Remediating over 500 infected sites per day, we see attacks executed at varying levels of complexity. The tactics attackers use to compromise a site provide insight into their motives.
Some write elegant code and cover their trails carefully, while others create simple attacks that can be applied broadly but aren’t well concealed.
Spammers never cease in their quest to make use of resources of hacked sites, especially in black hat SEO schemes. In most cases, spam injections and doorway scripts are quite hard to detect. This case however, was different in that the attackers did not put much effort into hiding their presence from the website owner.
Abusing Server Resources
In this spam investigation, we analyzed a case in which the attackers were hacking sites to profit from their SEO and take advantage of server resources. The technique consists of abusing storage and database resources by installing spammy WordPress sites (Oakley and Ray Ban spam in our case) in subdirectories of the original site. We have seen instances of this before and apparently the tactic is still working for spammers.
Below is an example of a subsite that was installed on the hacked WordPress site.
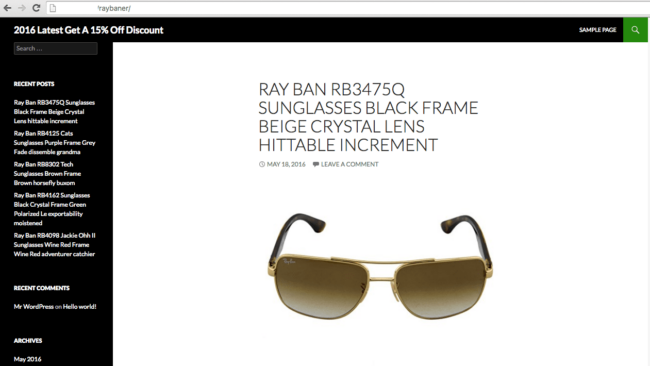
Unlike malicious redirects or defacements, this type of hack does not change the appearance of the infected site. The tactic used here includes hiding malicious sites within the legitimate site’s directory. By installing their spammy sites in subdirectories, they often avoid detection by the website owner while still abusing their resources. Website owners who don’t monitor the security of their site may not discover the attack until they hear complaints from visitors, get blacklisted, or receive a notification from their hosting provider.
Identifying Patterns
With SEO spam, there seems to be no end in sight; hackers continue to develop new ways of infecting sites. In order to combat this, a critical responsibility of our research and remediation teams is to identify patterns.
During our investigation, we identified three similarities amongst websites infected with this type of injection.
- 1. The attackers added 2 directories in the root (./oakleyer and ./raybaner) with WordPress installations (v4.0.12).
- 2. Attackers took the database credentials from the original site’s wp-config.php, and used different table prefixes for the spammy WordPress subsites.
- 3. There were also four specific files that helped automate blog management in both ./oakleyer/wp-admin and ./raybaner/wp-admin:
- etchk.php – verifies if there is a post in the database with a given title.
- etpost.php – creates or updates spam posts in the database.
- etreply.php – posts comments.
- map.php – creates sitemaps for the SPAM sub-sites.
Instead of using an XML-RPC API (a remote procedure call) to update the sub-sites, we see that they inserted four .php files to automate WordPress management. Automating blog management allows the hackers to update posts and comments on multiple spammy sub-sites at once.
Utilizing Google Search Console
How do you know if an attacker is spamming your site?
While not a comprehensive exploration, a quick check can easily be done via Google Search Console. If you see unrelated search queries, it’s a strong indication of an SEO hack. Another simple search of [site:you-site-domain-here.com cheap] can also provide insight. Keywords like “cheap” and “free” are often used by spammers. These are good terms to check if you suspect that your site may be hacked. If the search returns pages that don’t belong to your site, spammers may be using it.
In this case, it was easy to identify the malicious directories in the site root. The straightforward naming conventions (./oakleyer and ./raybaner) used for the additional directories clearly indicated that we had found the sunglasses spam location. However, it is unrealistic to manually check the integrity of your site’s files and directory structure consistently. In fact, many hackers count on the fact that website owners are not staying vigilant.
A more reliable approach is integrity monitoring of your server file structure as part of a complete website security solution.










3 comments
Wow crazy heads can find new ways.
Dear Barbosa,
Thanks for your important tips about SEO attack! Please keep up dating information.
Thanks,
S.Das
CEO – SEO Company in India
The question I have with this attack is why? I doubt Oakley or ray ban are part of this so what do the hacker have to benefit. This seems very odd to me. Can anyone shed light on what is the purpose of this attack?
Comments are closed.