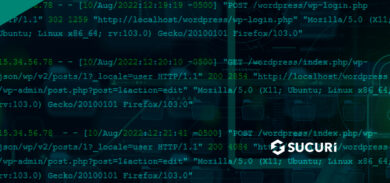
It’s quite common for attackers to compromise your website and make use of it for their phishing campaigns. The most typical method they use is to simply place redirects throughout your site or simply upload entire phishing folders so that your website becomes an actual phishing platform.
When the hosting finds any bad content there they usually take the swiftest action and just suspend the website account until the matter is resolved. But what if the compromise started at a different level? Let’s say, the server’s error documents?
Recently, we came across a very similar situation. The curious point is that the attackers predicted the domains would eventually be suspended so they promptly changed the template for suspended websites directly through the WHM panel.
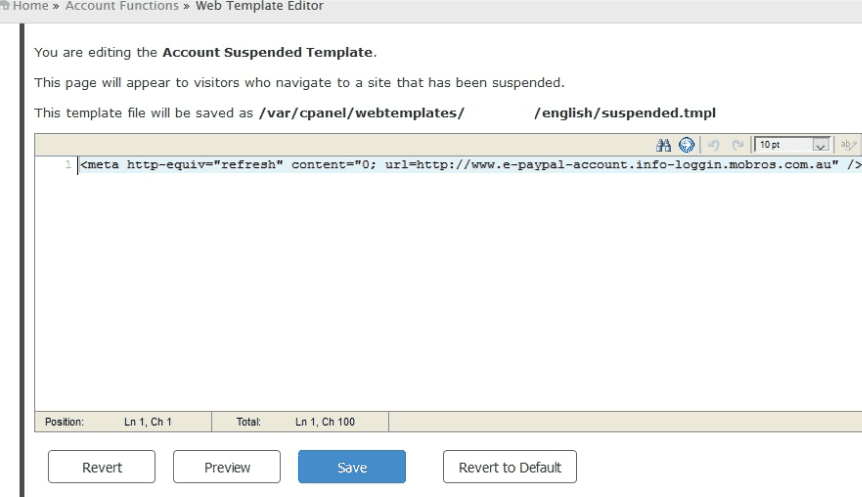
Even though the website was suspended and its content inaccessible, infecting the suspended template enabled the redirect to the phishing domain.
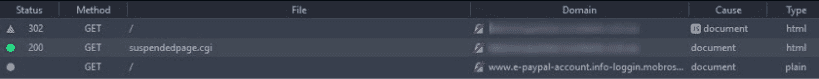
These phishing campaigns impact directly on a website’s reputation and can easily lead to blacklists and great drops in your SEO rankings.
Website suspension may not always be enough to fix issues resulted from a compromise, especially when the compromise happens directly on your hosting provider and the attacker has access to your cPanel / WHM.
Once a compromise is detected, we always recommend changing all passwords (database, back-end interfaces, cPanel, FTP/SFTP), keeping regular backups to restore the website to a clean state, and reduce the impacts on your business by adding a File Integrity Monitoring System and a Website Firewall to prevent attacks.