In the last few months, we’ve covered several cases of SEO Spam in our labs and blog that were promoting products and services ranging from essay writing to sunglasses. From time to time, these Spam campaigns change and attackers focus on topics that may bring additional revenue. This time around, the topic was Soccer 🙂
During an Incident Response process, we found several files on the website’s root folder that had nothing to do with the actual website content. Those files had PHP extensions and their filenames were either just numbers, e.g.: 1.php, 2.php, 5.php, … or soccer team names; for instance, Real-Madrid.php, Barcelona.php, Chelsea.php, etc.
When accessing those files on a browser, we see an attempt to impersonate a Swedish online store, as you can see in the following screenshots:
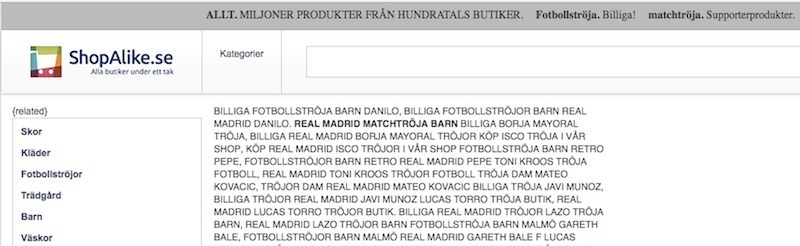
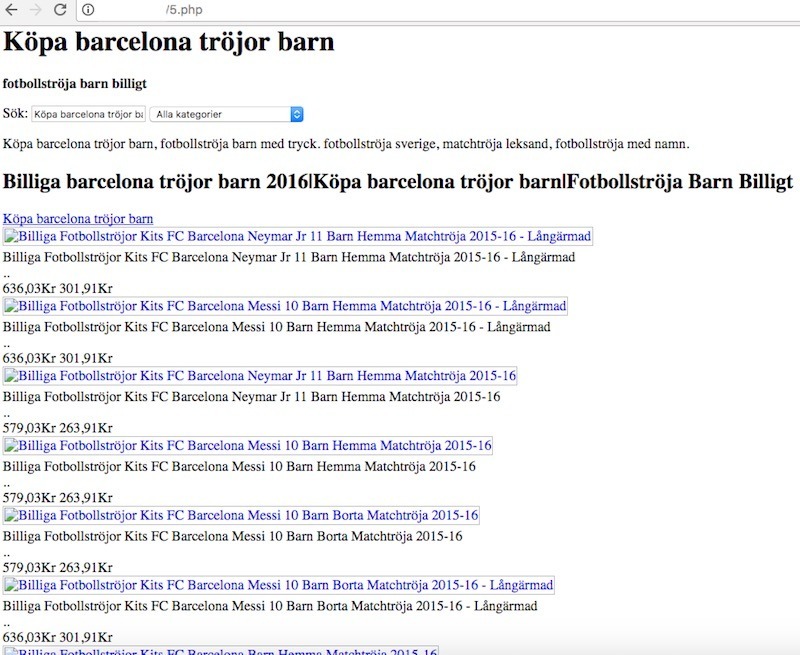
In addition to that, there’s a hidden iframe being loaded at the bottom pointing to hxxp://www[.]fabriksforsaljning[.]com (doesn’t seem to exist anymore).
Remember that removing the offending files will not prevent your site to be attacked and infected again, since those files were uploaded using a backdoor or stolen/leaked credentials to your site. Check your access logs and ftp logs for any strange activity. This will help identifying any malicious code used to upload those files. Also, if you need professional security assistance to clean up your website, let us know.










