We’ve covered a lot of personal security practices, but many people forget how important it is to secure mobile devices, which are riddled with personal information. Website owners should consider how their entire digital life can impact the security of their website and visitors.
If your phone is compromised, website access can be impacted through access to credentials and sensitive apps like email. I will also admit that some of this is a bit paranoid and has to do more with privacy than security – but for me, both go together.
For the best security, adjust your settings when you first receive a device. If you have been using your device for some time without proper security, you might consider reformatting the device to factory settings first.
1. Security Settings
Whether you use iOS or Android, you should become familiar with the security settings and adjust them to suit your preferred balance of security and convenience.
i. Unlocking Your Phone
It’s important to keep your phone locked with a password that is difficult to crack.
Apple and Android (7+) both do a decent job of encrypting data, but the level of security depends on the password you use to unlock your device.
Note: If you are running an older version of Android, you can encrypt your device manually under the Security settings. It may take some time to complete, so do it during a time when you don’t need your phone for at least an hour.
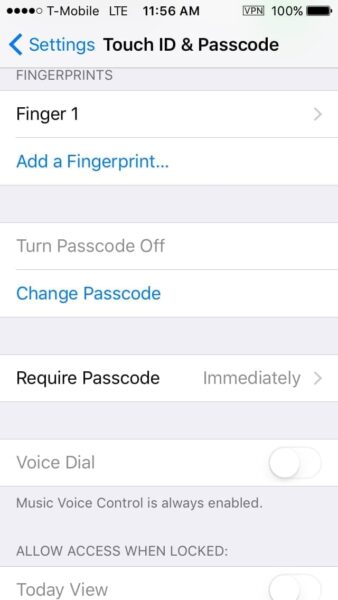
- iOS: Settings > Touch ID & Passcode
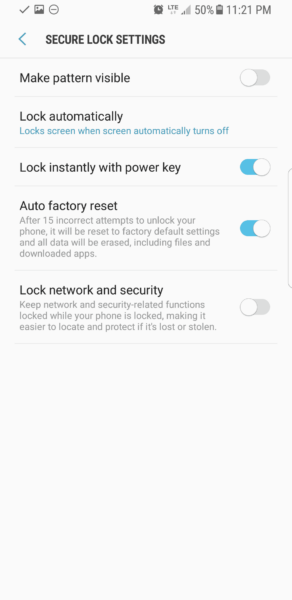
- Android: Settings > Lock Screen & Security
I recommend using an alphanumeric password with 10+ characters, or a numerical PIN with 15+ characters.
Pattern-based passwords can be problematic because streaks on the screen can make your pattern easy to guess. Contrary to popular belief, your fingerprint is not as secure as it seems. Think about how many places your finger touches that the fingerprint could possibly be copied.
ii. Lock Features
For Android, I don’t recommend using the Smart Lock options as they can be easily bypassed by a determined attacker – these include options like unlock by voice, facial recognition, an iris scanner, and proximity to certain locations or devices.
For iOS, I recommend turning off Siri (Settings > Siri) as there have been exploits discovered in the past to use Siri in order to bypass the Lock Screen without the passcode. For the “allow access when locked” section, I have everything off, and personally do not get the point of this “feature”. Allow someone with physical access to your phone to get information?
iii. Lock Screen Timeout
I ensure that the password is required immediately after locking the screen. I would say the longest amount of time that I would consider safe is after 1 minute.
Under the Display settings, I also selected to turn off the screen “after 15 seconds of inactivity.”
iv. Reset Phone Setting
If too many password attempts have failed, the phone can be automatically erased and reset to factory settings.
On iOS, I have the Erase Data feature turned on. On Android, this feature is called Auto factory reset.
For those concerned about losing data, I recommend using your computer for weekly backups (making sure to use the encrypted option for the backup).
v. Backups
I do not recommend backing up to iCloud or Google. While the data is encrypted in transit, Apple or Google still can get access to it and they maintain the key for it. Therefore, I prefer to use encrypted weekly backups to my computer.
- iOS: Settings > iCloud
- Android: Settings > Cloud and Accounts
vii. Notifications
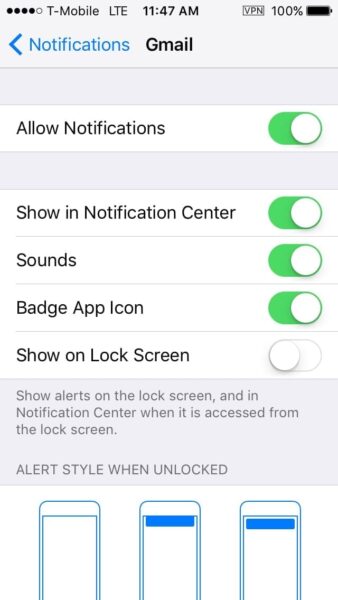
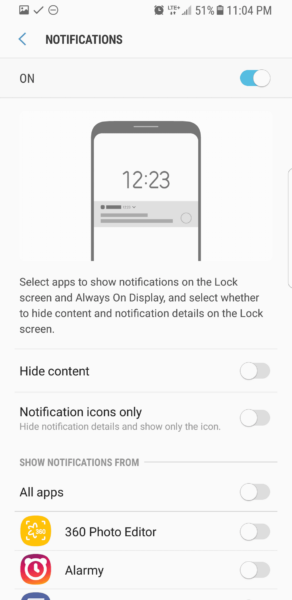
I recommend hiding notification content on the lock screen. You still get notifications, but the content is not shown while your device is locked. This way no one with physical access to your phone can see anything sensitive within a notification.
Under the Notifications settings.
- iOS: Turn off Show on Lock Screen
- Android: Turn on Hide content
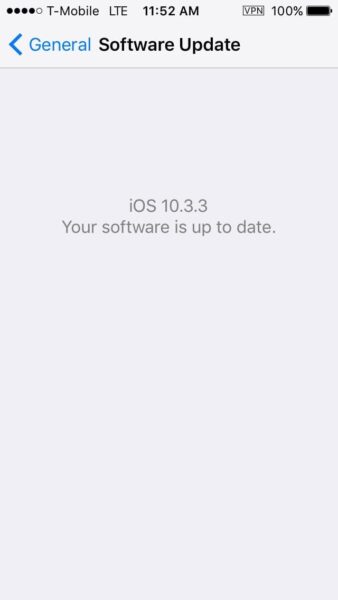
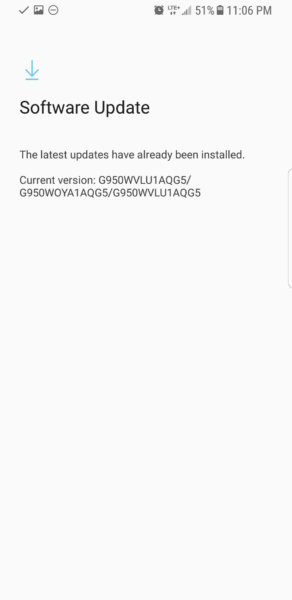
2. Updates
We preach (for good reason) that when it comes to your website, software updates often include security patches. The same is true for all of your devices.
i. Operating System Updates
You should configure automatic updates, but you can also check manually when setting up your device.
- iOS: Settings > General > Software Update
- Android: Settings > Software update
ii. App Updates
Apps are not updated along with the operating system. You should update all of your apps at least weekly. I also minimize the risk of compromise by keeping very few apps on my phone.
- iOS: App Store > Updates
- Android: Play Store > My apps & games
iii. Bloatware and Trusted Sources
Android devices typically come with more unnecessary apps than iOS, but either way, make sure to remove what you will not use. It can always be added back later. If I don’t have an immediate use for it, it’s deleted.
On Android, make sure to keep Unknown Sources turned off, which would allow installation of apps that are not approved on the Play Store.
3. Permissions
Most apps require specific permissions. You can adjust these under your App settings to keep your device more secure. I recommend taking a look at each section and if an app you use shouldn’t require access, turn it off.
i. Location Tracking
Personally, I have Location services turned off and only enable it when I’m using Google Maps, Lyft, or Uber. I only install Lfyt and Uber when I need them, and remove them after I’m done using them.
With Location services off, you won’t be able to use Find My iPhone, but you can always disable the location for all other apps if you want to still use it.
ii. Microphone Access
I don’t allow anything to have access to the Microphone. If an app requires access, I will enable it while I’m using the feature that requires microphone access, then disable it afterward.
iii. Camera
The same goes for Camera. For people who use their camera often, you may want to upload images from the default camera and remove access for all other apps.
4. Connections
Most devices have various ways of connecting to other devices, and these can be tailored to suit your needs.
i. Internet Access
Generally, I’m only using either Wi-Fi or Cellular data, not both. So I disable the one not in use.
I also always use a VPN for internet access. If you want to use an app, you might consider ProtonVPN. It has a lot of different locations, is reliable, pretty secure, can be used on multiple devices, and they offer a free version,
ii. Bluetooth and Hotspot
For Bluetooth, I always keep it off, and with Personal Hotspot, I always keep it off until I am ready to use it, and use the USB option only. That way I feel it is a bit more secure than if Hotspot came through Bluetooth or over Wi-Fi.
iii. Known Networks
If you have had your phone for a while, you probably have it connected to a lot of different networks that you won’t connect to again and don’t tend to keep.
- iOS: General > Reset > Reset Network Settings (will require you to re-enter your WiFi password).
- Android: Connections > Wi-Fi > Advanced > Manage networks (disable individual connections)
Recommended Apps:
There are a lot of apps that can help keep your device more secure. Here is a list of a few to consider:
- Signal – Encrypted messaging app
- ProtonVPN – For private browsing
- Mozilla Firefox Focus – Web browser
- SnowHaze – a more secure/private browser for iOS
Conclusion
As a final note, I would recommend getting a privacy screen and phone case to cover the back and front cameras on your phone. I use the EyePatch Case which has a sliding plastic piece to cover both cameras. It functions similar to a webcam cover for your computer and you can just slide it over when you are using the camera.
What do you do to protect your phone? Leave a comment, tweet us @SucuriSecurity, or email us at info@sucuri.net.
Appendix: Dealing With Android Privacy Issues
If you have been following this series, you know that I take privacy seriously. For this article, I had to use an Android phone, which requires the use of a Google account. For those curious about how I kept my identity secure during the process, I’ve included a summary of some actions I took. This might be helpful if you are looking for ways to greatly enhance your privacy.
To set the phone up to start, I connected the device to a local public WiFi network at a coffee shop about thirty minutes from my physical residence. Yes, publicly-accessible WiFi is not secure, I’m aware of that. I did this so that the device would be harder to associate with me than if I had connected it to my local network or a network I frequently use. Google tracks and logs pretty much everything, including location and WiFi access points.
I was forced to set up a Google account, as there was no way to skip that option on the set up with this phone. To do this anonymously, I created a random Gmail address, secure password, and then it required a phone number to text me a verification code. I always have a collection of dumb phones for purposes such as this. I used one of my $10 Tracfones with $20 worth of credit that was purchased anonymously, which allowed me to receive the text. I then had a fairly anonymous Google account that would be hard to associate with me.
I purchased both phones over 60 days ago and paid cash for them. I waited to use them because security cameras typically store footage for 30-60 days.
I created a virtual machine on my computer so that I could sign into my new Google account and configure the privacy settings as strictly as possible. After that was done, the VM was deleted.
I also added two-factor authentication to the Gmail account and used the same dumb phone as before. I then removed the option to receive authentication codes via text message and configured Google Authenticator in its place. From there, I added the ten backup codes to KeePass in case I ever lost access to the phone.
If there is interest in a future series that explores privacy more in-depth, let us know in the comments or by emailing info@sucuri.net.








![Massive ois[.]is Black Hat Redirect Malware Campaign Targets WordPress Sites](https://blog.sucuri.net/wp-content/uploads/2022/11/BlogPost_Feature-Image_1490x700_PHP-Login-Stealer-390x183.png)

