McAfee SiteAdvisor is one of the top three blocklisting authorities currently issuing security warnings on websites. When a website is blocklisted, it loses 95% of its traffic, on average. Blocklisting can affect how visitors access your website and how it ranks in Search Engine Result Pages (SERPs). Websites that have been scanned and found to possess harmful behavior or content are flagged by a blocklist authority (like McAfee SiteAdvisor), which then removes the site from their index.
Contents
Your website has been officially blocklisted when the big red splash page is shown. This is designed to stop visitors from accessing it.
If you are seeing security warnings when trying to reach your website, follow this guide to fix these issues and request a review for blocklist removal.
Here is an example of a common malware warning that suggests your hacked website is serving malicious downloads (such as viruses, spyware, rootkits, and ransomware).
Note
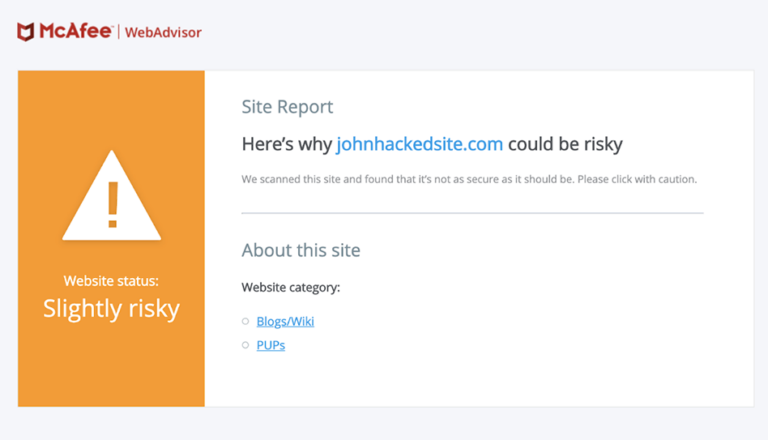
Here’s why johnhackedsite.com could be risky. We scanned this site and found that it’s not as secure as it should be. Please click with caution.
The very first step is to make sure your site is clean.
You can use our free tool, Sucuri SiteCheck, to scan your site and find malicious payloads, malware locations, security issues, and blocklist status with major authorities.
To scan your website for hacks and blocklist warnings using Sucuri SiteCheck:
If SiteCheck is able to find a payload, this can help narrow your search. The following section of this guide will help you manually review your site to look for suspicious elements. You can also use other tools such as UnmaskParasites.
Note
If you have multiple websites on the same server, we recommend scanning all of them. Cross-site contamination is one of the leading causes of reinfections. We encourage every website owner to isolate their hosting and web accounts.
To perform complete malware removal, you should be able to edit files on your server. If you are not comfortable with this, enlist professionals to clean your site.
File Replacement: For CMSs such as WordPress or Joomla, you can safely rebuild the site using new copies of your core files and extensions directly from the official repositories. Custom files can be replaced with a recent backup—as long as it’s not infected.
Malicious Domains and Payloads: If SiteCheck or the Diagnostic Page indicate any malicious domains or payloads, then you can start looking for those files on your server. The discovery date can also narrow your search down to files modified around that time frame.
To manually remove a malware infection from your website files:
Hackers change malicious sites fairly often to avoid detection. As a result, Google’s diagnostic page may mention malicious or intermediary domains that can no longer be found on your site since they have already been replaced with new domains.
If you can’t find the “bad” content, try searching the web for the domain names listed on the diagnostic page. Chances are, someone else has already figured out how those domain names are involved in website exploits.
Caution
Manually removing “malicious” code from your website files can be extremely hazardous. Never perform any actions without a backup. If you’re unsure, please seek assistance from a professional.
The Sucuri Firewall can help block attacks and virtually patch known vulnerabilities.
Caution
Do not overwrite your CMS configuration files. On WordPress, this includes wp-config.php file or wp-content. On Joomla, this includes the configuration.php file and customizations.
To remove a malware infection from your website database, use your database admin panel to connect to the database. In cPanel, most hosting companies offer PHPMyAdmin. You can also use tools like Search-Replace-DB or Adminer.
To manually remove a malware infection from your database tables:
You can also manually search for common malicious PHP functions, such as eval, base64_decode, gzinflate, preg_replace, str_replace, etc.
Caution
These functions are also used by plugins for legitimate reasons. Be sure to test changes or seek help, so you do not accidentally break your site.
Hackers always leave a way to reenter your site. More often than not, we find multiple backdoors, malicious admin users, and overlooked vulnerabilities.
User Accounts: Don’t overlook user accounts! Stolen passwords are a prime way hackers get back into your site.
To clean up your user accounts:
Hackers change malicious sites fairly often to avoid detection. As a result, Google’s diagnostic page may mention malicious or intermediary domains that can no longer be found on your site since they have already been replaced with new domains.
Caution
These functions can also be used legitimately by plugins, so be sure to test any changes because you could break your site by removing benign functions. The majority of malicious code we see uses some form of encoding to prevent detection. Aside from premium components that use encoding to protect their authentication mechanism, it’s very rare to see encoding in official CMS files.
Often backdoors are embedded in files similarly named to CMS core files but located in the wrong directory. Attackers can also inject backdoors into legitimate files.
Backdoors commonly include the following PHP functions:
It is critical that all backdoors are closed in order to successfully clean a website hack, otherwise your site will be reinfected quickly.
Secure Computing: It is possible for infections to jump from a computer to your website by using CMS and file transfer applications. All computers with access to your website should be secure.
Have all users scan their computers with an antivirus program.
Here are some antivirus programs we recommend:
Most browser blocklists use the Google blocklist API. For more information visit the Google help pages.
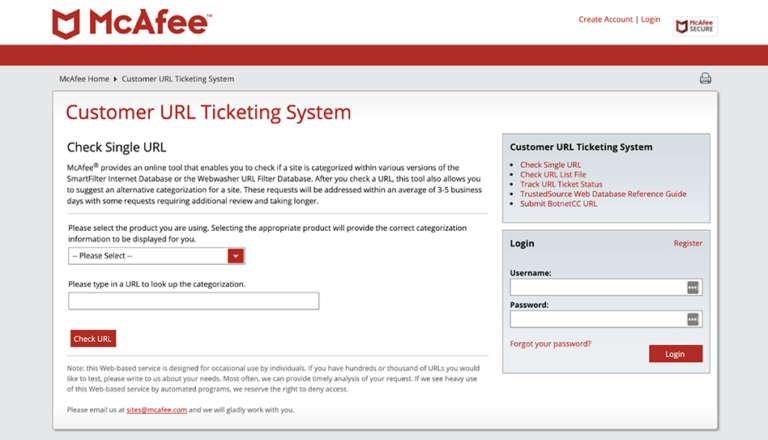
This is perhaps the most challenging part we found. Unlike Google and Bing or even Norton, there is no webmaster tools you can log into—at least none that we can find. However, here is the McAfee SiteAdvisor link you need to access.
To request a review of your site on McAfee to remove blocklist:
Like most blocklist authorities, it takes three to five business days on average for McAfee SiteAdvisor to remove a website from their blocklist. It can also take longer, depending on the complexity of the hack and length of the ticket queue.
You can track the status of the McAfee SiteAdvisor blocklist review by clicking on “Track URL Ticket Status”.
Remove Spam URLs from Google: If spam pages were removed from your site, they may have been indexed by Google already. The spam pages can create 404 (Not Found) errors when they are removed from your site. You can use the URL Removal Tool to notify Google that these spam pages should be removed from their index.
To remove spam URLs causing 404 errors:
Website Protection: You should also consider taking more steps to harden and protect your site. This includes applying updates, maintaining a good website backup strategy, managing user privileges, and implementing website security controls.
The number of vulnerabilities exploited by attackers grows every day. Trying to keep up is challenging for administrators. Website firewalls were invented to surround your website with a professional defense system.
Caution
This tool removes pages from Google search. This option helps after you have removed spam pages so that Google knows they are not actually part of your site.
If you’ve been blocklisted by McAfee SiteAdvisor you need to quickly get blocklist removal. Depending on your experience and budget, you could do it yourself using a guide like this one, or have a professional do it for you. Either way, it’s important to act as soon as possible. The longer your website is blocklisted, the more damage it can do to your ranking and reputation.
There is very little difference between the McAfee SiteAdvisor blocklist and Google blocklist. If I site gets listed on one, it is very likely it will quickly appear on the anther. The advantage of this for site owners is that the process for fixing blocklist warnings is generally similar between blocklist authorities.
Say on top emerging website security threats with our helpful guides, email, courses, and blog content.