Social engineering techniques, like phishing, can be powerful in persuading users into performing specific actions or disclosing confidential information. In these types of scenarios, attackers look for vulnerable sites on the web to upload fake pages pretending to be trustworthy organizations, such as banks, email and payment services, etc.
During an incident response process, we identified a phishing directory called “login-apple-account” on the website’s root. When accessing the path via HTTP, a very well structured fake version of the Apple ID website would be displayed:
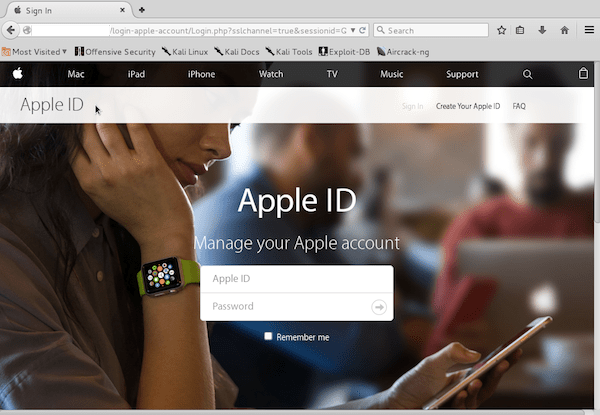
Although at first it may seem just a regular phishing attempt, the page would be displayed only to a very specific set of visitors.
This conditional attack implemented several evasion techniques to prevent access from different IP ranges, and in some cases, redirecting search engines, antivirus and anti-phishing companies to the official Apple ID website through raw header() calls:
header("Location: hXXps://www[.]google[.]ca/url?sa=t&rct=j&q=&esrc=s&source=web&cd=1&cad=rja&uact=8&ved=0ahUKEwi_yey8kvzJAhWwj4MKHVp5ALcQFggcMAA&url=hXXps%3A%2F%2Fappleid[.]apple[.]com%2F&usg=AFQjCNF7841Jq5PLrYJwYDN8RkcZjuNVww");For instance, the “login-apple-account/assets/includes/netcraft_check.php” file prevents the malicious page to be accessed if the user-agent matches Netcraft, an anti-phishing company, redirecting it to a Google search result page:
<?phpif ($v_agent == "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; .NET CLR 2.0.50727)") { header("Location: hXXps://www[.]google[.]ca/url?sa=t&rct=j&q=&esrc=s&source=web&cd=1&cad=;uact=8&ved=0ahUKEwi_yey8kvzJAhWwj4MKHVp5ALcQFggcMAA&url=hXXps%3A%2F%2Fappleid[.]apple[.]com%2F&usg=AFQjCNF7841Jq5PLrYJwYDN8RkcZjuNVww");die();}?>Other files refer to the “login-apple-account/assets/includes/blacklist.dat”, which has quite a big list of IP ranges from several services, to prevent them from accessing the phishing page:
# NETCRAFT IP RANGES194.52.68.0-194.52.68.255194.72.238.0-194.72.238.25583.138.182.72-83.138.182.7983.138.189.96-83.138.189.10381.91.240.0-81.91.255.25589.36.24.0-89.36.31.25583.222.232.216-83.222.232.218184.172.0.0-184.173.255.255# KASPERSKY IP RANGES...
There were also several other AntiVirus and AntiPhishing companies’ IPs listed in that file so the phishing page would go unnoticed during a regular website crawl, therefore preventing the phishing URL to get into blacklists.
Even though it tries to hide itself via HTTP, it cannot stop a server-side scan, so our server-side scanner is able to detect and alert you asap about such phishing pages. If you’re looking for a security solution that helps you avoid such issues, let us know.