What is XML-RPC? Security Risks, Best Practices, and How to Disable It
XML-RPC is a protocol that lets remote applications send commands to your site using XML and HTTP. In WordPress, it works through the xmlrpc.php file…
Vulnerability & Patch Roundup — February 2026
Vulnerability reports and responsible disclosures are essential for website security awareness and education. Automated attacks targeting known software vulnerabilities are one of the leading causes…
Understanding File and Folder Permissions for Better Website Security
Website security begins on the server, not with a plugin. Every page and configuration file is stored on disk, and the operating system controls who…
From Guessing to Phishing: The Dynamics of Password Security
Password security was once just a small hassle. Now, they’re the main defense for bank accounts, cloud tools, customer data, and businesses. Attackers use automation…
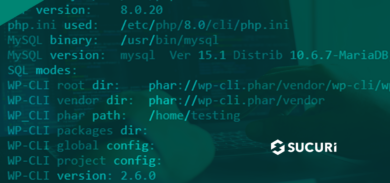
WP-CLI: How to Install WordPress via SSH
Sure, there are tons of one-click installers floating around for WordPress. But they’re not always the most secure option — and can still be tedious…
Beyond Login Screens: Why Access Control Matters
As breach costs go up and attackers focus on common web features like dashboards, admin panels, customer portals, and APIs, weak access control quickly leads…
Creating a Strong Password in 7 Easy Steps
Have you ever set up a new server, database, or admin account but once it came time to create a password, you struggled to come…
Vulnerability & Patch Roundup — January 2026
Vulnerability reports and responsible disclosures are essential for website security awareness and education. Automated attacks targeting known software vulnerabilities are one of the leading causes…
Shadow Directories: A Unique Method to Hijack WordPress Permalinks
Last month, while working on a WordPress cleanup case, a customer reached out with a strange complaint: their website looked completely normal to them and…
Securing Your Computer: A Primer for Windows and Mac Users
In this post we’ll be focusing on a part of your digital life that quietly influences everything else: the computer you use to log into…
What is Website Monitoring?
You rarely hear about a website when everything is working. There’s no applause when pages load fast, forms go through, or checkout works smoothly. But…