There has been a noted increase in the number of sextortion scams during 2019. These scam campaigns are commonly distributed through email, but any method of digital communication can be used to deliver the blackmail threat to the victim.
Blackmail Attempts for Bitcoin Payments
The majority of these sextortion scam emails follow a similar template, disclosed earlier this year in a post by MalwareBytes. This email template has been translated into various languages, however some of the templates use different methods to lure victims into believing the scammer.
These emails usually involve the scammer claiming to have recorded the victim through a webcam over a certain period of months. Claims may also include having viewed browser history with adult content.
While it is indeed possible for someone to be involved in this level of intrusive spying, these email campaigns are merely a bluff sent out by the millions. If even a small fraction of victims respond and submit the extortion Bitcoin payment to scammers, the campaign would prove to be lucrative.
Scam Variants Blocked by Spam Filters
September 2019 saw reports in Ireland of another variant of this email template, which included an accusation that victims had viewed illegal, underage content.
While the scam email threatened to release nonexistent evidence to law enforcement, it lacked authenticity. Fortunately, spam filters are doing a good job at blocking these scam emails from ever arriving to the victim’s inbox.
Disabled Browser Functions & Other Website Features
A new sextortion scam was recently reported to us which takes an entirely different approach to the trends that we’ve seen in the past year.
First, it is not solely reliant on emails. The scam campaign leverages websites to include features like fake purchase payment phishing forms and browser interactivity to add the illusion of authenticity.
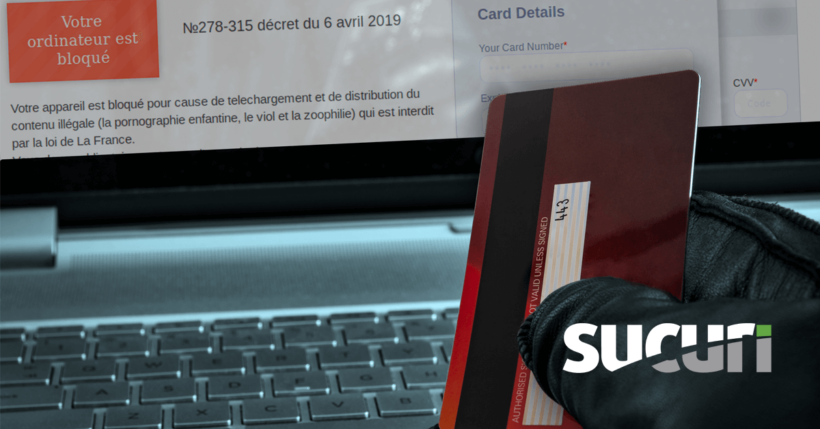
In fact, this scam tries to trick victims into believing it is the website for the French national police.
JavaScript Details
When a victim loads the scam website, the browser’s full screen mode is triggered on two different conditions: if a click event is fired, or after a specified wait time is reached.
From the full screen mode, it then disables various browser function hotkeys with the aid of Javascript functions.
You may have encountered websites that disable functions like right clicking on a website—usually in an attempt to prevent site visitors from saving images or other content. Similar functions can also be used to prevent visitors from performing specific browser tasks like using the Ctrl + U hotkey for viewing the page’s source, however it’s just a deterrence as you can just obtain the source using a variety of other methods.
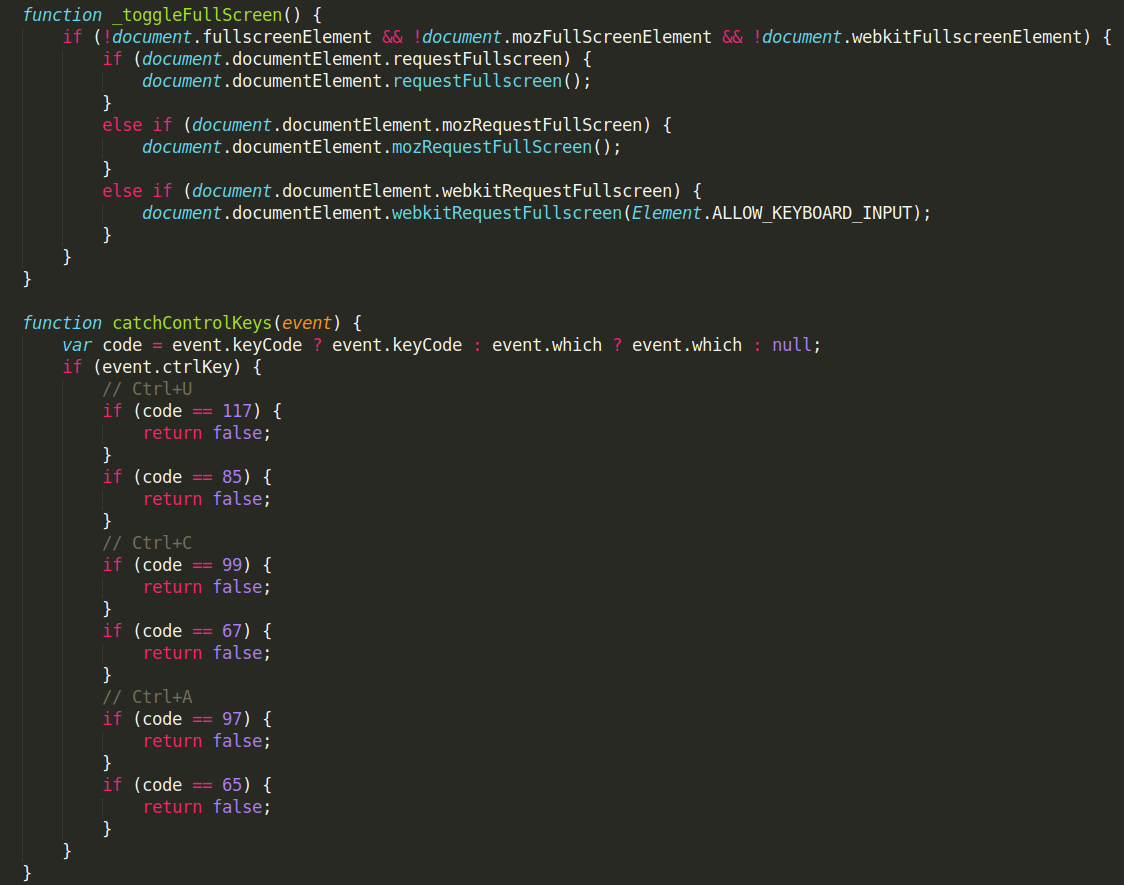
Credit Card Stealer
The credit card payment form used in this scam campaign doesn’t actually charge victims’ cards for the requested extortion fee. Instead, it steals credit card information by using a mail.php file for exfiltrating the stolen information to an email address controlled by the scammer.
Deceptive Design Elements
Analyzing the HTML and CSS from this campaign revealed why the scammers tried so hard to keep the browser in full screen mode.
When the browser enters full screen mode, it causes the browser to maximize the current open tab and so a victim can’t see their Windows taskbar or the “X” button to close the browser window.
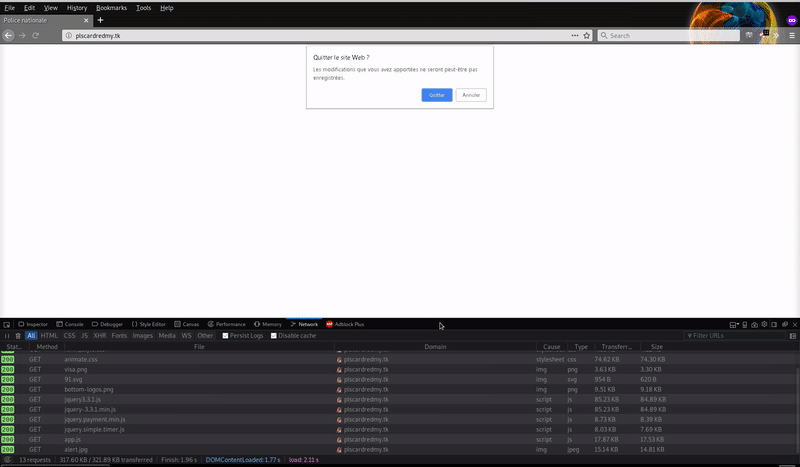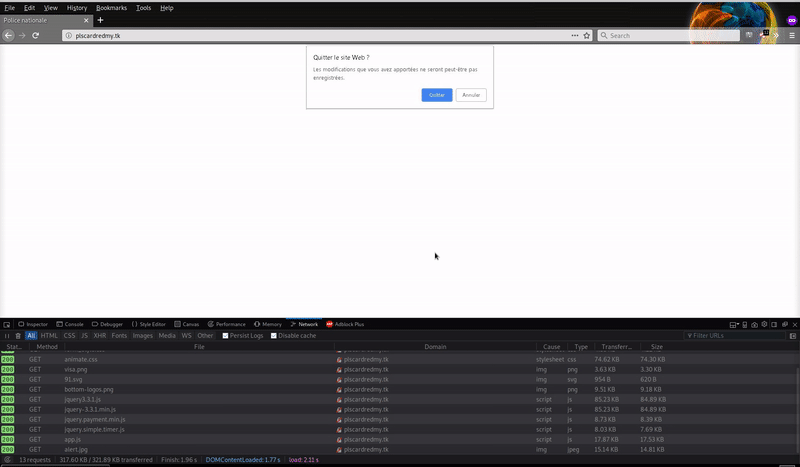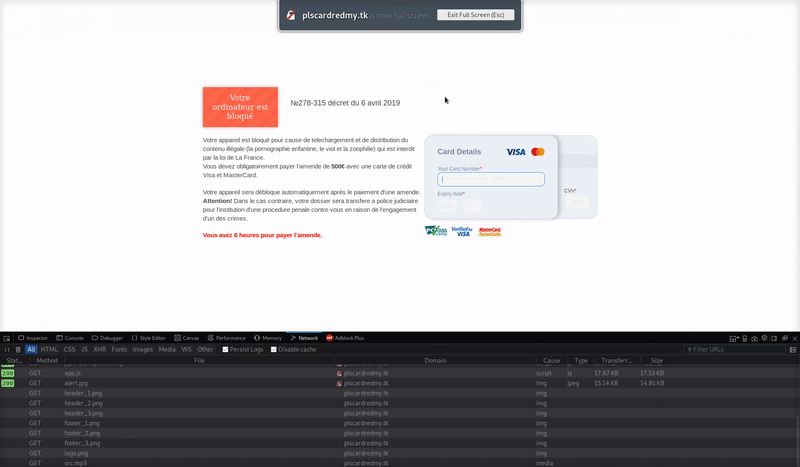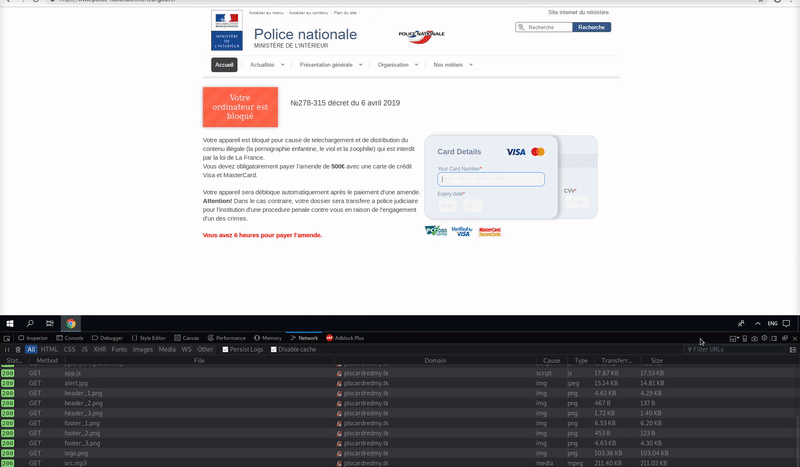
This phishing page’s design does a pretty good job of replicating a Windows 10 user’s desktop, complete with an open Google Chrome window.
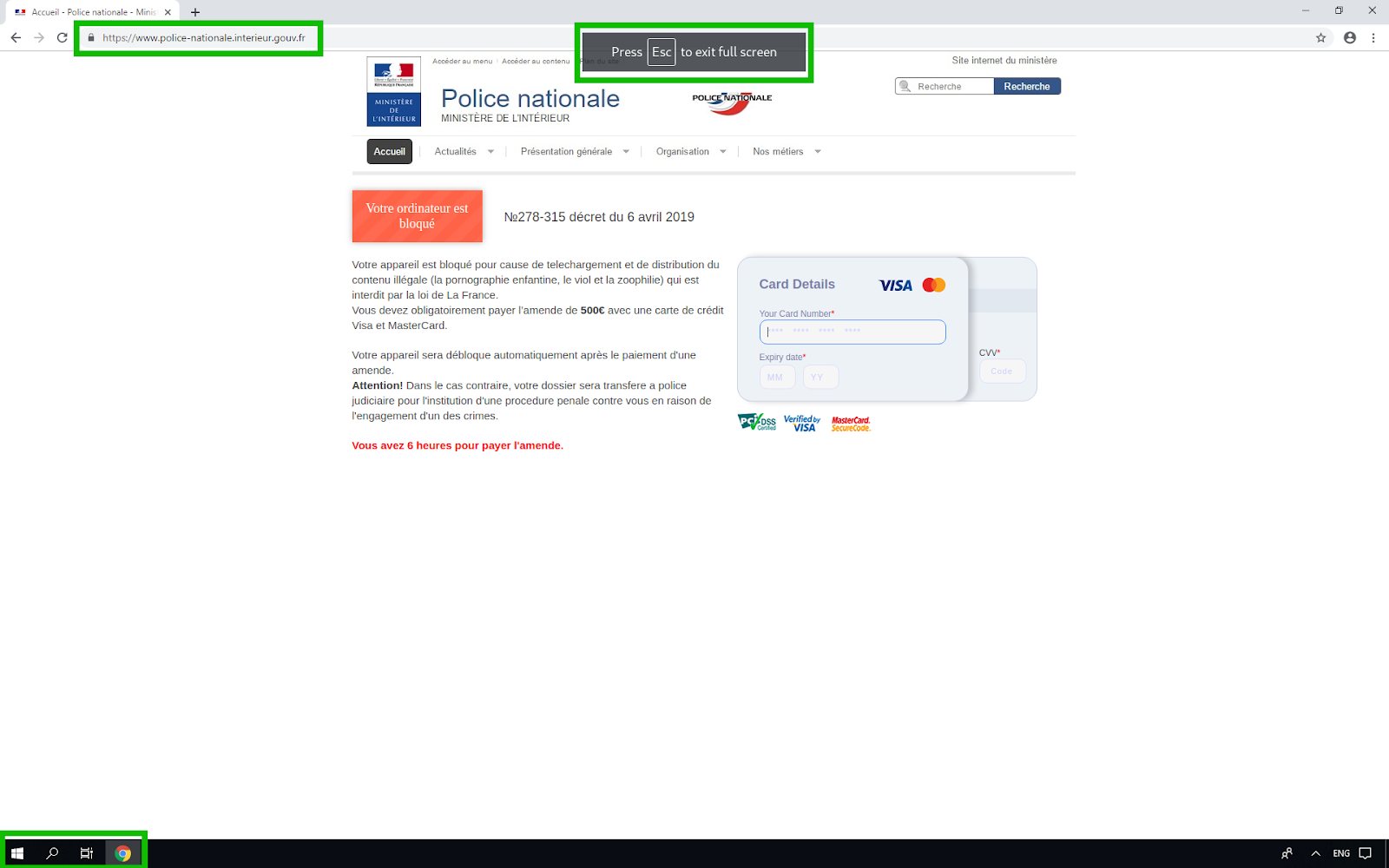
It may not be perfect, but this is a pretty good way to trick someone into thinking they are being blocked from the Internet—when in reality, they are just loading a cleverly crafted scam website.
The actual extortion threat text found on the website is where this scheme takes a disturbing turn. Here is the content translated from the original French messaging found on the scam page:
| Your computer is blocked. Your device is blocked due to downloading and distributing illegal content (child pornography, rape and zoophilia) which is forbidden by the law of France. You must pay a fine of 500€ with a Visa and Mastercard credit card. Your device will unlock automatically after payment of a fine. Warning! If not, your file will be transferred to the judicial police for the institution of criminal proceedings against you because of the commission of one of the crimes. You have 6 hours to pay the fine. |
Conclusion
Websites that replicate both the victim’s desktop environment and the French National Police definitely add to the suspicion that someone is monitoring you or is able to access your computer.
The part that puzzles me is, why would scammers go overboard and accuse the person of something so horrific as underage content? I hope that it’s because they believe that a certain number of victims will just pay the money to avoid accusations or any official court summons. This seems unlikely since at some level paying the fee would be viewed by many as a sign of guilt.
A worse (and more sickening) possibility is that these scammers honestly believe there are enough people out there viewing this illegal content that would make great potential blackmail victims.
Unfortunately, recent law enforcement actions have shown that people from all over the world are still regularly paying to view this type of illegal content, as evidenced in a recent dark net bust resulting in 337 arrests.
Overall, these extortion scams seem overly aggressive. Scammers would probably cast a wider net by accusing victims of more common criminal offenses, like downloading copyrighted/DMCA content.