Just over a week ago, WordPress released version 4.7.3 to patch multiple security issues. Despite the automatic update feature provided by many hosting companies, there are still many WordPress websites that have not been updated. In fact, we are seeing quite a few sites that are still using versions 4.7 and 4.7.1, which are vulnerable to the WordPress REST API vulnerability patched in early February (version 4.7.2). This more serious vulnerability allows attackers to create, delete, and modify posts on vulnerable websites without authorization.
Quite soon after the original REST API vulnerability disclosure, after many hosts and firewalls had auto-updated their client sites to version 4.7.2, various hacker groups began to exploit the REST API to create defacement campaigns.
There is a new wave of SEO spam campaigns using this vulnerability, not only create spam posts, but to replace existing post content with spam keywords and links.
Dating Spam Campaign
Back then we predicted that defacements were just the beginning. After those highly visible and immediate attacks, we started to discover that SEO spammers were exploiting the same vulnerability to manipulate search engine results.
Indeed, by the end of February, we identified around 300 WordPress blogs that had compromised posts full of links using Swedish and Italian anchor text

Each spam post on an infected site contains around 200 links to 100 unique websites. These hacker-controlled sites are doorway pages that link off to the “money sites” which offer affiliate commissions. This blackhat SEO technique is known as a private blog network (PBN).
Half the links contain only the URLs of the doorways sites, while the rest have optimized anchor text in either Swedish or Italian, e.g. “kostnadsfria dejtingsajter gratis” (free dating sites).
All the doorway sites have pretty exotic top-level domains:
- .cf (Central African Republic)
- .ga (Gabon)
- .gq (Equatorial Guinea)
- .tk (Tokelau)
They also chose pretty random domain names, such as:
- ajformedling[.]cf
- confidentliving[.]gq,
- jaubil[.]cf
- nikesoccerbodotoutlet[.]tk
- wing-tsun[.]gq, etc.
You can find the whole list of the domains here. These domains were registered for free via the Freenom service.
Cloning Popular Legitimate Sites
These doorway sites copy the templates from popular Swedish and Italian sites and use these to build their spam sites while replacing all links on the page with dating-related keywords.
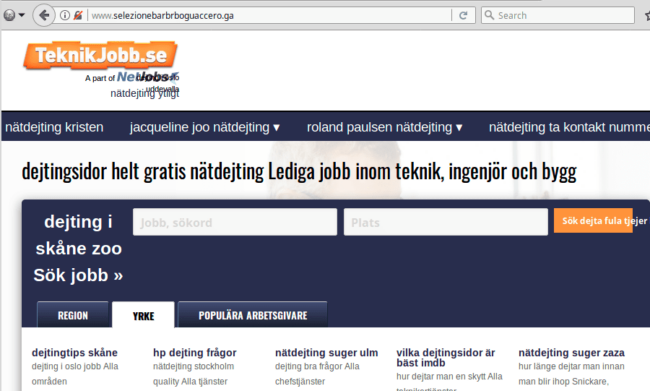
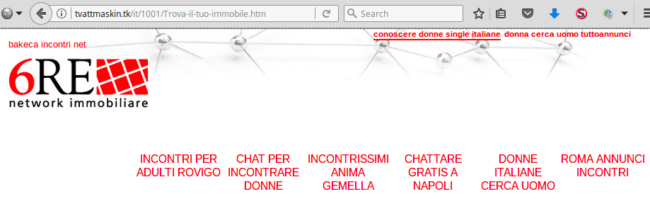
It looks like in addition to free domain names, the spammers also abuse the free Cloudflare plan to hide their server (I doubt they pay $2,000/month for their 100 domains).
The real location of the doorway sites is hidden by the Cloudflare firewall. However, it is clear that they all share the same server. Cloudflare reported “Gateway time-out” errors for all of them at the same time and they all came back online shortly after.
WordPress REST API Security Hole
At this point, we can see that someone creates similar posts with spammy “dating” links on multiple sites. But can we be sure that the recently patched WordPress REST API vulnerability was exploited in all these cases?
This may not be the first thing you suspect when you check the creation dates of the spam posts. For example, on the screenshot above of a spam post, notice the date: February 24, 2016. That’s more than 9 months before the release of WordPress 4.7 (the first WordPress version with that bug) and almost a year before the disclosure of the vulnerability. Moreover, on some other sites, the dates of the spam posts are as old as 2011!
So what makes us think that this security hole, which only existed in WordPress versions 4.7 and 4.7.1, is to blame? Here’s what we found during our investigation.
Versions of Infected Sites
A month after the release of WordPress 4.7.2, all the affected sites still use WordPress 4.7 or 4.7.1. None of them used any older versions.
WHOIS
There is no WHOIS information about those 100 doorway domains used in this black hat SEO campaign before 2017.
Backlinks
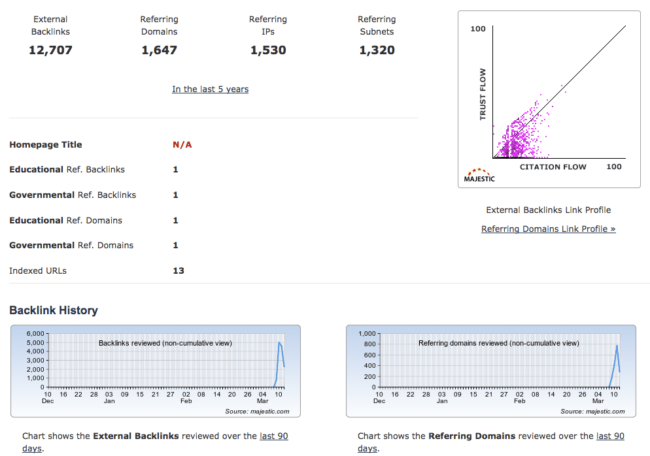
When we check backlink profiles for those 100 doorway domains on Majestic Site Explorer, we get pretty much the same picture:
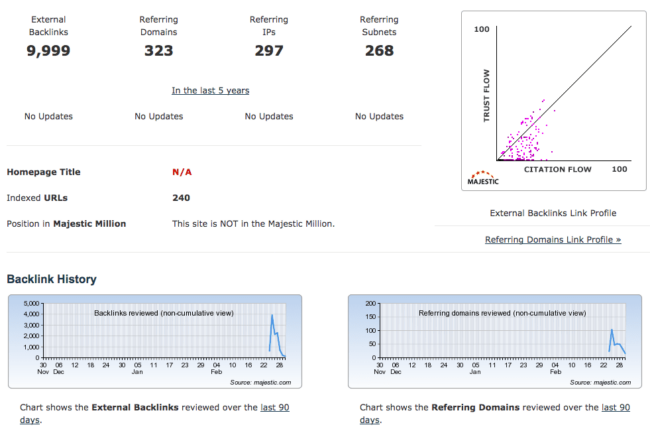
You can see that the Majestic crawler began to find links to the doorway site only after February 23rd, 2017, which is more than 3 weeks after the vulnerability disclosure.
Replacing Existing Post Content
The vulnerability in the REST API allows attackers to create posts with arbitrary publish dates, but it’s not the case here. The attackers opted instead to use the vulnerability to update the content of older, existing posts.
We noticed these posts still had legitimate titles related to the original website. When we checked cached versions of these posts on the Archive.org WayBack Machine, we saw that before February those posts had legitimate content as well. This means the attackers preferred to replace the content of existing, legitimate posts.
Streaming and Download Scam Campaign Emerges
We had been investigating the dating site spam for some time already. On March 7th, we noticed a new black hat SEO campaign exploiting the same vulnerability. This time the attackers replaced entire posts, including the titles, to promote “Watch Movie Online Streaming & Download” scams.
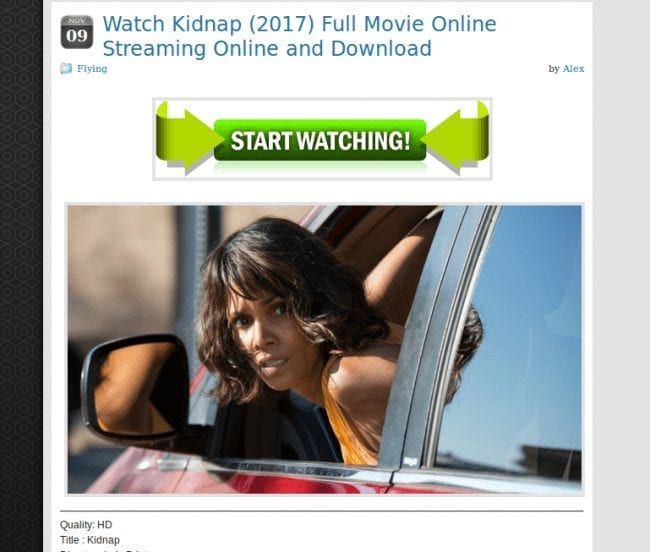
The hijacked posts have titles that follow this pattern:
“Watch <movie_name> (2017) Movie Online Streaming & Download”.
The content of the post usually consists of a screenshot, movie facts, and download links and buttons pointing to fake movie sites. The fake sites don’t contain movies at all. There are screenshots and a scripted animation that makes it appear as if the stream is loading, along with a background sound from an invisible YouTube iframe. After a few seconds, a pop-up requires the visitor to login before they can continue watching the movie.
This fake login prompt redirects visitors through an affiliate link to deceitful paid sites such as
- geeker[.]com
- filmlush[.]com
- watch.vid-id[.]me
- videostripe[.]com
- boinkplay[.]com, etc.
Here’s the [incomplete] list of the fake movie sites used in this campaign.
- cheiomovie[.]com
- filmerfilm[.]com
- films212[.]com
- firimu[.]com
- ganzermovie[.]com
- movieadrenaline[.]com
- movieclose[.]com
- moviecrot[.]ml
- moviedungeons[.]com
- moviefake[.]com
- movgames[.]com
- moviekw[.]com
- moviesci-fi[.]com
- moviewestern[.]com
- plnemovie[.]com
- punimovie[.]com
- sinemanews[.]com
- sinimanews[.]com
- vollmovie[.]com
Most of these domains have been registered less than a month ago (some even just last week) specifically for this campaign.
Like with the Swedish dating spam attack, these fake movie sites hide their server location behind the Cloudflare firewall.
Backlink analysis from Majestic shows that the “Watch Movie Online Streaming & Download” campaign began around March 7th. We can also see that it’s already infected 1,600+ domains (mainly WordPress 4.7 and 4.7.1 sites)
In addition, Google shows 1000+ results when using search operators to identify hacked sites matching the following pattern: [intitle:“2017 Full Movie Online Streaming Online and Download“]
Conclusion
As we predicted, black hat SEOs didn’t miss the opportunity to abuse out-of-date WordPress blogs with the REST API vulnerability. SEO spam is one of the more common infections we deal with on a daily basis.
The attack that we currently see in the wild does more harm to compromised sites than typical SEO spam hacks. Instead of just injecting invisible links or new spam pages, attackers remove legitimate site content and replace it with spam. When hackers replace existing posts, they do double damage: the legitimate posts (often many hours of work) are now gone, and reputation issues arise when site visitors see the spam (it is not hidden).
Update and Monitor Your Sites
Despite the prominent nature of this hack, many of the compromised sites are not being cleaned for weeks. This leads us to believe that these website owners probably don’t open their sites often and are likely unaware they’ve been hacked. In these situations, it’s wise to have automated website security monitoring to alert you when there have been content changes.
These attacks against unpatched sites prove the importance of timely updates of websites software. The longer a site stays unpatched after the release of a security patch and the disclosure of the vulnerability the higher the risks of being hacked.
Firewall Protection and Backups
If for some reason you can’t update your site automatically in the event of a security patch release, you might want to use a Web Application Firewall (WAF) to virtually patch your site against known and emerging attacks.
When we discovered the WordPress REST API vulnerability, Sucuri worked closely with the WordPress Security Team to notify all major hosting companies that provide automatic updates to their customers. We also helped other reputable WAF providers to prepare virtual patches and protect vulnerable websites. Due to this coordinated effort, the scale of this campaign was significantly limited and many sites were never in danger of this attack.
It’s also important to have reliable backups of your sites. In this case, hackers simply removed legitimate blog posts. While it is easy to delete the spammy posts, it will not restore their original content. Only a backup can help you in such a situation. Alternatively, it’s possible to restore post content if your blog is configured (default setting) to save revisions, however, some webmasters turn revision control off to improve performance and save some database space.
For more information on cleaning and protecting WordPress sites, read our step-by-step guide here.






![Massive ois[.]is Black Hat Redirect Malware Campaign Targets WordPress Sites](https://blog.sucuri.net/wp-content/uploads/2022/11/BlogPost_Feature-Image_1490x700_PHP-Login-Stealer-390x183.png)
