In the spirit of National Cyber Security Awareness Month (NCSAM), let’s talk about a security basic that many people overlook: passwords. These are one of the most fundamental aspects of website security, yet we too often see webmasters taking a lax approach to their credentials.
Weak passwords make it easier for bad actors to perform brute force attacks against your sensitive admin, email, and server credentials. In fact, insecure usernames and passwords are among some of the leading reasons for website or server compromise.
The password manager provider NordPass found that last year the most commonly used password was “password”. That edges out some real gems including “guest”, “qwerty” and the always-popular “12345”.
Thing is, everyone has their own password policy. It’s very personal and usually based on a set of assumptions about online security. Many users choose “efficient” policies over secure ones.
Like any defensive measure, best practices in password management can help to minimize the level of risk — however, no single measure provides a 100% guarantee.
Password management is a choice — and a habit. By taking a deeper look, users can make informed decisions and put better passwords into practice.
What makes a good password?
There are a key set of guidelines and standards for securing your digital identity. Let’s review a few of the core considerations to making a strong password.
Length
The longer your password, the stronger it will be. Length directly influences how difficult a password is to guess or crack.
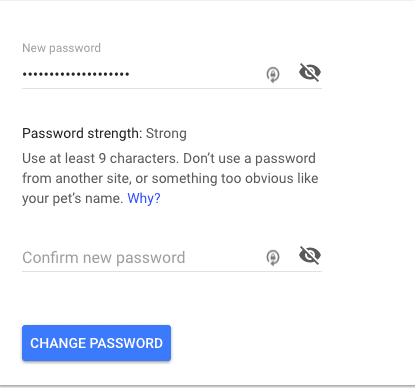
The more characters you use, the more computational power, time, and attempts will be required to crack it — and the higher mathematically probability it has of not being guessed. More characters equals a better, more secure password!
Uniqueness
You might have been told this before, but Password123! or 123456 (or any obvious combination of sequential numbers and letters) will be guessed very easily.
It’s also not wise to use known personal details like your birthday or pet’s name, as these pieces of information can be found without much effort by anyone on the web. This is because hackers often use “dictionary attacks,” where they systematically enter every word in the dictionary to try and guess a password.
Complexity
Adding numbers and unique characters to your website passwords will further increase security.
For example, anyone can use their dog’s name Harry as a password would be incredibly insecure. But by adding numbers, characters, and a mixture of lower and upper case letters, the original Harry” becomes obscured as &H4RrY:)*7?! — and therefore harder for an attacker to guess.
Diversification
To effectively protect your accounts you should avoid reusing passwords. That includes any database, admin, or FTP credentials that you use for your website. Reusing passwords makes accounts vulnerable to credential stuffing attacks.
If one of your accounts gets compromised, a unique password will help isolate the incident. If you have multiple accounts with the same password, they may be at a higher risk of also being compromised — resulting in unpleasant consequences for your website.
Let’s talk some more about password entropy
Entropy is the word used to describe how random a password is. The more entropy your password has, the stronger and less predictable it is. Using longer passwords increases entropy exponentially. Adding character sets (numbers, symbols, unicode) increases the permutations available for any length of password. If your password, or part of your password exists in a word list, it isn’t random.
If your password is based on a pattern or common base, it isn’t random. When password entropy is low, the password is easier to predict.
It doesn’t help that password strength meters can differ greatly from one to the next. It can be frustrating trying to figure out exactly what makes a password “strong” or theoretically unpredictable. All the while, there is talk of quantum computers that aim to be so fast, they could break any encryption with ease.
How to remember passwords
If the thought of trying to remember every unique password for all of your accounts makes you woozy, then I have the solution for you! The easiest way to keep you on track is by using password managers such as KeePass, LastPass, 1Password, or Dashlane.
They will keep all of your passwords in one “vault” and even auto-fill passwords if you take advantage of a browser extension. They can also help generate passwords with higher levels of entropy for you.
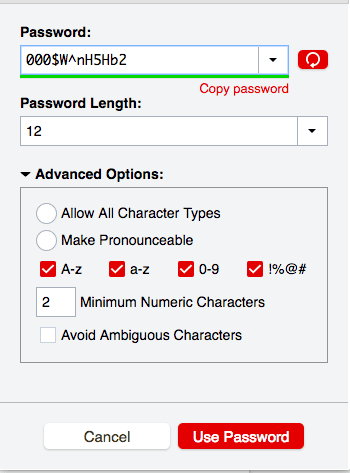
Understanding password manager security
It’s worth mentioning that each password manager will have its own unique set of benefits and drawbacks, so you’ll want to do a bit of research to figure out which one meets your needs the best. While quite convenient to use, popular cloud-based password managers like LastPass have suffered data breaches in the past.
Furthermore, the security of your computer is also a critical component: no password manager will be able to effectively protect your data in an insecure, spyware infected environment.
How does a password get hacked?
Computers work incredibly fast, and hackers have access to huge amounts of data to help the computer guess more efficiently. On a typical US keyboard there are 94 possible characters. A brute force attack, in its basic form, attempts to guess every possible combination of these characters until the hacker gets into the account.
You can take a look at this video to see how attackers use automated tools to launch a brute force attack against a website.
This method works quickly if the password is fairly short, but can be exhausting with longer passwords. A dictionary attack is a more efficient way to guess long passwords.
A dictionary attack uses the same technique as a brute force attack, but instead of guessing all the character combinations, it tries from a list of common passwords and words from dictionaries and literature. Even at almost fifty characters, including symbols, you can’t use the call of Cthulhu as your password. We’re at a point where even the use of common substitutions — such as L1K3 TH15 — are part of most common word lists.
The rise of password breaches
A strong password isn’t a 100% guarantee for security. The odds of a password getting leaked due to a data breach are on the rise. With the sheer number of password breaches that continue to occur, hundreds of millions of potentially active passwords are floating around in cyberspace.
Both bad guys and good guys look at password dumps to research the most common passwords and patterns. This data reveals many common tricks that people use to make passwords memorable and strong at the same time.
Clever methods of making your own passwords become transparent with enough data:
- Pattern-based passwords (qwerty678^&*)
- A capital at the beginning and a number and symbol at the end (Password1!)
- Common substitutions (P@ssw0rd)
- Words associated with the user or website (Username@2014)
Once discovered, someone can design a program to exploit these methods via brute force attacks, and in turn, that program can expand the word lists that are used.
A variety of social tactics can also be used to reveal passwords. By spoofing an email address, attackers can lure users with phishing emails that seem legitimate. Similarly, malware on a computer may attempt to scare users into revealing information.
In targeted attacks, hackers will use any personally identifying information they can find (such as your birthday, or your dog’s name) to enhance their attack.
For website protection against these kinds of attacks we recommend implementing multi-factor authentication, limiting login attempts, and using a website firewall to protect sensitive admin pages and block bad bots. This can help prevent malicious users from breaking into your site.
Future-proofing your website passwords
It’s difficult to imagine a future-proof password. However, making passwords unique, complex, and longer is a start — and can be easily accomplished with a decent password manager. Perhaps we’ll see new authentication methods.
One thing is certain, as computers evolve in terms of processing speed and storage capacity, requirements on password entropy will need to evolve with it.
What we do know is that password breaches are gaining popularity, and the standard password is not going away. Like anything to do with security, you want to know the risks and put a policy in place that keeps you one step ahead of potential threats. When it comes to your website and visitors, protection against brute force and dictionary attacks is an important step to take.