Exploitation Level: Medium / Remote
DREAD Score: 6
Vulnerability: CSRF to Persistent XSS
Patched Version: 1.7.6
During regular research audits for our Sucuri Firewall (WAF), we discovered a Cross Site Request Forgery (CSRF) leading to a persistent Cross Site Scripting vulnerability affecting 70,000+ users of the WP Meta and Date Remover plugin for WordPress.
Disclosure / Response Timeline:
- April 30 – Initial contact attempt
- May 07 – Patch is live
Are You at Risk?
This vulnerability requires some level of social engineering to be exploited. An attacker will have to post a comment with a malicious link and the exploitation will succeed if the admin user clicks on that link when approving the comment.
We wrote in the past about different techniques attackers use to trick users and how they often have a high rate of success. You should update to the latest version as soon as possible, and remind all users to avoid clicking suspicious links.
Technical Details
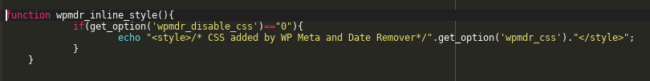
With the CSRF vector, an attacker stores malicious code that can call an external script acting on the behalf of an administrator. A bad actor could use this vulnerability to store SEO spam in your site or (under certain circumstances) send authenticated requests to edit the code of other plugins.
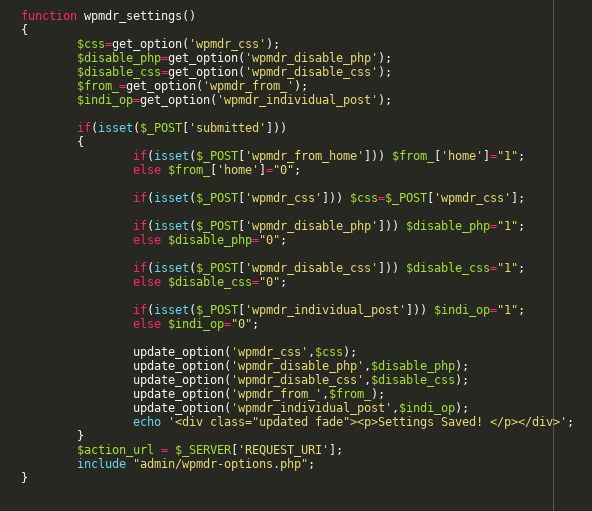
The vulnerability occurs in the method wpmdr_settings from the file wp-meta-and-date-remover.php:
This function is not checking if the POST data is originated from a legitimate form which could’ve been accomplished with WordPress functions like wp_verify_nonce().
If the attack is successfully executed, a malicious JavaScript payload will execute behind the scenes, and use the administrator’s browser session to store malicious code in the site.
Update as Soon as Possible
If you’re using a vulnerable version of this plugin, update as soon as possible. In the event where you cannot do this, we strongly recommend leveraging the Sucuri Firewall or equivalent technology to have the vulnerability patched virtually.