Last year we spoke about the siteurlpath blackhat SEO attack that was infecting many WordPress sites with spam.
But, how many? We had no clue at the time. Today, we decided to check on Google and it seems that almost 50k (yes, fifty thousand sites) were compromised, at minimum…
How do we know this? Well, the attack consists of contacting the domain wplinksforwork.com to get a list of links to be displayed on the compromised sites. However, that domain has been down for the last few days and all the sites compromised (if they have display errors enabled), have this message in their footer:
Warning: file_get_contents(http://wplinksforwork.com/56132.. 47509328/p.php?host=… failed to open stream: php_network_getaddresses: getaddrinfo failed: Name or service not known in ..
So we checked on Google to see how many they have found lately with this error and it is an astonishing number of almost 50k pages:
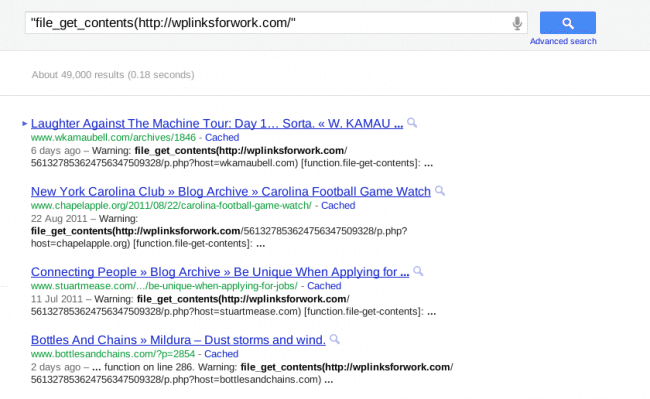
This only include sites that Google crawled recently AND have PHP display errors turned on. So the number is very likely much higher than that.
How were these sites compromised?
At the time of our first analysis, most of the hacked sites had outdated versions of WordPress installed. Some of them were not, but we assume they upgraded after the fact, and never cleaned up the spam from their themes (yes, it hides in themes and in the database).
So, if you keep WordPress updated, you’re likely safe. In any case, you can check via our free scanner to verify: http://sitecheck.sucuri.net
As always, remember to keep your sites updated. If you need help, let us know.