PHP web shells are a type of backdoor which, when left on compromised websites, allow attackers to maintain unauthorized access after initial compromise.
To further evade detection, attackers may also choose to keep a packer script on a compromised website instead of the actual PHP web shell. They can then use this script to generate the PHP web shell on an as-needed basis.
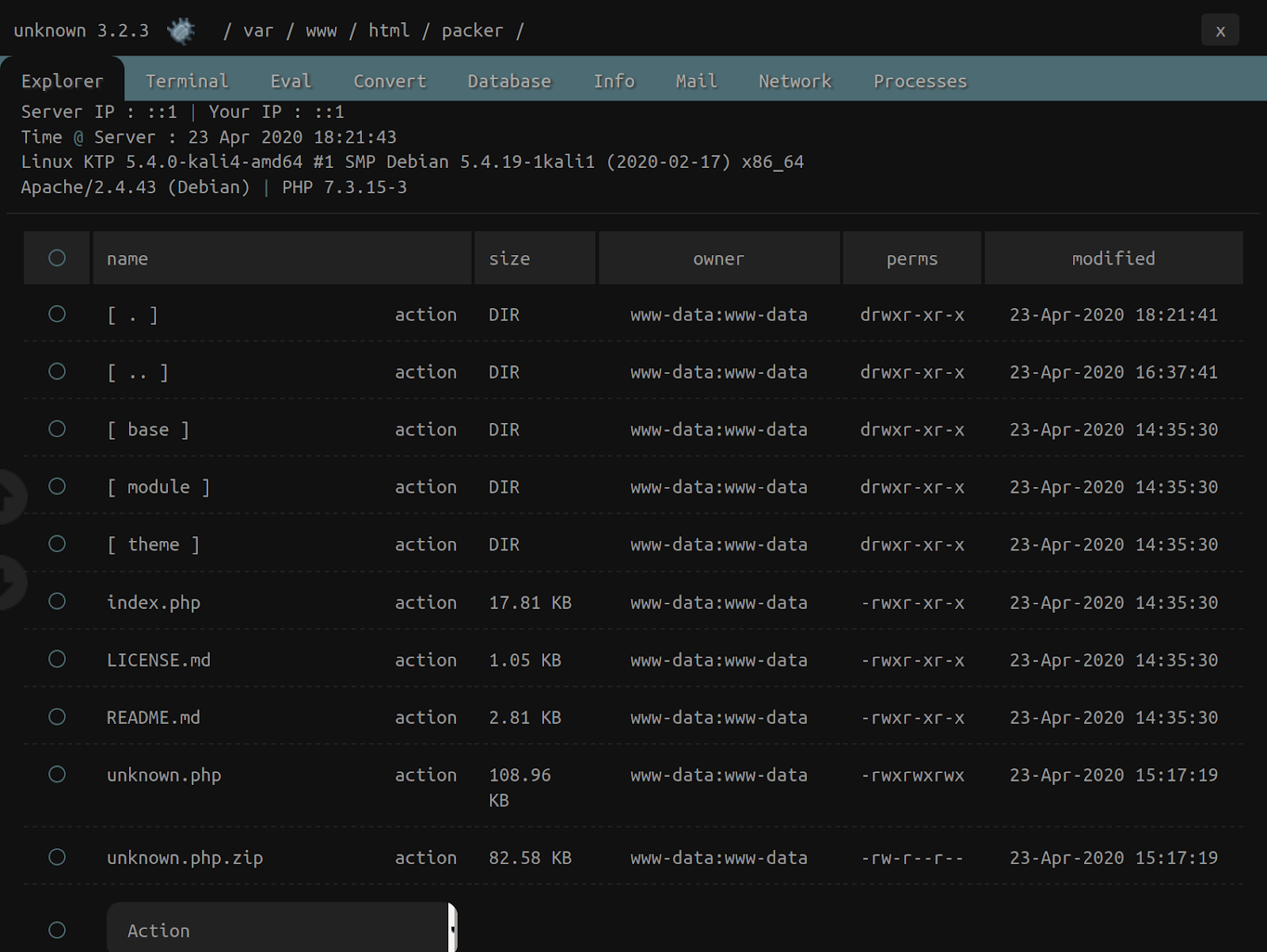
One of the more common PHP web shells is b374k.php. It’s popular with bad actors because it offers a lot of features including a file manager, database connect, various text conversions, and email via PHP.
Let’s take a look at how attackers can load b374k.php with a packing script, seen below.
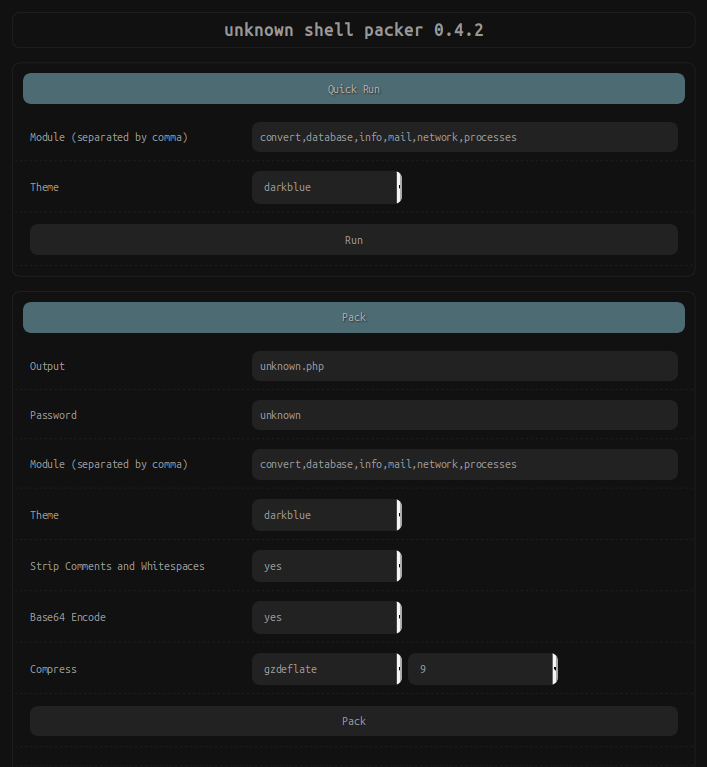
This unknown shell packer offers a few different options to the attacker:
- Output – Defines the filename of the PHP web shell to be created
- Password – Sets a password used to limit access to the PHP web shell
- Module – Optional features that can be enabled: convert, database, info, mail, network, processes
- Theme – Optional color theme
- Strip Comments and Whitespaces – Removes unneeded code comments and whitespaces
- Base64 Encode – encodes the PHP web shell’s code with base64
- Compress – Compresses the PHP code with various PHP functions like gzdeflate, gzencode, gzcompress. This feature requires the code to have already been base64 encoded.
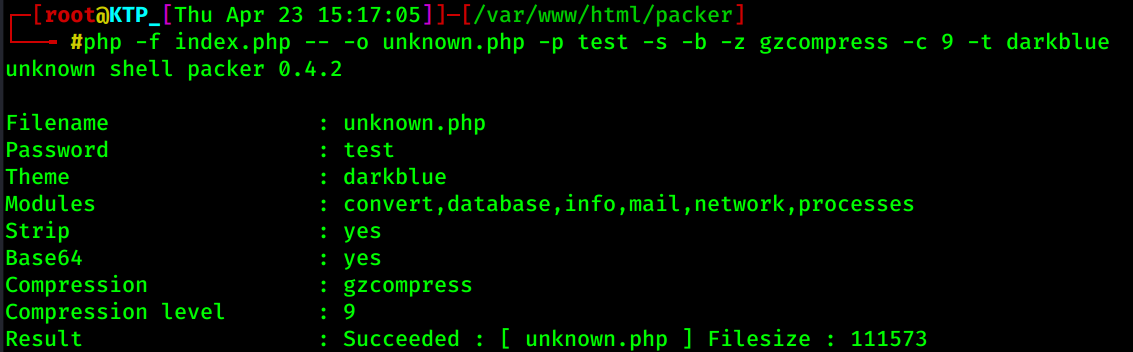
Attackers can also run the packer by submitting the parameters through PHP CLI, if available.
Regardless of whether the attacker opts for the PHP CLI or the browser GUI, the result is a generated PHP shell with the chosen filename — in this case unknown.php — which is dropped in the current directory.
These types of malicious scripts can be found planted anywhere within a website’s environment, so the best way to mitigate threat is to prevent unauthorized access to your website in the first place. Practice strong password security principles and use a firewall to prevent a password from brute force.