We recently noticed an interesting example of network infrastructure resources being used over a period of time by more than one large scale malware campaign (e.g redirected traffic, cryptomining). This was discovered when reviewing sources of the various malicious domains used in a recent WordPress plugin exploit wave.
Mass Infection of WordPress Websites
The latest Easy SMTP plugin vulnerability has resulted in many infected WordPress websites. The first wave of exploits seemed to follow a similar methodology as the first wave of GDPR plugin exploits in late 2018:
- The malicious user exploits the vulnerability and enables new user registration with the default user level set to administrator, then creates a new admin user.
- The new user with admin privileges is used to upload PHP backdoors to the website files and update the site_url to a domain controlled by a malicious user.
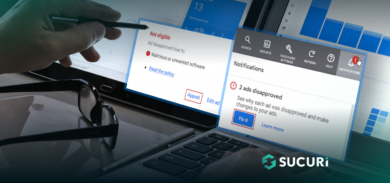
- The new site_url redirects the infected website’s visitors to the domain controlled by the malicious user, which loads JavaScript to track the visitor via cookies. Then it redirects to a new malicious URL.
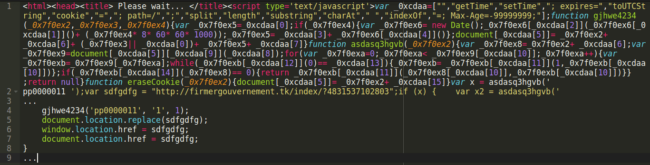
MalwareBytes recently analyzed the various methods used by hackers to monetize these large-scale attacks against plugin vulnerabilities through their network of malicious redirections using .tk domains (as shown in the above sample image). You can view their article here.
Some of the domains we have seen being used in the site_url value for WordPress databases:
somelandingpage.com getmyconfigplease.com getmyfreetraffic.com setforconfigplease.com strangefullthiggngs.com (new) redrentalservice.com (new)
While this general methodology (i.e exploit -> create admin user -> upload malware) isn’t new, it is an observable pattern. This could be used to gather additional information to see if there were any actual relationships between the domains that we kept noticing being used when changing the site_url value in the wp_options table.
Similarities to Cryptojacking Campaigns
After additional research, we identified that this campaign shares infrastructure used by another malware campaign known as the “game console cryptojacking” attack:
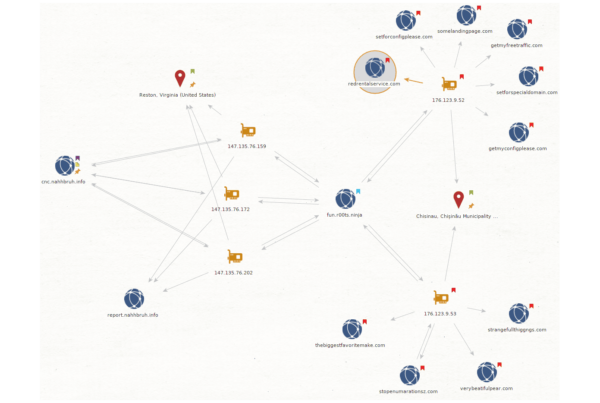
The malicious subdomain fun.r00ts.ninja resolved to two web servers located in Chisinau, Moldova:
176.123.9.52 176.123.9.53
These are the same two IP addresses that host the domains used to replace the site_url value on infected WordPress websites. The initial GDPR plugin exploit wave showed signs of this. And then again with the initial wave of Easy SMTP exploits.
fun.r00ts.ninja had also resolved to the following intermediary servers located in Virginia, USA:
147.135.76.202 147.135.76.172 147.135.76.159
Other domains that had resolved to the same IP address infrastructure include cnc.nahhbruh.info and report.nahhbruh.info.
Shockingly it looks like r00ts.ninja has been operating for at least one year and is apparently involved with large scale operations like recent cryptojacking through gaming consoles network resources (PS4 and Xbox):
Conclusion
It may just be coincidence, but it looks like this r00ts.ninja group began their cryptomining malware campaign around the same time that news about Coinhive shutting down was made public. This incident serves as an example of how malware can be loaded onto your device when playing an online video game.
Unfortunately, sometimes the same network infrastructure resources will be used repeatedly for malicious purposes until eventually the host or owner of the abused network infrastructure shuts its down. In other cases, legitimate web hosts are just having their network resources abused while failing to secure it. There are also other cases where the web host doesn’t enforce many rules or respond to security/abuse complaints.
If you believe that your website has been compromised and you need help identifying the issue or cleaning up the infection, we can help.