Number,
Windows 8 contact number,
Internet Explorer Technical Support Number
windows 10 support
windows 8 support
windows 7 support
windows vista support
windows xp support
windows office support
Tony, you never cease to amaze me for two very different reasons.
1- You really know your stuff.
2- Sadly, you are unable to communicate that in a way that the AVERAGE USER, the users that should be the target audience for this article, can understand.
There’s maybe one author of the Sucuri blog who writes in plain English… the rest of you use IT/ITSEC buzzwords as if you’re getting paid per buzzword.
Hello??? You’re missing your target audience! I would love to recommend our users to you, but it’s not worth the time I’d lose in translating from geek-speak to plain English.
Hi @davidfraiser:disqus
Thank you for your thoughtful critique. It’s definitely a struggle finding a balance and accounting for the many different audiences that depend on the things we share.
If nothing else, this should provide you the level of confidence you need in our knowledge of the space we operate in. Something that should also give your customers some peace of mind as well. Remember, when website owners enlist us for their website security they’re getting the products and services we’ve built, but also the knowledge we’ve gained over the years. They should see this as a positive, not a negative.
I do agree, IT/ITSEC buzzwords can be challenging, but I assure you we try to avoid buzzwords and stick to factoids and abbreviations when possible. Our purist tendencies makes it difficult not to call something but by it’s rightful name (which could appear to be buzzword like).
I truly appreciate your feedback..
Tony
Comments are closed.