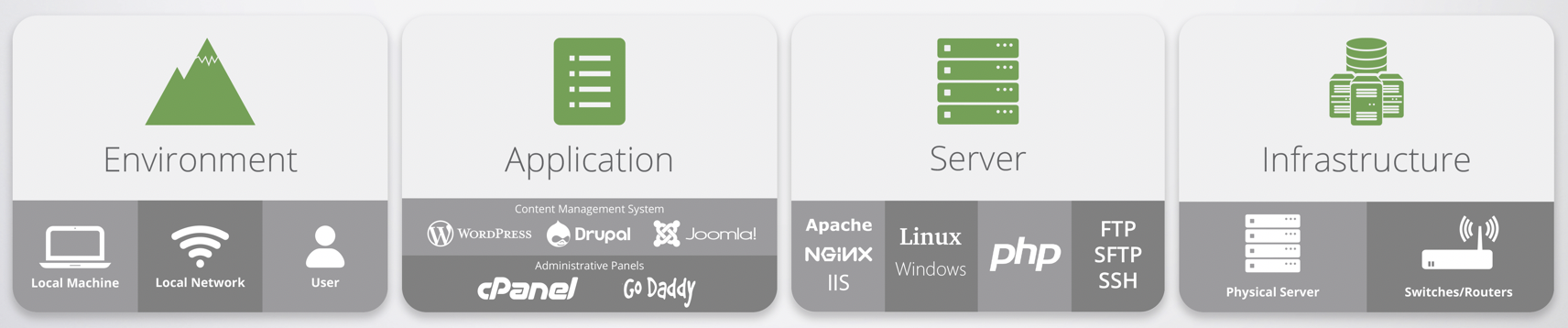
When we started Sucuri we set out to make enterprise security accessible, affordable, and effective for every day webmasters.
It was at a time when open-source platforms like WordPress, Joomla!, Drupal, and others were changing the web landscape. With them came an entirely new generation of administrators who had no idea that they were now webmasters — but they shared the same responsibilities that large enterprises had around ensuring the Confidentiality, Integrity and Availability (CIA) of their web applications.
Sucuri was built to empower the webmaster and protect its users. But what about the webmaster’s safety? What about threats from websites you do not own? Who protects the webmaster when they are the online user, and not the website owner? That’s where network security comes into play, and why we have built CleanBrowsing.
Expanding Application Security with Network Security
For years, I have spoken about the threat landscape and how exhaustive it is. We have invested energy in building resources to help you adequately prepare for everything that exists within the world of your application, but that is only one of a series of domains that contribute to your overarching security posture.
In a post-COVID world that sees us working from home, going to school from home, and otherwise being removed from the protections that enterprise networks afford us, we figured we would take some time to focus on our environments. More specifically, placing emphasis on networks and how you can leverage technologies like DNS to help protect your server and its applications — but also yourself from external factors outside of your control.
Enhancing our Environment with Network Security
One of the amazing things about COVID has been this untethering of the traditional views around co-located work. For many in the startup world the idea of remote work is not new, but for many accustomed to working in physical offices it is. And similar to the explosion of webmasters in 2010, we are seeing an exponential increase in the number of system administrators as more people go home and find themselves responsible for their own environments and networks.
The good news is that focusing on your local environment not only keeps you safe, but also helps reduce the risk you introduce to your web application.
Network Security & Domain Name System (DNS)
The principles of network security are very similar to application security, and there are tools available designed to help you combat threats. Unlike what we do here at Sucuri, network security tools help keep you protected from those things you can’t control.
One of the more effective ways to accomplish this is to leverage the Domain Name System (DNS). DNS is the lookup table of the web. It helps us convert something as simple as sucuri.net to its corresponding IP address, telling the web exactly where the content resides. Its power doesn’t stop there, either. DNS can also be used to keep bad things away.
Sucuri empowers you, the website owner, to a) know if something is wrong, and b) help you solve it. What do you do to ensure that sites you’re visiting, and don’t control, are not infected or being used to steal information from you?
The benefits of DNS are not just limited to what sites you visit, but can also be leveraged to limit what resources your web server can access.
Introduction to a DNS Firewall
The Sucuri firewall was built to keep bad actors off your site. It protects your website from people that might want to exploit weaknesses (i.e., vulnerabilities) and do malicious things with your site (e.g., distribute malware).
Similar to traditional firewalls, a DNS firewall detects malicious traffic, shielding you from attacks and protecting your network. While it doesn’t stop exploitation of vulnerabilities in your environment, it does help you from being susceptible to malicious scams.
A DNS firewall is built on top of the Domain Name System (DNS) construct. It integrates with the lookup table of the web, functioning as a first line of defense against outside of threats. As malicious domains are identified, the DNS firewall acts on your behalf and proactively mitigates the risk by blocking direct access.
Let’s look at how it relates to website owners.
How DNS Firewalls Help Website Owners
A DNS firewall can be married with your overall security posture and can be leveraged in a number of different ways. Here, we’ll focus on two that are most practical for website owners:
- Enhance Server Security
- Enhance Local Security
1. Enhance Server Security
One great example of the power of DNS can be highlighted from December 2019’s Legion Loader campaign. The basic tenant of the campaign was the use of a Command & Control (C&C) construct, which required the campaign to “phone home” for instructions.
In this example, the C&C is rotated between these domains:
ntupdate4[.]top
ntupdate3[.]top
iplogger[.]org
stationstall2[.]info
egreetcards942[.]servehttp[.]com
legion1488[.]info
Leveraging a DNS firewall would mitigate the potential impact by disabling the payloads ability to communicate to it’s C&C — essentially filtering any malicious requests as they are detected.
This scenario assumes communication is happening on the server. So, what about your local environment?
2. Enhance Local Security
We don’t have to look too far for an example that applies to your local environment.
We often talk about what happens if your website is hacked and the effects it can have on your readers and customers. But have you ever stopped to think about the impact you may experience as a website visitor when you visit a compromised website?
Let’s look at the recent Magento exploit dubbed CardBleed.
This campaign saw thousands of Magento sites compromised. Bad actors were able to steal payment information from unsuspecting users by injecting malicious code into the site’s JavaScript. Whenever the site was visited by a user, the malicious JavaScript would execute via the local browser. Sensitive credit card and personal information was stolen and sent to the C&C where the information was harvested.
To accomplish this, attackers were loading and embedding their malicious payload into the website’s JavaScript via the mcdnn[.]net domain. They were then siphoning any harvested information to the imags[.]pw domain for future use.
Similar to the Legion Loader campaign, a DNS Firewall would have prevented the website from a) loading the malicious content and b) pushing stolen data to the C&C.
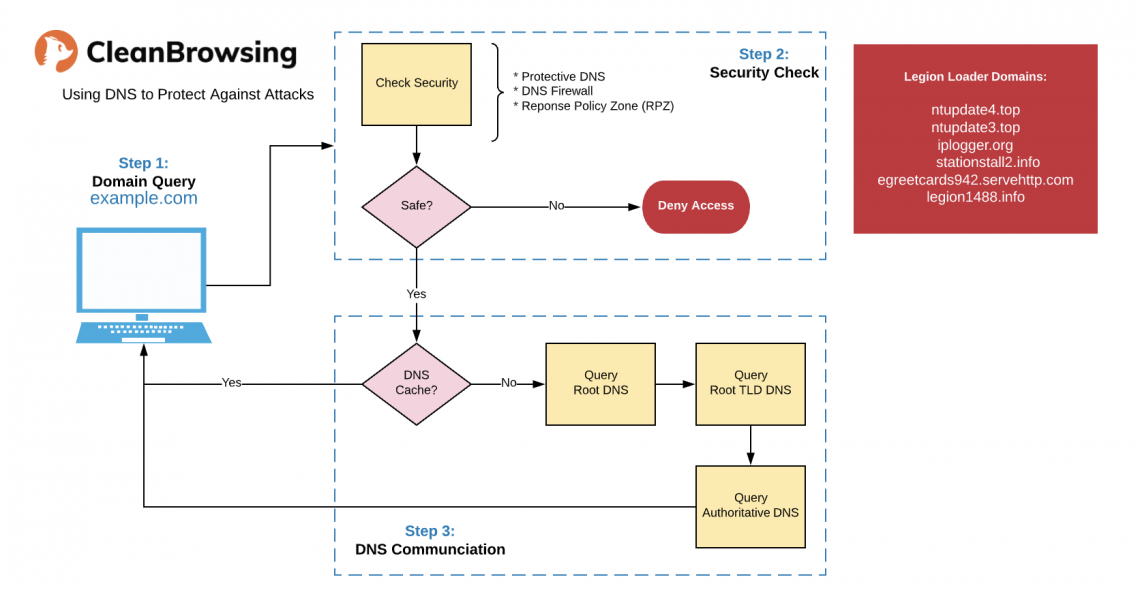
How DNS Firewalls Work
Leveraging a DNS Firewall can be a highly effective security control. This is why we built CleanBrowsing and we offer a free security filter that anyone can use.
The following illustration highlights how a DNS filter like CleanBrowsing can be employed on both your servers and local environments to help enhance your security and reduce your risk exposure.
CleanBrowsing focuses on enhancing your security against external factors outside of your control — such as websites you don’t own. It also introduces a number of useful capabilities like content filtering, which allows you to block access to dangerous or inappropriate web content and create the type of environment you want in your home.
This technology can be deployed on the networks of homes and businesses alike and is proven to be highly effective at improving your overall security posture.