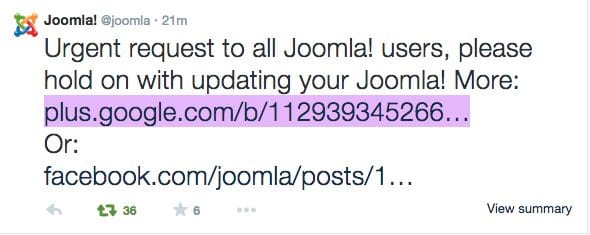
Update: It seems like there is a glitch in the new version and the Joomla team is urging its users not to upgrade yet. From their Twitter:
Original post:
The Joomla team just released versions 3.3.5, 3.2.6 and 2.5.26, patching high priority security issues. The first one is an Remote File Include (RFI) vulnerability and the second one is a Denial of Service (DoS) vulnerability that affect all previous versions. If you are using Joomla, stop what you are doing and update it now!
The good news for our clients and what’s very exciting for us, me especially, is to see how the virtual hardening on our CloudProxy Website firewall protected our clients automatically against this vulnerability. As our researchers started to analyze the disclosure, we quickly noticed that it was already covered and the URL used to trigger this bug was already blocked by default. It means that our clients got zero-day protection without anyone even knowing about this issue.
For more information on these vulnerabilities, you can get straight from the Joomla! release notes:
High Priority – Core – Remote File Inclusion:
Project: Joomla!
SubProject: CMS
Severity: Moderate
Versions: 2.5.4 through 2.5.25, 3.2.5 and earlier 3.x versions, 3.3.0 through 3.3.4
Exploit type: Remote File Inclusion
Reported Date: 2014-September-24
Fixed Date: 2014-September-30
CVE Number: CVE-2014-7228Inadequate checking allowed the potential for remote files to be executed.
This issue was discovered by Johannes Dahse and disclosed to Akeeba (and Joomla). The Akeeba team released a good post explaining the issue. We recommend reading if you are interested in the technical details.
Medium Priority – Core – Denial of Service:
Project: Joomla!
SubProject: CMS
Severity: Low
Versions: 2.5.4 through 2.5.25, 3.2.5 and earlier 3.x versions, 3.3.0 through 3.3.4
Exploit type: Denial of Service
Reported Date: 2014-September-24
Fixed Date: 2014-September-30
CVE Number: CVE-2014-7229Inadequate checking allowed the potential for a denial of service attack.
Again, if you are using the Joomla! we highly recommend updating immediately.