Website security can be a complex (or even confusing) topic in an ever-evolving landscape. This guide is meant to provide a clear framework for website owners seeking to mitigate risk and apply security principles to their web properties.
Before we get started, it’s important to keep in mind that security is never a set-it-and-forge-it solution. Instead, we encourage you to think of it as a continuous process that requires constant assessment to reduce the overall risk.
By applying a systematic approach to website security, we can think of it as an onion, with many layers of defense all coming together to form one piece. We need to view website security holistically and approach it with a defense in depth strategy.
Content
Website security refers to the measures taken to secure a website from cyberattacks. That may include protecting a website from hackers, malware, scams or phishing, and errors. In this sense, website security is an ongoing process and an essential part of managing a website. Maintaining a secure website is critical to protecting your website visitors and users from attacks, data theft, and bad actors.
Website security can be challenging, especially when dealing with a large network of sites. Having a secure website is as vital to someone’s online presence as having a website host. If a website is hacked and blocklisted, for example, it can lose up to 98% of its traffic. Not having a secure website can be as bad as not having a website at all or even worse. For example, client data breach can result in lawsuits, heavy fines, and ruined reputation.
A defense in depth strategy for website security looks at the depth of the defense and at the breadth of the attack surface to analyze the tools used across the stack. This approach provides a more accurate picture of today’s website security threat landscape.
We can’t forget about the statistics, which make website security a compelling topic for any online business—regardless of their size.
After analyzing over 1,000 survey responses from web professionals, we uncovered some insights about the security landscape:
There are over 1.94 billion websites online in 2019. This provides an extensive playground for bad actors.
There is often a misconception about why websites get hacked. Owners and administrators often believe they won’t get hacked because their sites are smaller, and therefore make less attractive targets. Hackers may choose bigger sites if they want to steal information or sabotage. For their other goals (which are more common), any small site is valuable enough.
Note:
The instructions will vary depending on your server software and system. Some systems do not support Certbot, but you can find a list of other reputable clients that should work with your server environment.
It has become easier for the average site owner to get online quickly with the use of an open source content management system (CMS) such as WordPress, Magento, Joomla or Drupal.
While these platforms often provide frequent security updates, the use of third party extensible components – such as plugins or themes – lead to vulnerabilities that attacks of opportunity can easily exploit.
We have developed detailed website security guides for each popular CMS to help website owners protect their environments and mitigate threats.
A benchmark in information security is the CIA triad – Confidentiality, Integrity and Availability. This model is used to develop policies for securing organizations.
Confidentiality refers to access control of information to ensure that those who should not have access are kept out. This can be done with passwords, usernames, and other access control components.
Integrity ensures that the information end-users receive is accurate and unaltered by anyone other than the site owner. This is often done with encryption, such as Secure Socket Layer (SSL) certificates which ensure that data in transit is encrypted.
Availability rounds out the triad and ensures information can be accessed when needed. The most common threat to website availability is a Distributed Denial of Service attack or DDoS attack.
Now that we have some background on automated and targeted attacks, we can dive into some of the most common website security threats.
Let’s take a look at the most common website security vulnerabilities and threats facing modern websites today.
SQL injection attacks are done by injecting malicious code in a vulnerable SQL query. They rely on an attacker adding a specially crafted request within the message sent by the website to the database.
A successful attack will alter the database query in such a way that it will return the information desired by the attacker, instead of the information the website expected. SQL injections can even modify or add malicious information to the database.
Cross-site scripting attacks consist of injecting malicious client-side scripts into a website and using the website as a propagation method.
The danger behind XSS is that it allows an attacker to inject content into a website and modify how it is displayed, forcing a victim’s browser to execute the code provided by the attacker when loading the page. If a logged in site administrator loads the code, the script will be executed with their level of privilege, which could potentially lead to site takeover.
Gaining access to a website’s admin area, control panel or even to the SFTP server is one of the most common vectors used to compromise websites. The process is very simple; the attackers basically program a script to try multiple combinations of usernames and passwords until it finds one that works.
Once access is granted, attackers can launch a variety of malicious activities, from spam campaigns to coin-miners and credit card stealers.
Using some of the previous security issues as a means to gain unauthorized access to a website, attackers can then:
Our Web Application Firewall (WAF) and Intrusion Prevention System (IPS) helps mitigate many website threats.
A Distributed Denial of Service (DDoS) attack is a non-intrusive internet attack. It is made to take down the targeted website or slow it down by flooding the network, server or application with fake traffic.
DDoS attacks are threats that website owners must familiarize themselves with as they are a critical piece of the security landscape. When a DDoS attack targets a vulnerable resource-intensive endpoint, even a tiny amount of traffic is enough for the attack to be successful.
The Payment Card Industry Data Security Standards (PCI-DSS) outlines requirements for website owners with online stores. These requirements help ensure that you are properly securing the cardholder data you collect as an online store.
Under PCI DSS, cardholder data that must be secured refers to the full primary account number (PAN), but may also appear in the form of one of the following:
PCI compliance regulations apply regardless of whether you share data digitally, in written form, or speak to another individual with access to the data.
For ecommerce websites, it’s critical to do everything in your power to ensure that cardholder data passes from the browser to the web server by being properly encrypted via HTTPS. It should also be stored on the server securely and similarly encrypted when transmitted to any third-party payment processing services.
Hackers may try to steal or intercept cardholder data at any time, whether the data is at rest or in transit. Our PCI Compliance Guide and Checklist can help you walk through how to meet these requirements.
Regardless of the size of your business, developing a security framework can help reduce your overall risk.
The US National Institute of Standards and Technology (NIST) developed The Cybersecurity Framework which forms the basis of our website security principles framework in this guide.
Knowing security is a continuous process means it starting with the foundation of a website security framework. This framework will involve creating a “culture of security” where scheduled audits will help in keeping things simple and timely.
The five functions: Identify, Protect, Detect, Respond and Recover will be broken out in more detail along with actions to be applied.
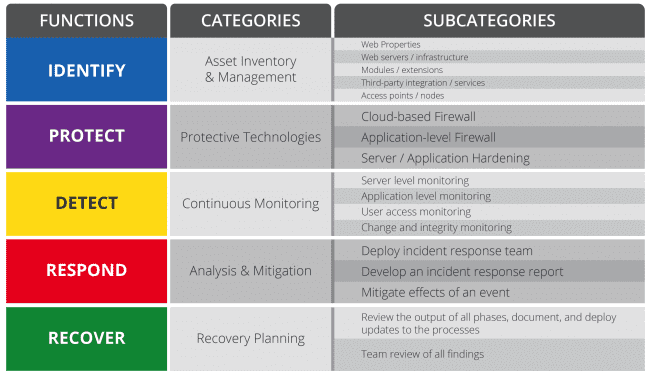
During this stage all asset inventory and management is documented and reviewed.
Asset inventory and management can be taken one step further into the following subcategories:
Once you have a list of your website assets, you can take steps to audit and defend each of them from attacks.
There are many reasons why having preventative web security measures in place is crucial, but where do you begin? These are known as protective technologies and layers of defense.
Sometimes these measures satisfy compliance requirements such as PCI, or make it easy to virtually patch and harden environments that are vulnerable to attack. Protection can also include employee training and access control policies.
One of the best ways to secure your website is by activating a web application firewall. Taking the time to think through security processes, tools, and configurations will impact your website security posture.
Continuous monitoring is a concept that refers to implementing tools to monitor your website (assets) and alert you to any issues.
Monitoring should be in place to verify the security state of:
You can also use security scanners and tools (such as SiteCheck) to scan for indicators of compromise or vulnerability.
Analysis and mitigation help to build out the response category. When there is an incident, there needs to be a response plan in place. Having a response plan prior to an incident of compromise will do wonders for the psyche.
A proper incident response plan includes:
During the remediation process, we never know beforehand what malware we are going to find. Some issues can spread quickly and infect other websites in shared server environments (cross-contamination).
The incident response process, as defined by NIST, is broken down into four broad phases:
Having a comprehensive preparation phase and a website security team you can count on is critical to the success of the mission.
In this phase, we make sure that we have all the necessary tools and resources before an incident occurs.
This goes hand in hand with the previous sections in the security framework.
Hosting companies play a crucial role in this phase by ensuring that systems, servers, and networks are sufficiently secure. It is also important to ensure your web developer or technical team is prepared to handle a security incident.
Although there are several methods of attack, we should be prepared to handle any incident. After hundreds of thousands of responses, we narrow down most of the infections to vulnerable components installed on the website (mostly plugins), password compromises (weak password, brute force) and others.
Depending on the issue and intent, the detection phase can be tricky. Some attackers are looking for fame, others may want to use resources or intercept sensitive information (credit card).
In some cases, there is no sign that a backdoor has been installed, waiting to be accessed by the attacker for malicious activities. Therefore, it’s highly recommended to implement mechanisms to ensure the integrity of your file system.
As for the “Containment, Eradication & Recovery” phase, the process has to adapt to the type of issue found on the website and predefined strategies based on the attack.
For instance, cryptominer infections usually consume lots of resources from the server (leecher), and before starting the remediation process the incident response team has to contain the threat. The containment of this attack is a critical step to prevent the depletion of additional resources and further damage.
This decision-making system and strategies are a crucial part of this phase. For instance, if we identify a particular file as being 100% malicious, there should be an action to wipe it out. If the file contains partially malicious code, only that piece should be removed. Each scenario should have a specific process.
Although there are several methods of attack, we should be prepared to handle any incident. After hundreds of thousands of responses, we narrow down most of the infections to vulnerable components installed on the website (mostly plugins), password compromises (weak password, brute force) and others.
Last but not least, the “Post Incident Activities” could also be called the “Lessons Learned” phase.
In this phase, the Incident Response Team should present a report detailing what occurred, what actions were taken, and how well intervention worked. We should reflect on the incident, learn from it, and take action to prevent similar issues in the future. These actions could be as simple as updating a component, changing passwords, or adding a website firewall to prevent attacks at the edge.
Conduct a review of the actions your department needs to take to continue fortifying your security posture. Next, ensure you take those actions as quickly as possible.
You can base all further actions on the following tips:
In addition, if you’re actively using a web application firewall (WAF), review your existing configuration to identify potential adjustments to be made.
Remember that even though WAFs help in meeting several Payment Card Industry Data Security Standards (PCI DSS), they are not a silver bullet solution. There are other factors that can impact your business, especially the human factor.
Recovery planning will happen when a complete review of all phases in the event of an incident takes place. Recover also relates to having a backup plan for situations in which all prior phases failed, for example, in the event of ransomware attacks.
This process should also include arranging time to speak with your security vendor on how to improve areas of weakness. They are better equipped to offer insight into what can be done.
If any data is at risk, notify your customers. This is particularly important if you’re a business operating in the EU where an organization must report a data breach within 72 hours, according to Article 33 of the General Data Protection Regulation (GDPR).
No matter what you do to secure your website, the risk will never be zero. If your website functionality is damaged, you need a way to recover the data quickly – not only one way, but at least two. It’s essential to have a local backup of the entire application and an external backup not directly connected to the application in case of a hardware failure or an attack.
The importance of website security cannot be overlooked. In this section, we will review how to secure and protect your website. This is not a step-by-step guide, but it will provide you with website security guidelines to find the right services for your needs.
Countless websites are compromised every day due to outdated and insecure software.
It is important to update your site as soon as a new plugin or CMS version is available. Those updates might just contain security enhancements or patch a vulnerability.
Most website attacks are automated. Bots are constantly scanning every site they can for any exploitation opportunities. It is no longer good enough to update once a month or even once a week because bots are very likely to find a vulnerability before you patch it.
This is why you should use a website firewall, which will virtually patch the security hole as soon as updates are released.
If you have a WordPress website, one plugin you should consider is WP Updates Notifier. It emails you to let you know when a plugin or WordPress core update is available.
Having a secure website depends a lot on your security posture. Have you ever thought of how the passwords you use can threaten your website security?
In order to clean up infected websites, remediators need to log into a client’s site or server using their admin user details. They might be surprised to see how insecure root passwords can be. With logins like admin/admin you might as well not have any password at all.
There are many lists of breached passwords online. Hackers will combine these with dictionary word lists to generate even larger lists of potential passwords. If the passwords you use are on one of those lists, it is just a matter of time before your site is compromised.
The best practices for you to have a strong password are:
Hosting many websites on a single server can seem ideal, especially if you have an ‘unlimited’ web hosting plan. Unfortunately, this is one of the worst security practices you could employ. Hosting many sites in the same location creates a very large attack surface.
You need to be aware that cross-site contamination is very common. It’s when a site is negatively affected by neighboring sites within the same server due to poor isolation on the server or account configuration.
For example, a server containing one site might have a single WordPress install with a theme and 10 plugins that can be potentially targeted by an attacker. If you host five sites on a single server now an attacker might have three WordPress installs, two Joomla installs, five themes and 50 plugins that can be potential targets. To make matters worse, once an attacker has found an exploit on one site, the infection can spread easily to other sites on the same server.
Not only can this result in all your sites being hacked at the same time, it also makes the cleanup process much more time consuming and difficult. The infected sites can continue to reinfect one another, causing an endless loop.
After the cleanup is successful, you now have a much larger task when it comes to resetting your passwords. Instead of just one site, you have a number of them. Every single password associated with every website on the server must be changed after the infection is gone.
This includes all of your CMS databases and File Transfer Protocol (FTP) users for every single one of those websites. If you skip this step, the websites could all be reinfected and you must restart the process.
Your website code may not be targeted by an attacker, but your users will be. Recording IP addresses and all activity history will be helpful in forensic analysis later.
A large increase in the number of registered users, for example, may indicate a failure in the registration process and allow spammers to flood your site with fake content.
The principle of least privilege centers around a principle that looks to accomplish two things:
Granting privileges to specific roles will dictate what they can and cannot do. In a perfect system, a role will stop anyone who tries to perform an action beyond what it’s designed for.
For example, let’s say an administrator is able to inject unfiltered HTML into posts or execute commands to install plugins. Is this a vulnerability? No, it’s a feature, based on one very important element – trust.
However, should an author have the same privileges and access? Consider separate roles based on trust, and lock down all accounts.
This only applies to sites that have multiple users or logins. It’s important that every user has the appropriate permission they require to do their job. If escalated permissions are needed momentarily, grant it. Then reduce it once the job is complete.
For example, if someone wants to write a guest blog post for you, make sure their account does not have full administrator privileges. The account should only be able to create new posts and edit their own posts because there is no need for them to be able to change website settings.
Having carefully defined user roles and access rules will limit any mistakes that can be made. It also reduces the fallout of compromised accounts and can protect against the damage done by rogue users.
This is a frequently overlooked part of user management: accountability and monitoring. If multiple people share a single user account and an unwanted change is made by that user, how do you find out which person on your team was responsible?
Once you have separate accounts for every user, you can keep an eye on their behavior by reviewing logs and knowing their usual tendencies, like when and where they normally access the website. This way, if a user logs in at an odd hour or from a suspicious location, you can investigate.
Keeping audit logs are vital to keeping on top of any suspicious change to your website. An audit log is a document that records the events in a website so you can spot anomalies and confirm with the person in charge that the account hasn’t been compromised.
Granted, it may be hard for some users to perform audit logs manually. If you have a WordPress website, you can use Sucuri’s free Security Plugin that can be downloaded from the official WordPress repository.
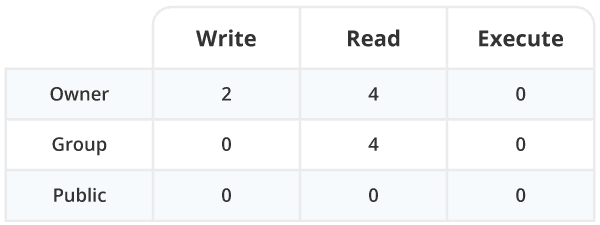
File permissions define who can do what to a file. Each file has three permissions available and each permission is represented by a number:
If you want to allow multiple permissions, simply add the numbers together, e.g. to allow read (4) and write (2) you set the user permission to 6. If you want to allow a user to read (4), write (2) and execute (1) then you set the user permission to 7.
There are also three user types:
So, if you want the owner to have read and write access, the group to have only-read access, and the public to have no access, the file permission settings should be:
Today’s CMS applications (although easy to use) can be tricky from a security perspective for the end users. By far the most common attacks against websites are entirely automated. Many of these attacks rely on users to have only default settings. This means that you can avoid a large number of attacks simply by changing the default settings when installing your CMS of choice.
For example, some CMS applications are writeable by the user – allowing a user to install whatever extensions they want.
There are settings you may want to adjust to control comments, users, and the visibility of your user information. The file permissions are another example of a default setting that can be hardened.
You can either change these default details when installing your CMS or later, but don’t forget to do it.
The CMS applications extensibility is something webmasters usually love, but it can also pose one of the biggest weaknesses. There are plugins, add-ons, and extensions that provide virtually any functionality you can imagine. But how do you know which one is safe to install?
Here are the things to look for when deciding which extensions to use:
In the event of a hack, website backups are crucial to recovering your website from a major security incident. Though it shouldn’t be considered a replacement for having a website security solution, a backup can help recover damaged files.
A good backup solution should fulfill the following requirements:
Get to know your web server configuration files: Apache web servers use the .htaccess file, Nginx servers use nginx.conf, Microsoft IIS servers use web.config.
Most often found in the root web directory, server configuration files are very powerful. They allow you to execute server rules, including directives that improve your website security. If you aren’t sure which web server you use, run your website through Sitecheck and click the Website Details tab.
Here are a few best practices to add for a particular web server:
SSL certificates are used to encrypt data in transit between the host (web server or firewall) and the client (web browser). This helps ensure that your information is sent to the right server and is not intercepted.
Some types of SSL certificates such as organization SSL or extended validation SSL add an additional layer of credibility because the visitor can see your organization’s details and know that you’re a legitimate entity.
As a website security company, it is our job to educate webmasters and to inform them that SSL certificates do not protect websites from attacks and hacks. SSL certificates encrypt data in transit, but do not add a protective layer to the website itself.
Monitor every step of the way to ensure the integrity of the application. Alerting mechanisms can improve the response time and damage control in the event of a breach. Without checks and scans, how will you know when your website has been compromised?
At least a month’s worth of logs can be quite useful to detect application malfunction. They will also show if a server is under a DDoS attack or facing unnecessary stress.
Record and regularly review all actions that occur in the critical parts of the application, especially (but not exclusively) in the administration areas. An attacker could try to exploit a less vital part of the site for a higher level of access later.
Be sure to create triggers to alert you in the event of a brute force attack or attempt to exploit any site features, including those unrelated to authentication systems.
It’s important to regularly check for updates and apply them to ensure you have the latest security patches. This is especially true if you do not to activate a web application firewall to block vulnerability exploitation attempts.
Securing your personal computer is an important task for website owners. Your devices can become an infection vector and cause your website to get hacked.
A good website security guide will mention scanning your computer for malware if your website has been hacked. Malware is known to jump from an infected user’s computer through text editors and FTP clients.
You should remove all unused programs from your computer. That step is important because these programs can also carry privacy issues, just like unused plugins and themes on your website.
If something isn’t installed, it can’t become an attack vector to infect your machine, especially browser extensions. They have full access to websites when webmasters are logged into their admin interfaces. The less you have installed in your computer the better.
If you aren’t sure of the purpose of a specific application, do some research online to confirm whether it is necessary or something you can remove. If you don’t intend to use it, remove it.
Using SSL certificates alone is not enough to prevent an attacker from accessing sensitive information. A vulnerability in your web application could allow the attacker to eavesdrop traffic, send a visitor to fake websites, display false information, hold a website hostage (ransomware) or wipe out all its data.
Even with a fully patched application, the attacker can also target your server or network using DDoS attacks to slow a website or take it down.
A web application firewall (WAF) is designed to prevent such attacks against websites and let you focus on your business.
Our website security service protects your site from vulnerable code, poor access controls, and server resource exploitation to ensure that it stays online and safe for site visitors. Let us secure your website so you can focus on what you do best.
Here are some free website security tools:
Here are some educational website security resources:
If you are looking for a website security partner, we would love to work with you.
Sucuri offers DDoS Protection, WAF, SSL Support & Monitoring with its Platform Plans.
Website security is vital to keeping a website online and safe for visitors. Without proper attention to website security, hackers can exploit your website, take it offline, and impact your online presence. The impacts of a hacked website can include financial loss, brand reputation issues, and poor search engine rankings.
The main security risks of a website include: vulnerable code, poor access controls, and server resource exploitation. For example, DDoS attacks can make a website unavailable to visitors in a matter of minutes. There are a lot of reasons why websites get hacked; a weak password or outdated plugin can lead to a hacked website.
A secure website has a web application firewall activated to prevent attacks and hacks. It also follows website security best practices and has no configuration issues or known vulnerabilities. You can use SiteCheck to see if a website has a firewall, any security anomalies, malware, or if it is blocklisted.SiteCheck to see if a website has a firewall, any security anomalies, malware, or if it is blocklisted.
Yes, absolutely. Website security is not included with most web hosting packages. The responsibility of securing a website is on the website owner. Security should be one of the first considerations when setting up a website, and an ongoing process of review. If a website is not secure, it can become a low-hanging fruit for cybercriminals.
You can secure your website by following website security best practices, such as:
For readers looking for the latest and trends, we’ve outlined the state of cybercrime and malware in our latest 2021 hacked website report. We dive into the number of websites compromised in 2021, explore the specific types of malware and vulnerabilities impacting our clients during cleanup and remediation efforts, and describe how you can mitigate risk to avoid infection.
Say on top emerging website security threats with our helpful guides, email, courses, and blog content.